Exam 14: Computer Crime and Information Technology Security
Exam 1: Rolse and Purpose of Accountig Information Systems67 Questions
Exam 2: Transaction Processing in the AIS58 Questions
Exam 3: Professionalisam and Ethics62 Questions
Exam 4: Internal Controls62 Questions
Exam 5: Flow Charting65 Questions
Exam 6: Data Flow Diagramming64 Questions
Exam 7: Real Modeling58 Questions
Exam 8: XBRL60 Questions
Exam 9: Business and Enterprise Resource Planning Systems60 Questions
Exam 10: Salles - Collection Process50 Questions
Exam 11: Acquestion Payment Process59 Questions
Exam 12: Other Business Process53 Questions
Exam 13: Bussiness Process Mamagement61 Questions
Exam 14: Computer Crime and Information Technology Security58 Questions
Exam 15: Dicision Making Models and Knowledge Management50 Questions
Exam 16: Professional Certifications and Career Planning48 Questions
Exam 17: Auditing and Evaluating the AIS56 Questions
Select questions type
Computer crime taxonomy, computer criminals and internal controls
For each independent situation below, indicate: (a) the type of computer crime based on Carter's taxonomy, (b) the type of computer criminal and (c) one internal control that would address the crime. Note to instructor: The situations in this problem are different from those in Problem 8. 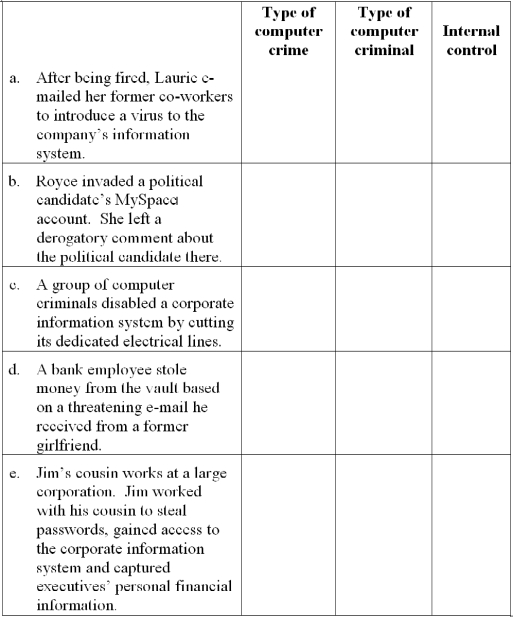
(Essay)
4.8/5  (32)
(32)
A hacker extracts clients' social security numbers from a company's information system, then offers to sell the numbers back to the company to prevent their disclosure. The hacker's actions are an example of:
(Multiple Choice)
4.8/5  (25)
(25)
Information systems professionals would most likely consult with legal professionals for advice regarding which of COBIT's information criteria?
(Multiple Choice)
4.9/5  (40)
(40)
The main difference between hackers and cyber-criminals is:
(Multiple Choice)
4.8/5  (45)
(45)
Indicate one group from COBIT's accountability framework that applies to each item below. Some groups may be repeated. ______________1. Chairman must have accounting or financial management expertise
______________2. Charter must be filed every three years with SEC
______________3. Included in the scope of corporate governance accountability
______________4. Included only in the scope of information governance accountability
______________5. Initiates disclosures about financial and internal control
______________6. Initiates disclosures about information governance control
______________7. Initiates sign-off on all forms of control
______________8. Provide independent review of accounting information system
______________9. Receives recommendations about information governance control
______________10. Source of accountability
(Short Answer)
4.8/5  (34)
(34)
On a monthly basis, internal auditors review an organization's information security policy over a specific group of physical computer assets. The review is an example of a(n):
(Multiple Choice)
4.9/5  (42)
(42)
Carter identified four categories of computer crime. Explain which categories are most appropriate for Tim's action.
(Essay)
4.9/5  (39)
(39)
A computer criminal initiates a denial of service attack designed to shut down a country's air traffic control system. The computer criminal is best described as a(n):
(Multiple Choice)
4.8/5  (33)
(33)
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
-If Calvin carries out the tabloid's request, RRI's information system will fail to meet which of COBIT's information criteria?
(Multiple Choice)
4.9/5  (36)
(36)
COBIT's accountability framework can enhance internal control by assigning responsibility and designating authority for various tasks related to information systems security. Which of the following groups is most suited to develop technical security controls?
(Multiple Choice)
4.8/5  (41)
(41)
List the seven information criteria associated with the COBIT framework. Which criteria will be compromised if Tim activates the program?
(Essay)
4.9/5  (33)
(33)
The textbook identified eleven specific business risks/threats associated with information technology. Discuss three that apply in this situation.
(Essay)
4.8/5  (28)
(28)
Corporate spies are most closely associated with which of the following business risks?
(Multiple Choice)
4.9/5  (31)
(31)
In MRT Corporation, users must say a specific phrase to gain access to information systems. The system identifies both the phrase and the user's voice before allowing access. MRT's system is an example of a(n):
(Multiple Choice)
4.9/5  (36)
(36)
As a form of internal control, fingerprint scans are most likely to prevent:
(Multiple Choice)
4.8/5  (37)
(37)
A terrorist posts a threatening message on a web site. The post is an example of which element of Carter's taxonomy?
(Multiple Choice)
4.9/5  (37)
(37)
COBIT's accountability framework can enhance internal control by assigning responsibility and designating authority for various tasks related to information systems security. Which of the following groups is ultimately responsible for developing and maintaining a strong internal control system?
(Multiple Choice)
4.8/5  (34)
(34)
As an administrative security control, a well-written conflict of interest policy would be most helpful in punishing which category of computer criminal?
(Multiple Choice)
4.9/5  (34)
(34)
An unhappy employee has installed a logic bomb in an organization's information system. If the bomb is activated, which of COBIT's information criteria is most likely to be compromised?
(Multiple Choice)
4.8/5  (41)
(41)
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
-Which of the following internal controls would be most effective in preventing Calvin from carrying out the tabloid's request?
(Multiple Choice)
4.7/5  (42)
(42)
Showing 21 - 40 of 58
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)