Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
What type of policy should an administrator utilize to prevent the spread of malware through cloud applications?
(Multiple Choice)
4.8/5  (46)
(46)
If you have configured continuous uploading of access logs and the ProxySG is unable to reach the upload destination, what happens to the log entries?
(Multiple Choice)
4.8/5  (24)
(24)
Which services are included in the Intelligence Services Advanced Bundle?
(Multiple Choice)
4.9/5  (39)
(39)
What module can an administrator use to connect certain cloud applications to CloudSOC via APIs, and have complete visibility into the content being shared in those cloud applications?
(Multiple Choice)
4.9/5  (35)
(35)
Why is authentication using Basic credentials typically used over HTTPS?
(Multiple Choice)
4.9/5  (32)
(32)
What type of solution should an administrator implement to secure the way users interact with cloud applications?
(Multiple Choice)
4.8/5  (35)
(35)
Which deployment method represents a single point of failure?
(Multiple Choice)
4.9/5  (47)
(47)
Refer to the exhibit. An administrator found this incident in the Investigate module. What type of policy should an administrator create to get email notifications if the incident happens again? 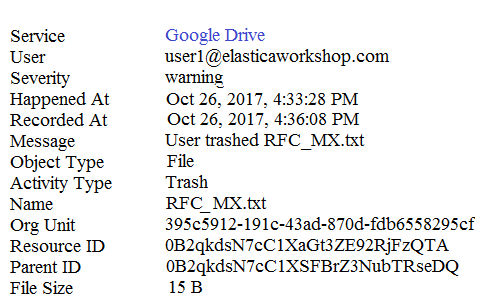
(Multiple Choice)
4.8/5  (37)
(37)
In which client connection type are user agents aware that a proxy has been deployed?
(Multiple Choice)
4.7/5  (40)
(40)
In the Management Console, how can you determine the serial number of the ProxySG?
(Multiple Choice)
4.7/5  (44)
(44)
Which detector will trigger if CloudSOC detects anomalously frequent sharing?
(Multiple Choice)
4.9/5  (47)
(47)
How should an administrator handle a cloud application that fails to meet compliance requirements, but the business need outweighs the risk?
(Multiple Choice)
4.8/5  (30)
(30)
Refer to the exhibit. Which module(s) are utilized in the use case "Identify and understand how information is used within cloud applications"? 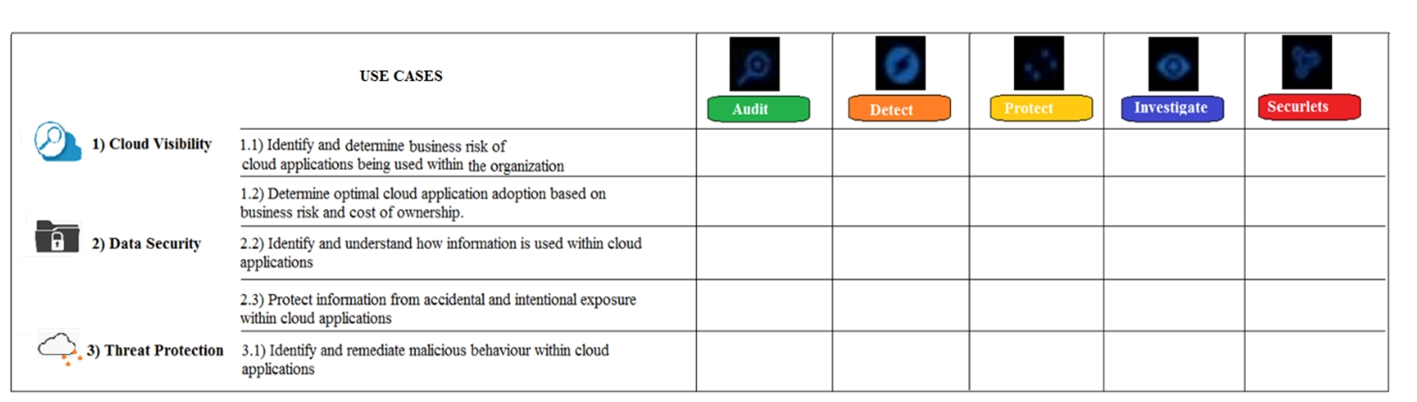
(Multiple Choice)
4.9/5  (46)
(46)
Name three methods by which client configuration can be performed in an explicit ProxySG deployment.
(Multiple Choice)
4.9/5  (34)
(34)
Showing 21 - 40 of 98
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)