Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
Refer to the exhibit. What action should an administrator take if this incident was found in the Investigate module? 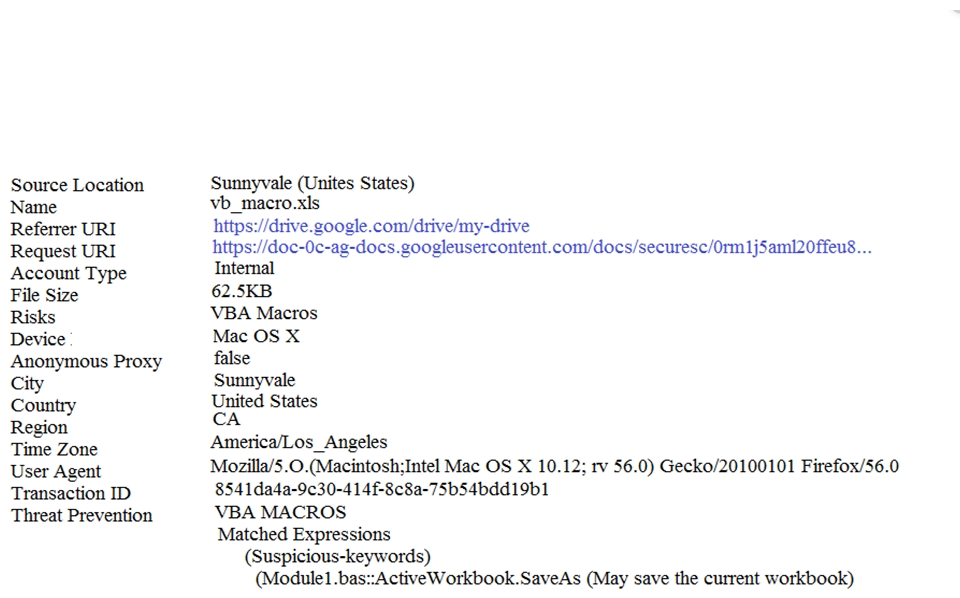
(Multiple Choice)
4.8/5  (31)
(31)
What type of policy should an administrator use to prevent a user that is behaving in anomalous ways from sharing public links while you monitor them?
(Multiple Choice)
4.9/5  (43)
(43)
What Rule Type in ContentIQ profiles do business, computing, encryption, engineering, health, and legal belong to?
(Multiple Choice)
4.8/5  (44)
(44)
Refer to the exhibit. Which module(s) use the CloudSOC gateway as a data source? 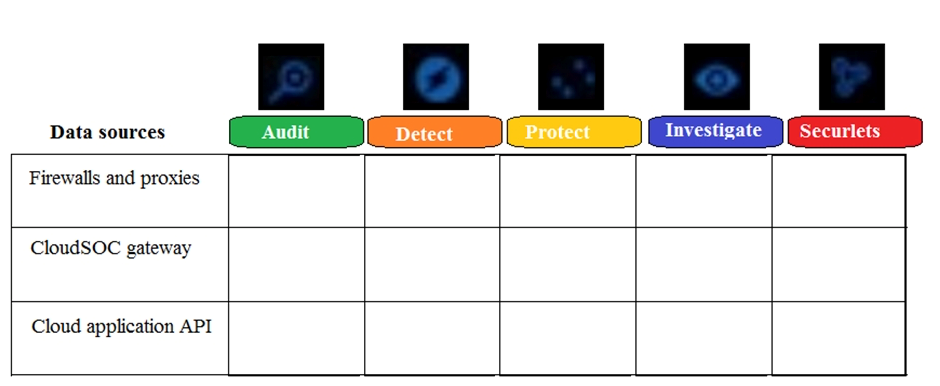
(Multiple Choice)
4.9/5  (40)
(40)
What module should an administrator use to create policies with one click, and send them to the Protect Module?
(Multiple Choice)
4.9/5  (35)
(35)
What Rule Type in ContentIQ do movies, presentations, raster images, spreadsheets, word processors, and vector graphics belong to?
(Multiple Choice)
4.8/5  (46)
(46)
What categories should an administrator utilize to classify cloud applications during the cloud applications adoption workflow?
(Multiple Choice)
4.8/5  (42)
(42)
Refer to the exhibit. Which CloudSOC module(s) use firewalls and proxies as data sources? 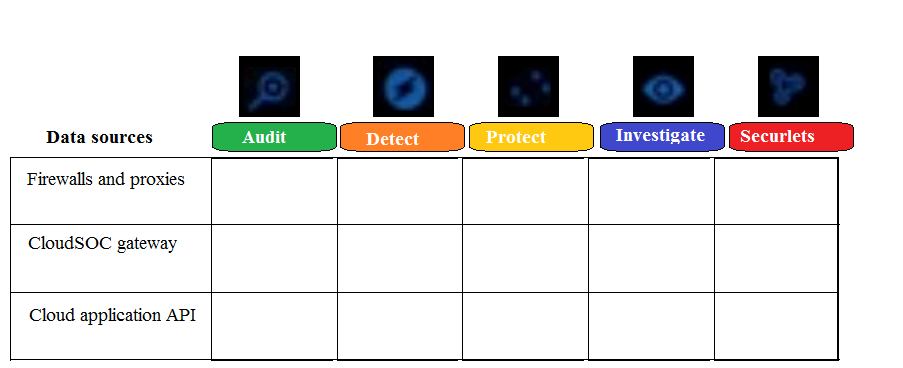
(Multiple Choice)
4.8/5  (37)
(37)
What Business Readiness Rating (BRR) category does the subcategory "HTTP Security Headers" belong to?
(Multiple Choice)
4.8/5  (38)
(38)
What Business Readiness Rating (BRR) category does the subcategory "Password Quality Rules" belong to?
(Multiple Choice)
4.9/5  (46)
(46)
What modules are used in the use case "Identify and remediate malicious behavior within cloud applications"?
(Multiple Choice)
4.9/5  (25)
(25)
What CloudSOC module should an administrator use to identify and understand how information is used within cloud applications?
(Multiple Choice)
4.8/5  (32)
(32)
What type of log upload should an administrator use during production?
(Multiple Choice)
4.9/5  (30)
(30)
Which of the following is NOT a component of a proxy service listener?
(Multiple Choice)
4.8/5  (32)
(32)
A primary difference between a proxy server and a firewall is that proxy is not fundamentally what?
(Multiple Choice)
4.9/5  (43)
(43)
Where should an administrator locate the level of exposure in files in the Securlet module?
(Multiple Choice)
4.8/5  (31)
(31)
What is one drawback to using apparent data type to detect the file type?
(Multiple Choice)
4.9/5  (36)
(36)
Showing 61 - 80 of 98
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)