Exam 11: Computer Security and Safety, Ethics, and Privacy
Exam 1: Introduction to Computers181 Questions
Exam 2: The Internet and the World Wide Web181 Questions
Exam 3: Application Software181 Questions
Exam 4: The Components of the Unit System181 Questions
Exam 5: Input181 Questions
Exam 6: Output181 Questions
Exam 7: Storage181 Questions
Exam 8: Operating Systems and Utility Programs181 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management181 Questions
Exam 11: Computer Security and Safety, Ethics, and Privacy181 Questions
Exam 12: Information System Development181 Questions
Exam 13: Programming Languages and Program Development181 Questions
Exam 14: Enterprise Computing181 Questions
Exam 15: Computer Careers and Certification181 Questions
Select questions type
COGNITIVE ASSESSMENT Which of the following term is used to describe a vulnerable computer that is set up to entice an intruder to break into it?
Free
(Multiple Choice)
4.9/5  (37)
(37)
Correct Answer:
A
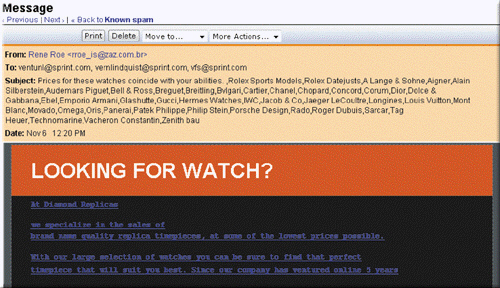 An alternative to e-mail filtering is to purchase which of the following kinds of program that attempts to remove a message, like the one in the accompanying figure, before it reaches a user's inbox?
An alternative to e-mail filtering is to purchase which of the following kinds of program that attempts to remove a message, like the one in the accompanying figure, before it reaches a user's inbox?
Free
(Multiple Choice)
4.9/5  (28)
(28)
Correct Answer:
D
____________________ is the process of converting readable data into unreadable characters to prevent unauthorized access.
Free
(Short Answer)
4.8/5  (35)
(35)
Correct Answer:
Encryption
The computer that a hacker uses for nefarious purposes, known as a(n) ____________________, is unaware that it is being used to attack other systems.
(Short Answer)
4.8/5  (32)
(32)
COGNITIVE ASSESSMENT Which of the following best describes the term, cybercrime?
(Multiple Choice)
4.8/5  (32)
(32)
Thieves often target notebook computers of company executives, so they can use the stolen computer to access confidential company information illegally.
(True/False)
4.9/5  (36)
(36)
Which of the following kinds of suppressors uses special electrical components to smooth out minor noise, provide a stable current flow, and keep an overvoltage from reaching a computer and other electronic equipment?
(Multiple Choice)
4.9/5  (42)
(42)
Which of the following is a technique intruders use to make their network or Internet transmission appear legitimate to a victim computer or network?
(Multiple Choice)
4.8/5  (40)
(40)
COGNITIVE ASSESSMENT Which of the following statements is not true about software theft?
(Multiple Choice)
4.9/5  (36)
(36)
COGNITIVE ASSESSMENT Which of the following statements is not true about backing up?
(Multiple Choice)
4.9/5  (44)
(44)
Digital signatures often are used to ensure that an imposter is not participating in an Internet transaction.
(True/False)
4.9/5  (34)
(34)
Which of the following is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed?
(Multiple Choice)
4.8/5  (41)
(41)
With a three-generation backup policy, the grandparent is which of the following?
(Multiple Choice)
4.8/5  (40)
(40)
Information collected and stored about individuals should be limited to what is necessary to carry out the function of the business or government agency collecting the data.
(True/False)
4.8/5  (33)
(33)
Many systems implement access controls using a two-phase process called identification and authentication.
(True/False)
4.9/5  (38)
(38)
Software ____________________ is a fairly simple crime to commit, because many buyers believe they have the right to copy software they have paid for, and because in some countries legal protection for software does not exist.
(Short Answer)
4.9/5  (38)
(38)
Many browsers offer 128-bit encryption and 256-bit encryption, which are higher levels of protection than 40-bit encryption because they have longer encryption keys.
(True/False)
4.9/5  (33)
(33)
A(n) ____________________ is a program or set of instructions in a program that allow users to bypass security controls when accessing a program, computer, or network.
(Short Answer)
4.7/5  (31)
(31)
Showing 1 - 20 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)