Exam 11: Computer Security and Safety, Ethics, and Privacy
Exam 1: Introduction to Computers181 Questions
Exam 2: The Internet and the World Wide Web181 Questions
Exam 3: Application Software181 Questions
Exam 4: The Components of the Unit System181 Questions
Exam 5: Input181 Questions
Exam 6: Output181 Questions
Exam 7: Storage181 Questions
Exam 8: Operating Systems and Utility Programs181 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management181 Questions
Exam 11: Computer Security and Safety, Ethics, and Privacy181 Questions
Exam 12: Information System Development181 Questions
Exam 13: Programming Languages and Program Development181 Questions
Exam 14: Enterprise Computing181 Questions
Exam 15: Computer Careers and Certification181 Questions
Select questions type
Undervoltages can cause equipment damage, but generally do not cause data loss.
(True/False)
4.8/5  (43)
(43)
Which of the following is any event or action that could cause a loss of or damage to computer hardware, software, data, information, or processing capability?
(Multiple Choice)
4.9/5  (45)
(45)
To help reduce the chance of ____________________, physical controls such as locked doors and cables usually are adequate to protect equipment.
(Short Answer)
4.9/5  (37)
(37)
Biometric objects are gaining popularity because they are entirely foolproof.
(True/False)
4.8/5  (44)
(44)
An online UPS switches to battery power when a problem occurs in the power line.
(True/False)
4.7/5  (39)
(39)
To promote a better understanding of software piracy problems and, if necessary, to take legal action, a number of major worldwide software companies formed the BSA.
(True/False)
4.7/5  (47)
(47)
It is illegal for employers to use software programs that monitor employees.
(True/False)
4.8/5  (38)
(38)
COGNITIVE ASSESSMENT Which of the following statements is not true about biometric devices?
(Multiple Choice)
4.8/5  (42)
(42)
For a computer work space, ergonomics experts recommend an area smaller than two feet by four feet.
(True/False)
4.7/5  (32)
(32)
An employee using an organization's computer to track his or her child's soccer league scores is an example of unauthorized access.
(True/False)
4.7/5  (33)
(33)
 Many Web sites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
Many Web sites, like that in the accompanying figure, require a user to enter a private combination of characters associated with a user name that allows access to certain computer resources. What is the term for this combination of characters?
(Multiple Choice)
4.8/5  (35)
(35)
COGNITIVE ASSESSMENT Which of the following terms is used to describe a program that hides in a computer and allows someone from a remote location to take full control of the computer?
(Multiple Choice)
4.8/5  (38)
(38)
A hash is a mathematical formula that generates a code from the contents of an e-mail message.
(True/False)
4.8/5  (34)
(34)
COGNITIVE ASSESSMENT Define social engineering as it pertains to computers.
(Multiple Choice)
5.0/5  (34)
(34)
A(n) ____________________ control is a security measure that defines who can access a computer, when they can access it, and what actions they can take while accessing the computer.
(Short Answer)
4.9/5  (41)
(41)
A wireless access point (WAP) should be configured to broadcast a network name, in order to increase security.
(True/False)
4.8/5  (34)
(34)
Which of the following is an applied science devoted to incorporating comfort, efficiency, and safety into the design of items in the workplace?
(Multiple Choice)
4.9/5  (29)
(29)
Which of the following kinds of certificate is a notice that guarantees a user or Web site is legitimate?
(Multiple Choice)
5.0/5  (39)
(39)
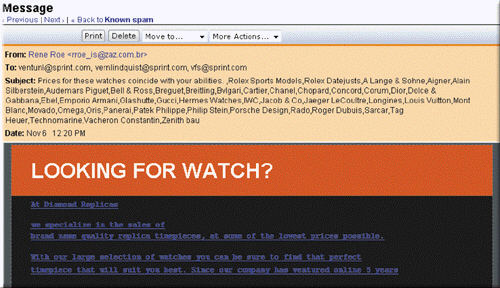 In order to safeguard personal information, you should not reply to messages like those shown in the accompanying figure for any reason.
In order to safeguard personal information, you should not reply to messages like those shown in the accompanying figure for any reason.
(True/False)
4.9/5  (36)
(36)
Although eyestrain associated with CVS (computer vision syndrome) is not thought to be disruptive or unpleasant, it has serious long-term consequences.
(True/False)
4.7/5  (41)
(41)
Showing 61 - 80 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)