Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
An administrator has been notified that a new office location will be opening within a few weeks. The office is a large site that will have 8,000 managed endpoints. The data center is located in Lindon, Utah and the office is located in Houston, Texas. What is the minimum number of site servers needed to support the new office location?
(Multiple Choice)
4.9/5  (40)
(40)
Refer to the exhibit. 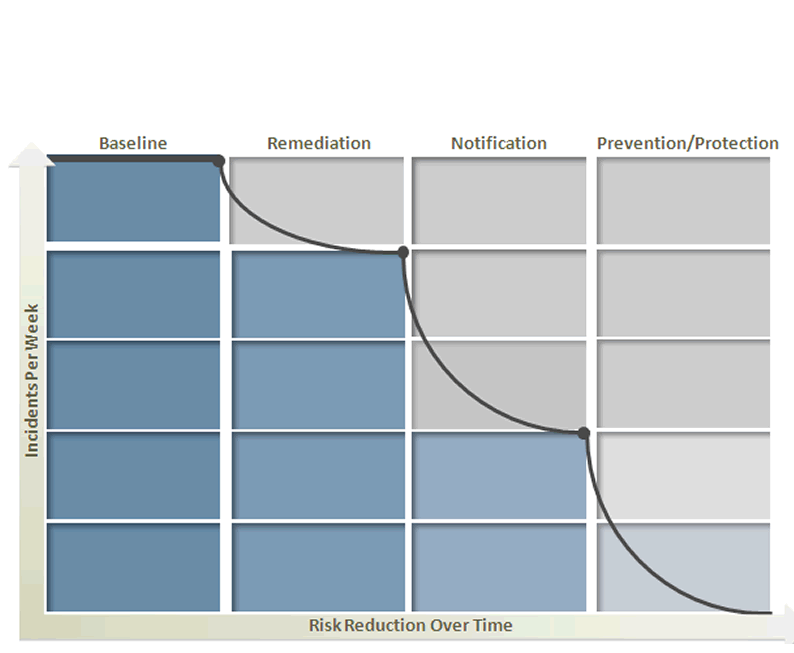 Symantec Data Loss Prevention's four phases of risk reduction model provides a blueprint for identifying and remediating key risk areas without disrupting legitimate business activity. According to this model, which activity should occur during the baseline phase?
Symantec Data Loss Prevention's four phases of risk reduction model provides a blueprint for identifying and remediating key risk areas without disrupting legitimate business activity. According to this model, which activity should occur during the baseline phase?
(Multiple Choice)
4.8/5  (31)
(31)
An administrator is in the process of defining roles within the Symantec Management Console. The administrator adds a user to a Security Role. The user can see the list of reports but cannot execute them. What must the administrator do in order for the user to be able to execute the reports?
(Multiple Choice)
4.9/5  (34)
(34)
What is the Email Security.cloud Service Level Agreement (SLA) for Anti-Spam false positives?
(Multiple Choice)
4.9/5  (31)
(31)
What happens when "0 Minutes" is selected with the Cynic Maximum Hold Time to an email?
(Multiple Choice)
4.8/5  (34)
(34)
Refer to the exhibit. 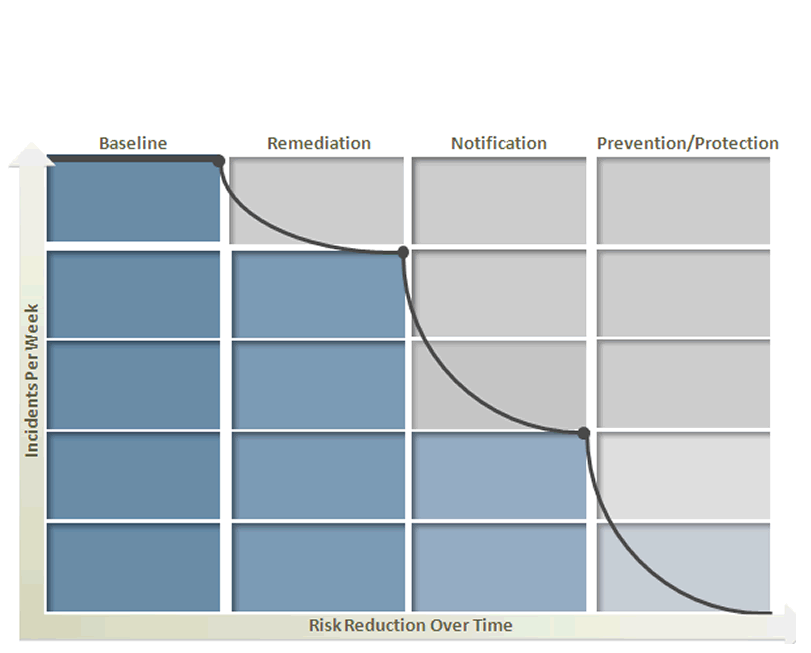 Symantec Data Loss Prevention's four phases of risk reduction model provides a blueprint for identifying and remediating key risk areas without disrupting legitimate business activity. What occurs during the notification phase?
