Exam 11: Computer Security and Safety, Ethics, and Privacy
Exam 1: Introduction to Computers181 Questions
Exam 2: The Internet and the World Wide Web181 Questions
Exam 3: Application Software181 Questions
Exam 4: The Components of the Unit System181 Questions
Exam 5: Input181 Questions
Exam 6: Output181 Questions
Exam 7: Storage181 Questions
Exam 8: Operating Systems and Utility Programs181 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management181 Questions
Exam 11: Computer Security and Safety, Ethics, and Privacy181 Questions
Exam 12: Information System Development181 Questions
Exam 13: Programming Languages and Program Development181 Questions
Exam 14: Enterprise Computing181 Questions
Exam 15: Computer Careers and Certification181 Questions
Select questions type
A(n) ____________________ is a program that hides in a computer and allows someone from a remote location to take full control of the computer.
(Short Answer)
4.9/5  (30)
(30)
A(n) ____________________ object is any item that must be carried to gain access to a computer or computer facility.
(Short Answer)
4.8/5  (42)
(42)
COGNITIVE ASSESSMENT What is the general term for programs that act without a user's knowledge and deliberately alter the computer's operations?
(Multiple Choice)
5.0/5  (28)
(28)
COGNITIVE ASSESSMENT Which of the following terms is used to describe a scam in which a perpetrator attempts to obtain your personal and financial information via spoofing?
(Multiple Choice)
4.9/5  (33)
(33)
Discuss what a virus is and related examples of malware, and include definitions of the term payload, and a discussion of how a virus delivers a payload in your answer. Also discuss the symptoms of a computer's having been infected with a virus.
(Not Answered)
This question doesn't have any answer yet
COGNITIVE ASSESSMENT Define the term back door, as it refers to computer crime.
(Multiple Choice)
4.9/5  (37)
(37)
COGNITIVE ASSESSMENT You set up your computer so that your elbows are at about 90 degrees and your viewing distance is 18 to 28 inches. What scientific principle are you using to ensure your comfort and safety while using the computer?
(Multiple Choice)
4.8/5  (35)
(35)
Which of the following gives authors and artists the exclusive rights to duplicate, publish, and sell their materials?
(Multiple Choice)
4.9/5  (42)
(42)
Which of the following occurs when a computer consumes someone's entire social life?
(Multiple Choice)
4.9/5  (38)
(38)
COGNITIVE ASSESSMENT Which of the following statements is not true about hardware theft and vandalism?
(Multiple Choice)
4.8/5  (32)
(32)
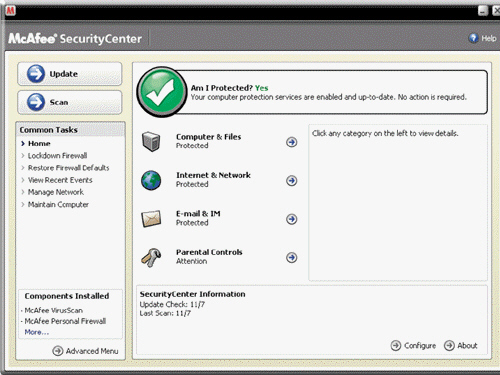 To ____________________ a program file, a program like the one in the accompany figure records information such as the file size and file creation date in a separate file.
To ____________________ a program file, a program like the one in the accompany figure records information such as the file size and file creation date in a separate file.
(Short Answer)
4.8/5  (30)
(30)
COGNITIVE ASSESSMENT Which of the following terms is used to describe an encrypted code that a person, Web site, or organization uses to verify the identity of the message sender?
(Multiple Choice)
4.7/5  (37)
(37)
COGNITIVE ASSESSMENT Define the term, payload, as it pertains to computer crime.
(Multiple Choice)
4.9/5  (26)
(26)
The only acceptable policy for backing up is to produce multiple backup copies.
(True/False)
4.8/5  (37)
(37)
Which of the following is someone who uses e-mail as a vehicle for extortion?
(Multiple Choice)
4.7/5  (30)
(30)
COGNITIVE ASSESSMENT Which of the following terms is used to describe a file a computer creates that records successful and unsuccessful access attempts?
(Multiple Choice)
4.9/5  (39)
(39)
COGNITIVE ASSESSMENT The term, PIN, is an acronym for which of the following?
(Multiple Choice)
4.8/5  (39)
(39)
Showing 101 - 120 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)