Exam 3: Security Through Authentication and Encryption
Exam 1: Operating Systems Security: Keeping Computers and Networks Secure86 Questions
Exam 2: Viruses, Worms, and Malicious Software86 Questions
Exam 3: Security Through Authentication and Encryption86 Questions
Exam 4: Account-Based Security86 Questions
Exam 6: Firewalls and Border Security86 Questions
Exam 7: Physical and Network Topology Security86 Questions
Exam 8: Wireless Security86 Questions
Exam 9: Web, Remote Access, and VPN Security86 Questions
Exam 10: E-Mail Security86 Questions
Exam 11: Security Through Disaster Recovery86 Questions
Exam 12: Security Through Monitoring and Auditing86 Questions
Select questions type
The public key/private key method uses an encryption algorithm developed by Joan Daemen and Vincent Rijmen.
(True/False)
4.9/5  (27)
(27)
Did the original version of DES use a 56-bit encryption key combined with 8-bit parity?
(True/False)
5.0/5  (31)
(31)
In Windows 2000 and Windows 2003, a computer that is configured to use IPSec communication can function in three roles. What are they?
(Essay)
4.8/5  (28)
(28)
The purpose of EFS is to protect folder and file contents on a hard disk, in case a hard disk is stolen from a server or workstation, or a portable computer is lost or stolen.
(True/False)
4.8/5  (37)
(37)
____________________ encryption can work well on a computer for files that are only accessed by an authorized account, but it is difficult to achieve secrecy over a network using this method.
(Short Answer)
4.8/5  (33)
(33)
What encryption method is often used to create a digital signature?
(Multiple Choice)
4.8/5  (29)
(29)
Does Microsoft's MPPE use a 40-bit RSA encryption key for its basic encryption?
(True/False)
4.8/5  (30)
(30)
A random generator starts with a base or seed number and generates the same sequence of random numbers time after time.
(True/False)
4.8/5  (40)
(40)
_____ authentication works by giving each frame or packet an identification or sequence number. This ensures the accuracy of ongoing communications and the authenticity of the communications source.
(Multiple Choice)
4.9/5  (38)
(38)
The ____________________ field in the ESP is used in the same way as in the AH, to store the Integrity Check Value.
(Short Answer)
4.8/5  (31)
(31)
____________________ authentication method is an application-independent form of authentication that is modeled after SSL and uses RSA encryption.
(Short Answer)
4.9/5  (41)
(41)
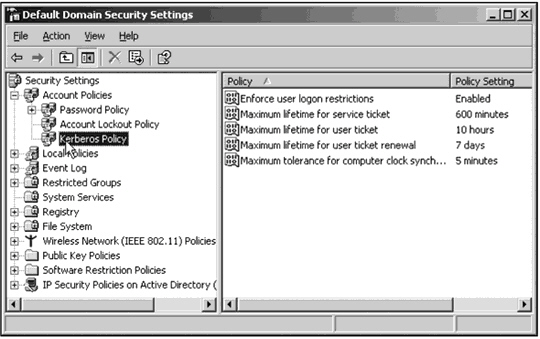 Which option in the figure above turns Kerberos encryption on and off?
Which option in the figure above turns Kerberos encryption on and off?
(Multiple Choice)
4.8/5  (35)
(35)
Which authentication method is a physical device that enables the generation of a unique password each time a user logs on to a server or network?
(Multiple Choice)
4.9/5  (33)
(33)
In session authentication, is each packet given a sequence number when it is constructed at the source computer?
(True/False)
4.8/5  (36)
(36)
When the hashing method of encryption is used, each password has a unique digital signature.
(True/False)
4.7/5  (37)
(37)
Which of the following encryption techniques is employed in UNIX/Linux systems to enable encryption in file systems, using DES, 3DES, and other encryption techniques?
(Multiple Choice)
4.8/5  (27)
(27)
Deploying _________________________ with NAT can interfere with the security established by IPSec.
(Short Answer)
4.8/5  (32)
(32)
Showing 41 - 60 of 86
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)