Exam 8: Security
Exam 1: Introduction14 Questions
Exam 2: The Information Systems Strategy Triangle52 Questions
Exam 3: Strategic Use of Information Resources63 Questions
Exam 4: Organizational Strategy and Information Systems53 Questions
Exam 5: Information Systems and the Design of Work55 Questions
Exam 6: Information Systems and Business Transformation60 Questions
Exam 7: Architecture and Infrastructure57 Questions
Exam 8: Security40 Questions
Exam 9: The Business of Information Technology71 Questions
Exam 10: Governance of the Information Systems Organization48 Questions
Exam 11: Information Systems Sourcing54 Questions
Exam 12: Managing IT Projects60 Questions
Exam 13: Business Intelligence Knowledge Management and Analytics53 Questions
Exam 14: Privacy and Ethical Considerations in Information Management47 Questions
Select questions type
Over time, attackers have had to increase their skills to be able to attack systems or create viruses.
(True/False)
4.7/5  (40)
(40)
The deep web is a part of the internet that includes unindexed websites offering both legal and illegal items, such as passports, citizenship, and even murders for hire.
(True/False)
4.9/5  (46)
(46)
You can purchase stolen credit cards on the "deep web" using a browser called "Tor."
(True/False)
4.9/5  (34)
(34)
All of the following are classic signs of a phishing message except:
(Multiple Choice)
4.9/5  (36)
(36)
According to the late L. Dain Gary, "You cannot make a computer secure."
(True/False)
4.7/5  (36)
(36)
Included in the five critical elements that are used to raise security in a firm are all of the following except:
(Multiple Choice)
4.9/5  (32)
(32)
Of the seven security policies noted in Chapter 7 (Figure 7.5), name at least three.
Matching
(Short Answer)
4.9/5  (37)
(37)
If you receive an email that says it is from Sam Johnson, your boss, with an odd EXE file as an attachment, it could be dangerous for all of the following reasons except:
(Multiple Choice)
4.8/5  (31)
(31)
Thanks to tightened security in operating systems, it is more difficult than ever before for hackers to break into systems, compared to the early 1990s, when people were much less often protected, less aware of risks, and more easily fooled.
(True/False)
4.8/5  (33)
(33)
This is a situation in which the thief counterfeits a different person's address
(Short Answer)
4.7/5  (36)
(36)
If you receive an email from your son, and the body of the email tells you to open an attachment because it is funny, the risk is pretty close to zero because it came from your son.
(True/False)
4.9/5  (43)
(43)
What security and controls should a company use to protect its computer infrastructure? Why do managers need to be involved in the decisions about security and control measures?
(Essay)
4.8/5  (33)
(33)
Match the security tool to its security category.
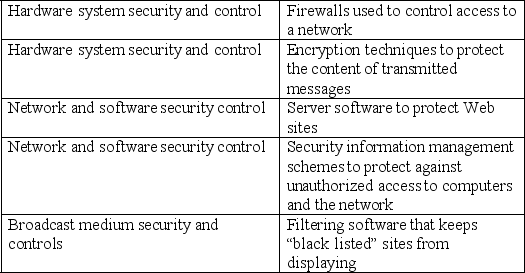
(Not Answered)
This question doesn't have any answer yet
The Deep Web is reputed to be 400 times larger than the public web.
(True/False)
4.9/5  (36)
(36)
It usually takes ____ for someone in a firm to discover a security compromise in a system, after the evidence shows up in logs or alerts
(Multiple Choice)
4.9/5  (42)
(42)
Showing 21 - 40 of 40
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)