Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
What Business Readiness Rating (BRR) category does the subcategory "User Audit Trail" belong to?
(Multiple Choice)
5.0/5  (24)
(24)
What module should an administrator use to view all activities in cloud applications?
(Multiple Choice)
4.9/5  (43)
(43)
What action should an administrator take if a cloud application has significant risks, but mitigating controls are available?
(Multiple Choice)
4.8/5  (39)
(39)
What type of connection should an administrator use when the network is sensitive to the bandwidth consumed by log traffic transfer to CloudSOC?
(Multiple Choice)
4.8/5  (41)
(41)
How should an administrator handle a cloud application that is business critical, but is NOT the most secure option?
(Multiple Choice)
4.8/5  (36)
(36)
By default, HTTP traffic that is logged is recorded to which log facility?
(Multiple Choice)
4.7/5  (35)
(35)
What compensatory control should an administrator implement if password quality rules of a cloud application has a low rating?
(Multiple Choice)
4.8/5  (29)
(29)
Which Symantec product is best suited for simultaneously administering a large number of ProxySG appliances?
(Multiple Choice)
4.9/5  (40)
(40)
Where should an administrator locate unshared content within the Securlet module that contains risky information?
(Multiple Choice)
4.9/5  (24)
(24)
What module requires administrative rights to make connections to cloud applications?
(Multiple Choice)
4.8/5  (34)
(34)
What Rule Type in ContentIQ profiles do FERPA, GLBA, HIPAA, PCI AND PII belong to?
(Multiple Choice)
4.8/5  (32)
(32)
Where does ProxySG object caching usually result in the most bandwidth savings?
(Multiple Choice)
4.8/5  (36)
(36)
Refer to the exhibit. What modules are used in the use case "Protect information from accidental and intentional exposure within cloud applications"? 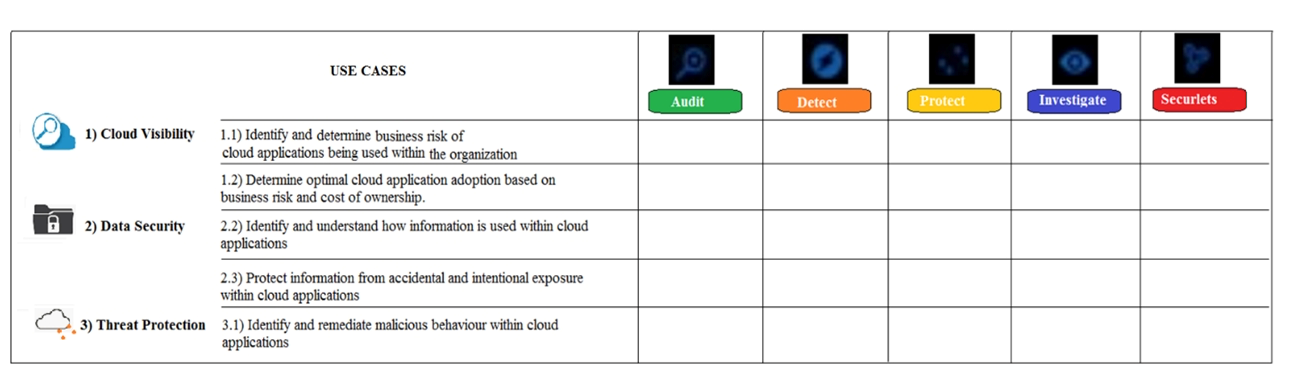
(Multiple Choice)
4.9/5  (48)
(48)
What rules in a VPM layer are being evaluated, what causes evaluation to stop and proceed to the next layer?
(Multiple Choice)
4.7/5  (41)
(41)
If you lose the password to the setup console, which of these methods can be used to regain access to the setup console? (Choose three.)
(Multiple Choice)
4.7/5  (31)
(31)
The ProxySG simultaneously opens multiple server connections to retrieve objects referenced on a web page before the client actually issues the requests for those objects. This statement best describes which ProxySG caching technique?
(Multiple Choice)
4.9/5  (37)
(37)
What CloudSOC module should an administrator use to identify and remediate malicious behavior within cloud applications?
(Multiple Choice)
4.7/5  (33)
(33)
What policy should an administrator utilize to allow users access to Office 365, but prevent the extraction of files when their ThreatScore is higher than 30?
(Multiple Choice)
4.9/5  (39)
(39)
Showing 41 - 60 of 98
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)