Exam 14: Computer Crime and Information Technology Security
Exam 1: Rolse and Purpose of Accountig Information Systems67 Questions
Exam 2: Transaction Processing in the AIS58 Questions
Exam 3: Professionalisam and Ethics62 Questions
Exam 4: Internal Controls62 Questions
Exam 5: Flow Charting65 Questions
Exam 6: Data Flow Diagramming64 Questions
Exam 7: Real Modeling58 Questions
Exam 8: XBRL60 Questions
Exam 9: Business and Enterprise Resource Planning Systems60 Questions
Exam 10: Salles - Collection Process50 Questions
Exam 11: Acquestion Payment Process59 Questions
Exam 12: Other Business Process53 Questions
Exam 13: Bussiness Process Mamagement61 Questions
Exam 14: Computer Crime and Information Technology Security58 Questions
Exam 15: Dicision Making Models and Knowledge Management50 Questions
Exam 16: Professional Certifications and Career Planning48 Questions
Exam 17: Auditing and Evaluating the AIS56 Questions
Select questions type
Calvin works as an accountant for RRI Inc., a corporation that manages the financial assets of wealthy clients, such as movie stars and politicians. Calvin has not received a pay increase in three years and has grown unhappy in his position. He has been approached by a tabloid newspaper with an offer for significant monetary compensation in exchange for personal facts about RRI's clients. Because he feels unappreciated and underpaid, Calvin is seriously considering the tabloid's offer, even though it violates RRI's information security policy and the agreements RRI has with its clients.
-If Calvin accepts the offer, the crime he commits will most likely involve computers as:
(Multiple Choice)
4.8/5  (38)
(38)
Computer crime taxonomy: Fill in each blank below with a word or phrase based on Carter's taxonomy of computer crime.
a. Target: This category is comprised of computer crimes where the criminal targets ______. The objective of these crimes is to impact the ______ of data stored on the computer.
b. Instrumentality: Computer as the instrumentality of the crime uses the computer to ______. The computer is used to ______.
c. Incidental: This type of computer crime encompasses crimes where the computer is not ______ but is ______. The use of computer ______ and may make the crime more difficult to ______.
d. Associated: The simple ______ of computers, and notably the growth of the Internet, has generated ______of ______. In these cases, technological growth essentially creates ______ and new ways of ______.
(Short Answer)
4.9/5  (41)
(41)
An unhappy employee introduces a virus that will shut down a company's information system if his name no longer appears in the payroll database. The employee's action is an example of which element of Carter's taxonomy?
(Multiple Choice)
4.8/5  (46)
(46)
Extortion is an example of: (i) a computer-associated crime, (ii) computer as incidental to a crime?
(Multiple Choice)
4.8/5  (34)
(34)
A bank teller steals money from the vault and covers up the theft by making a journal entry in the accounting information system. The teller's actions are an example of which element of Carter's taxonomy?
(Multiple Choice)
4.9/5  (40)
(40)
An attempt to gain access to a network or a system by bypassing security controls is referred to as a(n):
(Multiple Choice)
4.8/5  (41)
(41)
Which type of computer criminal is most closely associated with spamming, phishing, extortion and other profitable branches of computer crime?
(Multiple Choice)
4.9/5  (29)
(29)
As a business risk, extortion can be preceded by: (i) information theft, (ii) error, (iii) malicious software.
(Multiple Choice)
4.8/5  (33)
(33)
According to the COBIT accountability framework, the scope of corporate governance accountability and the scope of information governance accountability differ based on (i) the presence of disclosure, (ii) the stakeholders involved.
(Multiple Choice)
4.9/5  (38)
(38)
According to Carter's taxonomy of computer crime, which of the following best describes the computer as incidental?
(Multiple Choice)
4.9/5  (39)
(39)
The COBIT framework can be used to strengthen internal controls against computer crime by helping information systems professionals: (i) identify risk, (ii) assign responsibility, (iii) designate authority.
(Multiple Choice)
4.8/5  (39)
(39)
Identify the type of computer criminal described in each of the following cases. __________a. Could disrupt power grids, telecommunications and transportation systems
__________b. Have been getting into spamming, phishing and extortion
__________c. Inexperienced hacker who uses tools written by others to attack systems
__________d. Possess advanced skills and have turned to hacking for the money
__________e. Someone who invades an information system for malicious purposes
__________f. Take advantage of computer intrusion techniques to gather information
__________g. The largest threat to a company's information systems
(Short Answer)
4.9/5  (41)
(41)
Which type of computer criminal is least sophisticated in terms of computer knowledge?
(Multiple Choice)
4.8/5  (40)
(40)
According to Carter's taxonomy of computer crime, which of the following best describes the computer as a target?
(Multiple Choice)
4.8/5  (31)
(31)
Administrative security controls can be used to prevent problems with (i) confidentiality, (ii) data integrity, (iii) availability.
(Multiple Choice)
4.8/5  (46)
(46)
A customer's bank account should be credited with $10.532 interest. The bank's information system is most exposed to which of the following risks/threats?
(Multiple Choice)
4.8/5  (28)
(28)
Which type of internal control is most closely associated with COBIT's "compliance" information criterion?
(Multiple Choice)
4.7/5  (36)
(36)
Computer crime taxonomy, computer criminals and internal controls
For each independent situation below, indicate: (a) the type of computer crime based on Carter's taxonomy, (b) the type of computer criminal and (c) one internal control that would address the crime. Note to instructor: The situations in this problem are different from those in Problem 7. 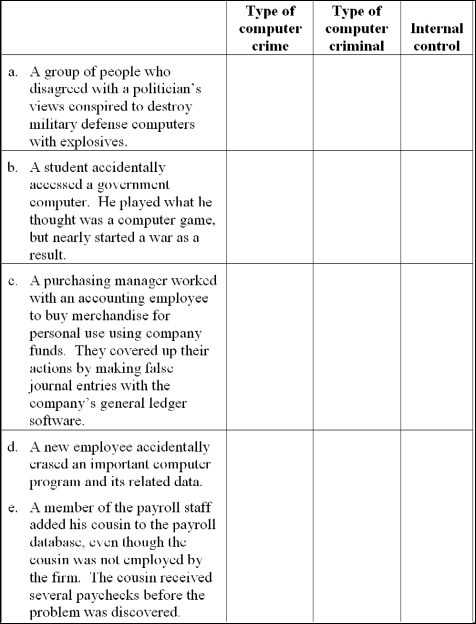
(Essay)
4.9/5  (30)
(30)
Showing 41 - 58 of 58
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)