Exam 11: Computer Security and Safety, Ethics, and Privacy
Exam 1: Introduction to Computers181 Questions
Exam 2: The Internet and the World Wide Web181 Questions
Exam 3: Application Software181 Questions
Exam 4: The Components of the Unit System181 Questions
Exam 5: Input181 Questions
Exam 6: Output181 Questions
Exam 7: Storage181 Questions
Exam 8: Operating Systems and Utility Programs181 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management181 Questions
Exam 11: Computer Security and Safety, Ethics, and Privacy181 Questions
Exam 12: Information System Development181 Questions
Exam 13: Programming Languages and Program Development181 Questions
Exam 14: Enterprise Computing181 Questions
Exam 15: Computer Careers and Certification181 Questions
Select questions type
Internet advertising firms often use which of the following to collect information about users Web browsing habits?
(Multiple Choice)
4.9/5  (38)
(38)
A(n) ____________________ device authenticates a person's identity by translating a personal characteristic into a digital code that then is compared with a digital code stored in the computer verifying a physical or behavioral characteristic.
(Short Answer)
5.0/5  (40)
(40)
Which of the following refers to the right of individuals and companies to deny or restrict the collection and use of information about them?
(Multiple Choice)
4.8/5  (37)
(37)
A particularly devastating type of DoS attack is which kind of DoS attack, in which multiple unsuspecting computers are used to attack multiple computer networks?
(Multiple Choice)
4.9/5  (38)
(38)
Many companies use access controls to minimize the chance that a hacker may intentionally access or an employee may accidentally access confidential information on a computer.
(True/False)
4.9/5  (36)
(36)
Which of the following is a scam in which a perpetrator sends an official looking e-mail that attempts to obtain a user's personal and financial information?
(Multiple Choice)
4.7/5  (42)
(42)
COGNITIVE ASSESSMENT Which of the following statements is not true about user names and passwords?
(Multiple Choice)
4.8/5  (40)
(40)
Explain three safeguards you can use to improve the security of wireless networks.
(Essay)
4.8/5  (33)
(33)
COGNITIVE ASSESSMENT Which of the following terms refers to a written list of guidelines that might include rules that prevent employees from using software illegally or using computers to steal?
(Multiple Choice)
4.8/5  (34)
(34)
Which of the following is a device that contains surge protection circuits and one or more batteries that can provide power during a temporary or permanent loss of power?
(Multiple Choice)
4.8/5  (36)
(36)
Which of the following occurs when the incoming electrical power increases significantly above the normal 120 volts?
(Multiple Choice)
4.9/5  (42)
(42)
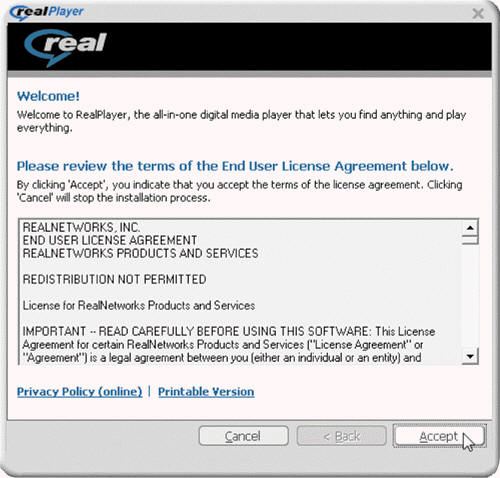 When users purchase software, a(n) ____________________ license agreement like the one in the accompanying figure does not permit users to install the software on a network or to give copies to friends and colleagues.
When users purchase software, a(n) ____________________ license agreement like the one in the accompanying figure does not permit users to install the software on a network or to give copies to friends and colleagues.
(Short Answer)
4.8/5  (30)
(30)
Which of the following is someone who uses the Internet or network to destroy or damage computers for political reasons?
(Multiple Choice)
4.8/5  (28)
(28)
One suggestion to safeguard personal information is to avoid shopping clubs and buyer cards.
(True/False)
4.9/5  (33)
(33)
Identify the letter of the choice that best matches the phrase or definition.
Correct Answer:
Premises:
Responses:
(Matching)
4.8/5  (46)
(46)
Some perpetrators use a technique in which they attempt to connect to wireless networks via their notebook computers while driving a vehicle through areas they suspect have a wireless network. What is the term this technique?
(Multiple Choice)
4.9/5  (42)
(42)
Each character added to a(n) ____________________ significantly increases the number of combinations and the length of time it might take for someone or for a hacker's computer to guess it.
(Short Answer)
4.8/5  (39)
(39)
Showing 141 - 160 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)