Symantec Data Loss Prevention's four phases of risk reduction model provides a blueprint for identifying and remediating key risk areas without disrupting legitimate business activity. What occurs during the notification phase?
(Multiple Choice)
4.8/5  (37)
(37)
Which website should an administrator browse to when solving Task Service Installation issues to check that the task server is up and running?
(Multiple Choice)
4.9/5  (33)
(33)
What is the primary reason a business would require encrypted email delivery?
(Multiple Choice)
4.8/5  (33)
(33)
Which prerequisite is necessary to extend the ATP: Network solution service in order to correlate email detections?
(Multiple Choice)
4.9/5  (35)
(35)
How should an ATP Administrator configure Endpoint Detection and Response according to Symantec best practices for a SEP environment with more than one domain?
(Multiple Choice)
4.8/5  (49)
(49)
Which default port does ATP use to communicate with the Symantec Endpoint Protection Manager (SEPM) web services?
(Multiple Choice)
4.9/5  (34)
(34)
How does a volume created by VxVM appear in the operating system?
(Multiple Choice)
4.9/5  (34)
(34)
Which two (2) files does the VPM update on the ProxySG when policy created in the VPM is installed? (Choose two.)
(Multiple Choice)
4.9/5  (37)
(37)
You have just performed maintenance operation on a system where VxVM is installed. When you start the system you realize that some disks have entered the FAILED state. After the inspection of the system, you discover that a cable is unplugged. You reconnect the cable. However, after reconnecting the cable, you need to move these disks out of the FAILED state. How should you resolve this error?
(Multiple Choice)
4.9/5  (35)
(35)
Which diagnostic tool allows an administrator to examine how the ProxySG has applied policy to a particular request? (Choose the best answer.)
(Multiple Choice)
5.0/5  (34)
(34)
Why is it important for an Incident Responder to review Related Incidents and Events when analyzing an incident for an After Actions Report?
(Multiple Choice)
4.7/5  (32)
(32)
You are the administrator for Veritas Volume Manager. You are resizing a device by reducing the size of the device, which has a volume configured on it. However, when you attempt to reduce the size, the resize operation fails. You want to ensure you are able to reduce the size of the device. What should you do? (Each correct answer presents a unique solution.)(Select two.)
(Multiple Choice)
4.9/5  (39)
(39)
Which two database attributes are needed to create a Microsoft SQL SEP database connection? (Choose two.)
(Multiple Choice)
4.8/5  (40)
(40)
You want to install the Veritas Enterprise Administrator to manage the Veritas Storage Foundation 5.0 server installed. Before installing the Veritas Enterprise Administrator, you need to know the installation procedure. Given the following installation procedures: 1. Start the Veritas Enterprise Administrator Server on the system to be administered. 2. Start the Veritas Enterprise Administrator Client. 3. Install the Veritas Volume Manager on the system to be administered. 4. Install the Veritas Enterprise Administrator server and client on the system to be administered. What is the correct order of steps that you need to follow?
(Multiple Choice)
4.9/5  (28)
(28)
Showing 121 - 140 of 409
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)