Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
You need to provide storage space for database application, including permanent data, temporary space, and activity log data. You need to ensure that the storage space that you provide offers data protection against disk failures. Which storage techniques will you use? (Each correct answer presents part of the solution. Select two.)
(Multiple Choice)
4.9/5  (36)
(36)
You have just started a relayout job on a large volume, and your work is interrupted by an unrelated server outage. Site policy requires that the relayout should be completed or rolled back within its scheduled window. You want to stop the relayout and roll back the incomplete changes so that the VxVM configuration is left stable till the relayout can be rescheduled. What would you do to perform this task?
(Multiple Choice)
5.0/5  (38)
(38)
You need to create a traditional third-mirror breakoff snapshot in disk group "testdg" on a volume named "testvol". You've used the vxassist command to start the creation of the snapshot, synchronizing in the background. How do you determine whether the snapshot is ready?
(Multiple Choice)
4.8/5  (38)
(38)
You are auditing a current storage environment that is not utilizing storage tiering. The information gained from the audit is to be used in a new storage tiering design that will have 4 tiers, Tiers 1-4. You need to determine the location for data that is not directly related to an enterprise's business, but nevertheless must be retained. Where should you store this data?
(Multiple Choice)
4.9/5  (33)
(33)
An administrator needs to remove an agent and its associated events from a specific Endpoint Server. Which Agent Task does the administrator need to perform to disable its visibility in the Enforce UI?
(Multiple Choice)
4.8/5  (39)
(39)
Which sandbox technology is available for Email Security.cloud?
(Multiple Choice)
4.7/5  (37)
(37)
When you attempt to start the RAID-5 volume, you are prompted with an error message "VxVM ERROR V-5-1-1237 Volume r5vol is not startable; some subdisks are unusable and the parity is stale." You want to remove this error and start the RAID-5 volume. How will you ensure that you do not encounter this error again?
(Multiple Choice)
4.8/5  (38)
(38)
Which two protocols are available by default and recognized by Network Monitor based on their individual signatures? (Select two.)
(Multiple Choice)
4.8/5  (35)
(35)
Refer to the exhibit. An Incident Responder wants to see what was detected on a specific day by the IPS engine. Which item must the responder choose from the drop-down menu? 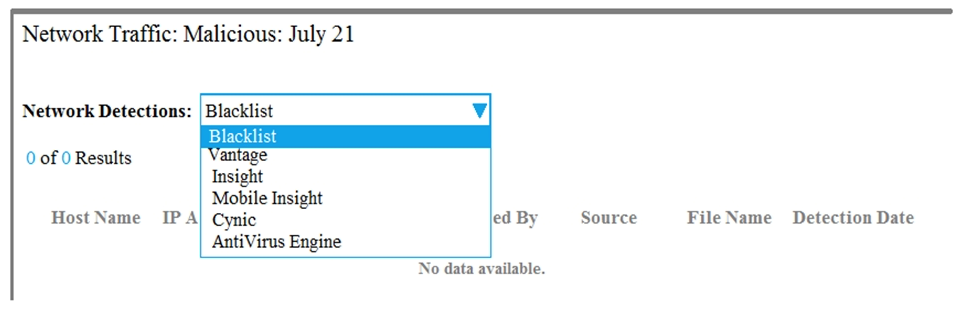
(Multiple Choice)
4.9/5  (42)
(42)
A company needs to secure the content of all Mergers and Acquisitions Agreements. However, the standard text included in all company literature needs to be excluded. How should the company ensure that this standard text is excluded from detection?
(Multiple Choice)
4.9/5  (30)
(30)
Which two (2) categories of traffic are typically left encrypted? (Choose two.)
(Multiple Choice)
4.8/5  (34)
(34)
While working on the Storage Foundation 5.0 server, you execute the following commanD. fsckptadm -n create sat_8pm /mnt0 What is the expected outcome of this command?
(Multiple Choice)
4.9/5  (34)
(34)
Where can an administrator create a new built-in exception on the ProxySG? (Choose the best answer.)
(Multiple Choice)
4.8/5  (32)
(32)
You are the administrator for the Veritas Storage Foundation. Using Veritas Volume Manager, you want to migrate an internal boot disk to a SAN boot disk. Given the following steps: 1. Add the target SAN disk to the boot disk group. 2. Create a mirror of the root disk on the target disk. 3. Verify that the Hardware Compatibility List for the target SAN disk being supported for SAN booting. 4. Boot from the mirror disk to verify that the system is bootable. What are the sequential steps you need to follow to accomplish this?
(Multiple Choice)
4.8/5  (36)
(36)
In which scenario would it be beneficial for an organization to eradicate a threat from the environment by deleting it?
(Multiple Choice)
4.8/5  (36)
(36)
What is the default Transport Layer Security (TLS) port for encrypted email traffic?
(Multiple Choice)
4.8/5  (35)
(35)
What is the basic requirement for deploying Email Security.cloud?
(Multiple Choice)
4.9/5  (39)
(39)
What are the prerequisite products needed when deploying ATP: Endpoint, Network, and Email?
(Multiple Choice)
4.7/5  (37)
(37)
When deploying Network Monitor, an administrator needs to implement monitoring of port-based protocols. Which protocol is supported by Network Monitor?
(Multiple Choice)
4.9/5  (38)
(38)
Which two (2) IT Management Suite 8.1 features should an administrator use in order to display an alert if a specified metric indicates a problem on a server? (Choose two.)
(Multiple Choice)
4.9/5  (32)
(32)
Showing 361 - 380 of 409
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)