Exam 25: Networks Fundamentals
Exam 1: Computers and Computer Systems46 Questions
Exam 2: Input, Output and Processing46 Questions
Exam 3: Computer Protection46 Questions
Exam 4: Computer Maintenance46 Questions
Exam 5: Computer-Related Issues46 Questions
Exam 6: Software and Hardware Interaction46 Questions
Exam 7: Software Fundamentals46 Questions
Exam 8: Operating Systems46 Questions
Exam 9: Windows Management46 Questions
Exam 10: Operating System Customization46 Questions
Exam 11: Exploring Microsoft Office 201046 Questions
Exam 12: Getting Started With Word Essentials46 Questions
Exam 13: Editing and Formatting Documents46 Questions
Exam 14: Sharing Documents46 Questions
Exam 15: Working With Tables46 Questions
Exam 16: Using Templates, Styles, and Building Blocks46 Questions
Exam 17: Enhancing Documents46 Questions
Exam 18: Getting Started With Excel Essentials46 Questions
Exam 19: Organizing and Enhancing Worksheets46 Questions
Exam 20: Creating Formulas and Charting Data46 Questions
Exam 21: Getting Started With Powerpoint Essentials46 Questions
Exam 22: Enhancing Presentations With Multimedia Effects46 Questions
Exam 23: Getting Started With Access Essentials46 Questions
Exam 24: Managing and Reporting Database Information46 Questions
Exam 25: Networks Fundamentals46 Questions
Exam 26: Communication Services46 Questions
Exam 27: Communications and Collaboration46 Questions
Exam 28: Using the Internet and the World Wide Web46 Questions
Exam 29: Web Content46 Questions
Exam 30: Technology and Society31 Questions
Exam 31: Security, Privacy, and Ethics Online46 Questions
Select questions type
Identify the letter of the choice that best matches the phrase or definition.
Premises:
A wireless technology used to connect mobile computer uses to the Internet across cities and countries.
Responses:
WiMAX
PSTN
WLAN
Correct Answer:
Premises:
Responses:
Free
(Matching)
4.7/5  (44)
(44)
Correct Answer:
Which of the following is true about the benefits of networking?
Free
(Multiple Choice)
4.9/5  (34)
(34)
Correct Answer:
D
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Fiber-optic telephone line used for data transfer on a network.
Responses:
T-1 line
DSL
WiMAX
Correct Answer:
Premises:
Responses:
Free
(Matching)
4.8/5  (28)
(28)
Correct Answer:
Simon is in charge of network security at a medium-sized company. His boss has asked him to give an overview of the company's network security to the board of directors. Simon tells the board that he uses a(n) ____ as an intermediary between a user and the Internet, ensuring security, administrative control, and caching service.
(Multiple Choice)
4.8/5  (45)
(45)
A telephone network is similar in makeup to a computer network, though it transfers voice data.
(True/False)
4.7/5  (42)
(42)
Digital, mobile, and standard telephones are supported through the PSTN network.
(True/False)
4.9/5  (30)
(30)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
A local network that uses few if any physical wires.
Responses:
PSTN
WLAN
WiMAX
Correct Answer:
Premises:
Responses:
(Matching)
4.9/5  (34)
(34)
Which of the following is NOT true about connecting to the Internet?
(Multiple Choice)
4.9/5  (33)
(33)
Information sent over telephone lines is transmitted in the form of binary code.
(True/False)
4.9/5  (30)
(30)
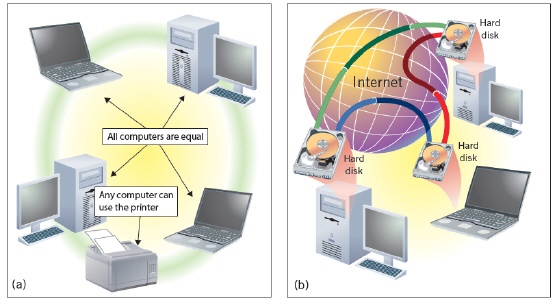 Which of the following is NOT true about the networks shown in the figure above?
Which of the following is NOT true about the networks shown in the figure above?
(Multiple Choice)
4.8/5  (43)
(43)
Ali is researching communication hardware for her Intro to Networking class so that she can write a report for her instructor. Ali learns that all of the following are true, EXCEPT: ____.
(Multiple Choice)
4.7/5  (37)
(37)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Transfers data at a high bandwidth over ordinary copper telephone lines.
Responses:
T-1 line
WLAN
WiMAX
Correct Answer:
Premises:
Responses:
(Matching)
4.8/5  (31)
(31)
Do you always know that computer crime or an intrusion has occurred? What is the best way to protect data? What might someone do if they gain unauthorized access to data? What is the most common form of restricting access? What should a secure password include? Give an example of a secure password. How is most password protection broken?
(Essay)
4.8/5  (41)
(41)
With software sharing companies purchase a site license for users.
(True/False)
4.9/5  (36)
(36)
A(n) ____ is hardware (a computer) that can be used to share mail, databases, and more.
(Multiple Choice)
5.0/5  (34)
(34)
Showing 1 - 20 of 46
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)