Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
While filling out the After Actions Report, an Incident Response Team noted that improved log monitoring could help detect future breaches. What are two examples of how an organization can improve log monitoring to help detect future breaches? (Choose two.)
(Multiple Choice)
4.8/5  (36)
(36)
The DLP services on an Endpoint Server keep stopping. The only events displayed in the Enforce UI are that the server processes have stopped. What is the first step the administrator should take to keep the services on the Endpoint server running?
(Multiple Choice)
4.8/5  (48)
(48)
How does a server know where to retrieve the requested information when it receives a GET request method? (Choose the best answer.)
(Multiple Choice)
4.7/5  (38)
(38)
Refer to the exhibit. 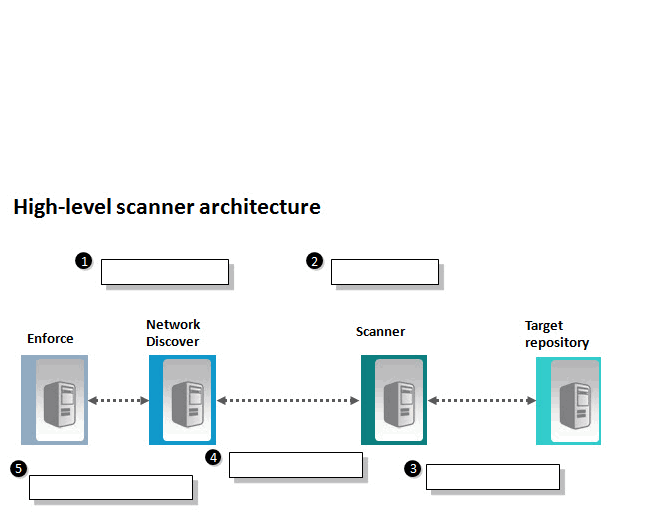 An administrator needs to implement the use of a scanner, but is unfamiliar with the general, high-level process associated with scanners. Which action occurs in step 3?
An administrator needs to implement the use of a scanner, but is unfamiliar with the general, high-level process associated with scanners. Which action occurs in step 3?
(Multiple Choice)
4.7/5  (34)
(34)
Which valid automated response option should an administrator choose for Email Prevent?
(Multiple Choice)
4.9/5  (46)
(46)
You are using the Symantec Storage Foundation Web GUI to manage a tiered storage environment. The Storage Foundation Web GUI provides a mechanism that allows an improved level of data management over mechanisms. What is this mechanism?
(Multiple Choice)
4.8/5  (35)
(35)
An incident response team has determined that multiple incidents are resulting from the same user action of copying sensitive data to USB devices. Which action should the incident response team take to fix this issue so only one incident per action is detected?
(Multiple Choice)
4.8/5  (28)
(28)
In the administration of a large storage environment, you learn that files not only have differing usages at the times they are created, but that many type of files have individual life cycles. User files do not have a defined lifecycle. You want DST capabilities to manage these files. How does DST help address this issue?
(Multiple Choice)
4.8/5  (29)
(29)
Which two actions should an organization take when deploying Endpoint Prevent according to Symantec best practices? (Select two.)
(Multiple Choice)
4.9/5  (34)
(34)
A compliance officer needs to understand how the company is complying with its data security policies over time. Which report should the compliance officer generate to obtain the compliance information?
(Multiple Choice)
4.8/5  (45)
(45)
A DLP administrator has determined that a Network Discover server is unable to scan a remote file server. Which action should the administrator take to successfully scan the remote file server?
(Multiple Choice)
4.9/5  (33)
(33)
What is the role of Insight within the Advanced Threat Protection (ATP) solution?
(Multiple Choice)
4.8/5  (33)
(33)
A company needs to disable USB devices on computers that are generating a number of recurring DLP incidents. It decides to implement Endpoint Lockdown using Endpoint Prevent, which integrates with Symantec Endpoint Protection Manager and Symantec Management Platform. After incidents are still detected from several agents, the company determines that a component is missing. Which component needs to be added to disable the USB devices once incidents are detected?
(Multiple Choice)
4.9/5  (28)
(28)
How would you define a template that is used in Intelligent Storage Provisioning (ISP)?
(Multiple Choice)
5.0/5  (44)
(44)
An organization has five (5) shops with a few endpoints and a large warehouse where 98% of all computers are located. The shops are connected to the warehouse using leased lines and access internet through the warehouse network. How should the organization deploy the network scanners to observe all inbound and outbound traffic based on Symantec best practices for Inline mode?
(Multiple Choice)
4.9/5  (41)
(41)
While performing a disk group joins operation, you get an error "VxVM vxdg ERROR V-5-1-2866 object: Record already exists in disk group." You want to resolve this error. How should you resolve this error?
(Multiple Choice)
4.9/5  (29)
(29)
While working with volume under VxVM control, you discover that a subdisk is detached from a RAID-5 volume. Because of the failure of the disk or an uncorrectable error on the disk, you get the following error messagE. "VxVM vxio WARNING V-5-0-237 object subdisk detached from RAID-5 volume at column column offset offset" How should you resolve this error?
(Multiple Choice)
4.9/5  (34)
(34)
Which threat is an example of an Advanced Persistent Threat (APT)?
(Multiple Choice)
4.7/5  (28)
(28)
Which stage of an Advanced Persistent Threat (APT) attack do attackers map an organization's defenses from the inside?
(Multiple Choice)
4.9/5  (42)
(42)
Showing 281 - 300 of 409
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)