Exam 5: HCNP-R&S Fast Track (Huawei Certified Network Professional - Routing & Switching Fast Track)
Exam 1: HCNA-VC (Huawei Certified Network Associate - Video Conference)151 Questions
Exam 2: HHCIA Routing&Switching456 Questions
Exam 3: HCNP-R&S-IERN (Huawei Certified Network Professional-Implementing Enterprise Routing Network)206 Questions
Exam 4: HCNP-R&S-IENPÂ (Huawei Certified Network Professional-Improving Enterprise Network Performance)10 Questions
Exam 5: HCNP-R&S Fast Track (Huawei Certified Network Professional - Routing & Switching Fast Track)733 Questions
Exam 6: HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching)331 Questions
Exam 7: HCNA-Security-CBSN (Huawei Certified Network Associate - Constructing Basic Security Network)27 Questions
Exam 8: HCNA-Storage-BSSN (Huawei Certified Network Associate - Building the Structure of Storage Network)170 Questions
Exam 9: HCNA-Storage-BSSN60 Questions
Exam 10: Huawei Certified Network Professional- Constructing Big Data Solution215 Questions
Exam 11: HCIE-Storage472 Questions
Exam 12: HCIA-Cloud Service V2.236 Questions
Exam 13: Huawei Certified Pre-sales Associate-IP Network(Datacom)-ENU101 Questions
Exam 14: Huawei Certified Pre-sales Associate - ECC (HCPA-ECC)24 Questions
Exam 15: HCNA - Carrier IP25 Questions
Exam 16: HCIP-Cloud Computing-CDSM28 Questions
Exam 17: HCIA-SDN53 Questions
Select questions type
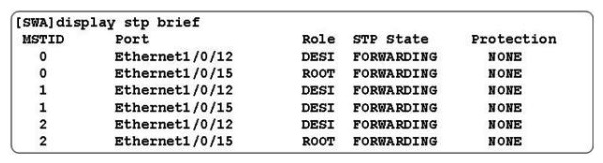 On the MSTP network as shown in the figure, what is the role of the switch in MSTID according to the configuration?
On the MSTP network as shown in the figure, what is the role of the switch in MSTID according to the configuration?
(Multiple Choice)
4.8/5  (34)
(34)
A router receives a data packet, with the destination address being 195.26.17.4. Which subnet is this address in?
(Multiple Choice)
4.9/5  (37)
(37)
Which of the following traffic can be mirrored through port mirroring? (Choose all that apply.)
(Multiple Choice)
4.9/5  (45)
(45)
Two Eudemons in dual-system hot backup mode use Huawei Redundancy Protocol (HRP) to back up key information (such as configuration commands and session status) between the active and standby devices.
(True/False)
4.9/5  (44)
(44)
Which of the following statements about a backup router in a VRRP backup group are true? (Choose three.)
(Multiple Choice)
4.9/5  (37)
(37)
Before configuring 802.1x services, you need to determine the configuration roadmap and prepare data. Which are general steps in the configuration roadmap? (Choose three.)
(Multiple Choice)
5.0/5  (36)
(36)
Which of the following statements about the link failure detection in STP protocol is not true?
(Multiple Choice)
4.7/5  (31)
(31)
An IP-prefix-filter is used to filter IP prefixes and data packets.
(True/False)
4.9/5  (41)
(41)
How does a BGP router process the received route whose next hop is unreachable?
(Multiple Choice)
4.8/5  (34)
(34)
RSTP has all functions that STP has and it is backward compatible with STP.
(True/False)
4.8/5  (43)
(43)
The reliability of a product or a system is generally evaluated with the two indicators of Mean Time to Repair (MTTR) and Mean Time Between Failures (MTBF).
(True/False)
4.8/5  (35)
(35)
Which of the following attacks is not the network layer attack?
(Multiple Choice)
4.9/5  (42)
(42)
Which of the following attacks are prevented after an IP address and MAC address are bound on the USG? (Choose two.)
(Multiple Choice)
4.9/5  (40)
(40)
In Round Robin mode, the device sends packets based on the number of defined bytes of each queue. The bandwidth ratio of each queue is the ratio of the number of defined bytes of the local queue to the total number of defined bytes of all queues.
(True/False)
4.8/5  (35)
(35)
Which of the following aspects should be considered for migration risk assessment?
(Multiple Choice)
4.8/5  (39)
(39)
OSPF uses SPF algorithm to calculate SPF tree according to topology. Which of the following statements are correct regarding SPF tree node? (Choose two.)
(Multiple Choice)
4.8/5  (39)
(39)
Which method is used to establish session between the BGP peers?
(Multiple Choice)
4.9/5  (48)
(48)
In PIM-DM, which of the following messages needs to be sent by a downstream interface when the downstream interface recovers to the forwarding state from the prune state?
(Multiple Choice)
4.8/5  (28)
(28)
On a switch running GVRP, each interface is considered as a participant. The participants can exchange information.
(True/False)
4.8/5  (48)
(48)
Showing 41 - 60 of 733
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)