Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
What needs to be selected for the Explicit HTTP service to be able to hand off SSL traffic?
(Multiple Choice)
4.8/5  (44)
(44)
Which action should an administrator take if a cloud application fails to meet security and compliance requirements, but the business need outweighs the risks?
(Multiple Choice)
4.9/5  (43)
(43)
Which built-in tool would you use to monitor external resources?
(Multiple Choice)
4.8/5  (34)
(34)
Which CloudSOC module(s) use cloud application APIs as data sources?
(Multiple Choice)
4.8/5  (37)
(37)
What is one of the security challenges generated by the proliferation of cloud applications?
(Multiple Choice)
4.8/5  (38)
(38)
Refer to the exhibit. What does this Access Monitoring policy do? 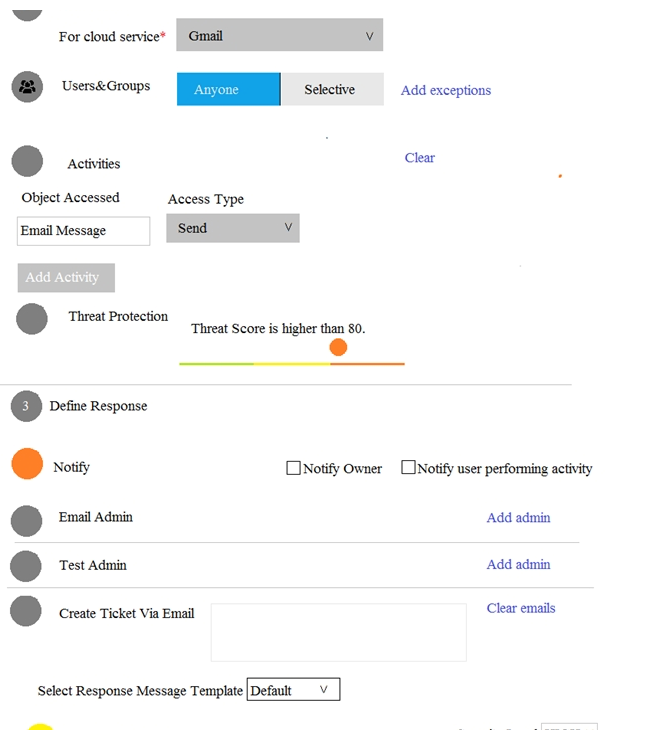
(Multiple Choice)
4.8/5  (35)
(35)
What module should an administrator use to identify anomalous user behavior such as large amounts of data being downloaded, too many files being shared, or logins from suspicious locations?
(Multiple Choice)
4.9/5  (40)
(40)
Which SGOS edition is designed for Secure Web Gateway deployments?
(Multiple Choice)
4.9/5  (41)
(41)
Which of the following are recommended to improve CPU performance? (Choose two.)
(Multiple Choice)
4.8/5  (35)
(35)
What variable increases when a detector is triggered by a suspicious behavior?
(Multiple Choice)
4.9/5  (43)
(43)
When the ProxySG uses a virtual URL for user authentication, what must the virtual URL point to?
(Multiple Choice)
4.9/5  (34)
(34)
What should an administrator utilize to steer traffic from client devices to the CloudSOC gateway?
(Multiple Choice)
4.8/5  (37)
(37)
When policy created in the VPM is installed, what two files does the VPM update on the ProxySG? (Choose two.)
(Multiple Choice)
4.9/5  (37)
(37)
What should an administrator use to identify document types specified by the user?
(Multiple Choice)
4.8/5  (30)
(30)
What would happen if the ProxySG did not use surrogate credentials to authenticate users who use transparent proxy connections?
(Multiple Choice)
4.9/5  (29)
(29)
Showing 81 - 98 of 98
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)