Exam 15: Evaluating Electronic Information
Exam 1: Understanding Computers and Computer Literacy46 Questions
Exam 2: The Internet and the World Wide Web48 Questions
Exam 3: The Internet and Research48 Questions
Exam 4: How a Computer Processes Data41 Questions
Exam 5: Input, Output, and Storage44 Questions
Exam 6: Operating Systems and Software42 Questions
Exam 7: Networks Unit45 Questions
Exam 8: Windows and File Management48 Questions
Exam 9: Email and Electronic Communication47 Questions
Exam 10: Word Processing44 Questions
Exam 11: Presentation Graphics45 Questions
Exam 12: Spreadsheets41 Questions
Exam 13: Databases42 Questions
Exam 14: Integration Feature Unit46 Questions
Exam 15: Evaluating Electronic Information44 Questions
Exam 16: Creating a Web Page48 Questions
Exam 17: Technology, the Workplace, and Society44 Questions
Select questions type
Links that are no longer active are called "____."
Free
(Multiple Choice)
4.9/5  (32)
(32)
Correct Answer:
C
____________________ is the unauthorized copying of software.
Free
(Short Answer)
4.8/5  (33)
(33)
Correct Answer:
Software piracy
____ is the ability to use links to move through a site.
Free
(Multiple Choice)
4.7/5  (28)
(28)
Correct Answer:
A
If the domain portion of a Web site is ____, the site is used for government resources.
(Multiple Choice)
4.8/5  (34)
(34)
A very important consideration of an effective site is its ____________________, which refers to the age of the information, how long it has been posted, and how often it is updated.
(Short Answer)
4.9/5  (32)
(32)
Please use the figure below to answer the following two questions.
FIGURE 15-1
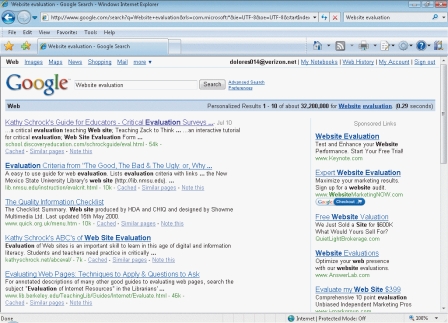 -Figure 15-1 shows a Google search with Sponsored Links. How do companies get their entries listed in the sponsored site area?
-Figure 15-1 shows a Google search with Sponsored Links. How do companies get their entries listed in the sponsored site area?
(Multiple Choice)
4.9/5  (35)
(35)
A ____ site is a site that has paid the search engine a fee in exchange for being listed in the "Sponsored Sites" section on many of their pages.
(Multiple Choice)
4.9/5  (36)
(36)
Search engines are programs written to query and retrieve information stored in a database.
(True/False)
4.9/5  (38)
(38)
Processes and business methods may be protected by ____, which guarantee the inventor exclusive copyright to the process or method for a certain time period.
(Multiple Choice)
4.7/5  (37)
(37)
If the domain portion of a Web site is ____, the site is used for military branches.
(Multiple Choice)
4.8/5  (29)
(29)
Please use the figure below to answer the following two questions.
FIGURE 15-1
 -When looking at the Sponsored Links in Figure 15-1, the companies appear to be sharing ____.
-When looking at the Sponsored Links in Figure 15-1, the companies appear to be sharing ____.
(Multiple Choice)
4.9/5  (36)
(36)
Software programs can be installed on a computer or network that automatically block access to user-specified sites or to sites with specified content.
(True/False)
4.9/5  (39)
(39)
Internet resources used in reports must be cited, which means giving credit to any information you include in a report that is not your original thought.
(True/False)
4.9/5  (40)
(40)
Please identify the letter of the choice that best matches the numbered definitions below.
-Guarantees the inventor exclusive copyright to the process or method for a certain time period
(Multiple Choice)
4.8/5  (45)
(45)
____ are stories that at one time could have been partially true, but have grown from constant retelling into a mythical yarn.
(Multiple Choice)
4.8/5  (34)
(34)
The first page, or about page, of a Web site indicates how the site is organized and what options are available.
(True/False)
4.7/5  (47)
(47)
A(n) ____________________ is an attempt to deceive an audience into believing that something false is real.
(Short Answer)
4.9/5  (39)
(39)
Nancy has started her own flower delivery business. She has created a logo and a unique delivery process. Please answer the questions below.
-To protect her unique delivery process from being used by other companies, Nancy would pursue obtaining a ____.
(Multiple Choice)
4.9/5  (39)
(39)
Which of the following is NOT a feature of properly used links in a Web site?
(Multiple Choice)
4.7/5  (31)
(31)
Showing 1 - 20 of 44
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)