Exam 11: Computer Security and Safety, Ethics, and Privacy
Exam 1: Introduction to Computers181 Questions
Exam 2: The Internet and the World Wide Web181 Questions
Exam 3: Application Software181 Questions
Exam 4: The Components of the Unit System181 Questions
Exam 5: Input181 Questions
Exam 6: Output181 Questions
Exam 7: Storage181 Questions
Exam 8: Operating Systems and Utility Programs181 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management181 Questions
Exam 11: Computer Security and Safety, Ethics, and Privacy181 Questions
Exam 12: Information System Development181 Questions
Exam 13: Programming Languages and Program Development181 Questions
Exam 14: Enterprise Computing181 Questions
Exam 15: Computer Careers and Certification181 Questions
Select questions type
COGNITIVE ASSESSMENT Which of the following terms is used to describe a set of steps that can convert readable plaintext into unreadable ciphertext?
(Multiple Choice)
4.8/5  (38)
(38)
Users may have this disorder if they have sore, tired, burning, itching or dry eyes; blurred or double vision; or difficulty focusing on a screen image. What is the name of this disorder?
(Multiple Choice)
4.7/5  (41)
(41)
COGNITIVE ASSESSMENT Which of the following terms is used to describe a small text file that a Web server stores on your computer?
(Multiple Choice)
4.7/5  (42)
(42)
COGNITIVE ASSESSMENT Which of the following terms is used to describe junk mail sent via VoIP.
(Multiple Choice)
4.7/5  (31)
(31)
A(n) ____________________ attack is an assault whose purpose is to disrupt computer access to an Internet service such as the Web or e-mail.
(Short Answer)
4.8/5  (37)
(37)
Which of the following software automatically analyzes all network traffic, assesses system vulnerabilities, identifies any unauthorized access (intrusions), and notifies a network administrator of suspicious behavior patterns or system breaches?
(Multiple Choice)
4.8/5  (40)
(40)
Web sites use which of the following to keep track of items in a user's shopping cart?
(Multiple Choice)
4.8/5  (36)
(36)
What is the term for the prolonged malfunction of a computer?
(Multiple Choice)
5.0/5  (34)
(34)
COGNITIVE ASSESSMENT Which of the following statements is not true about protecting yourself against computer viruses?
(Multiple Choice)
4.8/5  (43)
(43)
COGNITIVE ASSESSMENT Your roommate is complaining about sore eyes and blurred vision after prolonged computer use. What computer-related disorder may she have?
(Multiple Choice)
4.8/5  (30)
(30)
COGNITIVE ASSESSMENT Which of the following statements is not true about Internet and network attacks?
(Multiple Choice)
4.9/5  (25)
(25)
COGNITIVE ASSESSMENT Which of the following terms refers to someone who uses the Internet or network to destroy or damage computers for political reasons?
(Multiple Choice)
4.9/5  (42)
(42)
A UPS for a personal computer should provide about 24 hours of use in the event of a total power loss.
(True/False)
4.8/5  (35)
(35)
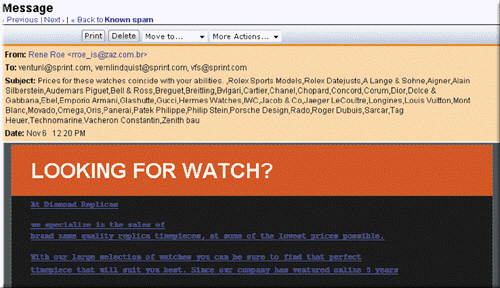 As shown in the accompanying figure, which of the following is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once?
As shown in the accompanying figure, which of the following is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once?
(Multiple Choice)
4.8/5  (39)
(39)
Which of the following category of rights are the rights to which creators are entitled for their work?
(Multiple Choice)
4.9/5  (41)
(41)
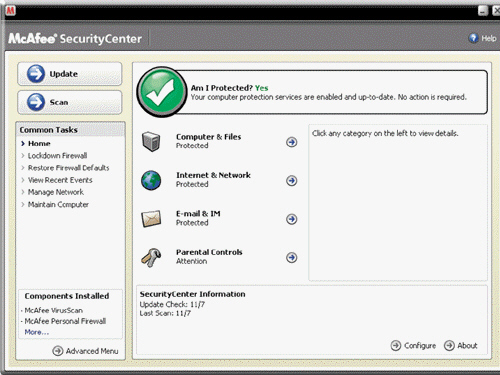 As shown in the accompanying figure, which of the following kinds of program protects a computer against viruses by identifying and removing any computer viruses found in memory, on storage media, or on incoming files?
As shown in the accompanying figure, which of the following kinds of program protects a computer against viruses by identifying and removing any computer viruses found in memory, on storage media, or on incoming files?
(Multiple Choice)
4.9/5  (38)
(38)
To do this to a file means to make a copy of it. What is the term in question?
(Multiple Choice)
4.8/5  (32)
(32)
COGNITIVE ASSESSMENT Which of the following terms refers to someone who accesses a computer or network illegally with the intent of malicious action?
(Multiple Choice)
4.8/5  (36)
(36)
Discuss the four types of software theft.
(Not Answered)
This question doesn't have any answer yet
Showing 21 - 40 of 181
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)