Exam 11: Computer Security and Safety, Ethics, and Privacy
Exam 1: Introduction to Computers181 Questions
Exam 2: The Internet and the World Wide Web181 Questions
Exam 3: Application Software181 Questions
Exam 4: The Components of the Unit System181 Questions
Exam 5: Input181 Questions
Exam 6: Output181 Questions
Exam 7: Storage181 Questions
Exam 8: Operating Systems and Utility Programs181 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management181 Questions
Exam 11: Computer Security and Safety, Ethics, and Privacy181 Questions
Exam 12: Information System Development181 Questions
Exam 13: Programming Languages and Program Development181 Questions
Exam 14: Enterprise Computing181 Questions
Exam 15: Computer Careers and Certification181 Questions
Select questions type
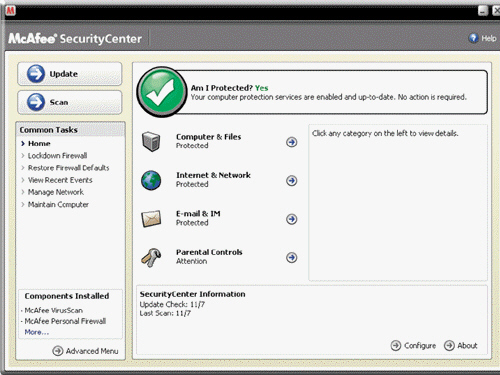 A program, like the one in the accompanying figure, scans for programs that attempt to modify the boot program, the operating system, and other programs that normally are read from but not modified.
A program, like the one in the accompanying figure, scans for programs that attempt to modify the boot program, the operating system, and other programs that normally are read from but not modified.
(True/False)
4.8/5  (39)
(39)
A(n) ____________________ agreement is the right to use software.
(Short Answer)
4.9/5  (28)
(28)
Phishing is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once.
(True/False)
4.7/5  (38)
(38)
Methods that guarantee a computer or network is safe from computer viruses, worms, and Trojan horses exist.
(True/False)
4.8/5  (32)
(32)
Perpetrators of back doors trick their victims into interacting with phony Web sites.
(True/False)
4.9/5  (40)
(40)
Which of the following refers to unique and original works such as ideas, inventions, writings, art, processes, company and product names, and logos?
(Multiple Choice)
5.0/5  (34)
(34)
COGNITIVE ASSESSMENT Which of the following statements is not true about wireless security?
(Multiple Choice)
4.8/5  (26)
(26)
Which of the following 1988 laws regulates the use of government data to determine the eligibility of individuals for federal benefits?
(Multiple Choice)
4.9/5  (32)
(32)
Which of the following copies all of the files in a computer?
(Multiple Choice)
4.8/5  (46)
(46)
COGNITIVE ASSESSMENT In order to safeguard your personal information, which of the following is recommended?
(Multiple Choice)
5.0/5  (43)
(43)
COGNITIVE ASSESSMENT Which of the following terms is used to describe a scam in which a Web site includes a button, image or link that contains a malicious program?
(Multiple Choice)
4.8/5  (32)
(32)
With which of the following do users choose which folders and files to include in a backup?
(Multiple Choice)
5.0/5  (33)
(33)
A(n) ____________________ signature is an encryption code that a person, Web site, or company attaches to an electronic message to verify the identity of the message sender.
(Short Answer)
4.9/5  (40)
(40)
Computer viruses, worms, and Trojan horses deliver their ____________________ on a computer when a user opens an infected file or runs an infected program, for example.
(Short Answer)
4.8/5  (38)
(38)
COGNITIVE ASSESSMENT Antivirus programs look for a specific pattern of virus code. What is this pattern called?
(Multiple Choice)
4.8/5  (32)
(32)
Users can purchase a software program that selectively blocks cookies.
(True/False)
4.9/5  (38)
(38)
The best preventive measures against hardware theft and vandalism are common sense and a constant awareness of the risk.
(True/False)
4.8/5  (41)
(41)
Which of the following involves the use of computers to observe, record, and review an employee's use of a computer, including communications such as e-mail messages, keyboarding activity, and Web sites visited?
(Multiple Choice)
4.8/5  (35)
(35)
Showing 161 - 180 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)