Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
A network control point discovered a botnet phone-home attempt in the network stream. Which detection method identified the event?
(Multiple Choice)
4.9/5  (45)
(45)
You place six physical disks under Volume Manager control to create 10GB of volume. You want to use this volume as an archive directory. You need to create a volume that will store three copies of the archived data. Which command will you use to create a volume with three plexes?
(Multiple Choice)
4.9/5  (34)
(34)
Refer to the exhibit. 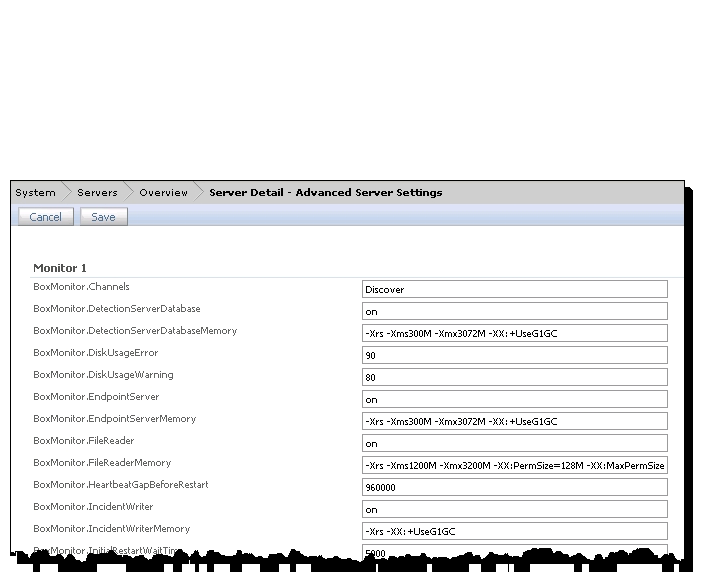 An administrator is testing the DLP installation by placing .EML files into the drop folder, but has been unsuccessful in generating any incidents. The administrator is checking the Advanced Server Settings page to see if it can help diagnose the issue. What could be causing this problem?
An administrator is testing the DLP installation by placing .EML files into the drop folder, but has been unsuccessful in generating any incidents. The administrator is checking the Advanced Server Settings page to see if it can help diagnose the issue. What could be causing this problem?
(Multiple Choice)
4.9/5  (35)
(35)
Which type of Mail Transfer Agent is required for automated group synchronization?
(Multiple Choice)
4.8/5  (37)
(37)
When attempting to log in as administrator to the UI, the administrator receives a login error: Invalid Username/Password or Disabled Account The DBA verifies the account is enabled. The information provided for the environment only includes the DLP protect database username and password as well as a username and password called Sys Admin\Admin. How should the administrator change the built-in 'Administrator' password?
(Multiple Choice)
4.8/5  (42)
(42)
Which endpoint detection method allows for information about triggered processes to be displayed in ATP?
(Multiple Choice)
4.9/5  (47)
(47)
You need to mirror an existing volume named mirvol1. You need to achieve the following goals: Mirror mirvol1: Should be a single mirror to the existing volume using disk mydg01: Synchronization must take place in the background: To meet the required goal, you execute the following command: vxassist -g mydg -b make mirror mirvol1 \ use_storage=' "DM"="mydg01" Which of the defined goals have been met?
(Multiple Choice)
4.8/5  (30)
(30)
What is the Symantec recommended best practice for testing a Data Protection policy?
(Multiple Choice)
4.9/5  (38)
(38)
Which two (2) events or methods allow the administrator to create a backup of Notification Server cryptographic keys? (Choose two.)
(Multiple Choice)
4.8/5  (39)
(39)
A medium-sized organization with 10,000 users at Site A and 20,000 users at Site B wants to use ATP: Network to scan internet traffic at both sites. Which physical appliances should the organization use to act as a network scanner at each site while using the fewest appliances and assuming typical network usage?
(Multiple Choice)
4.8/5  (27)
(27)
Which detection method identifies a file as malware after SEP has queried the file's reputation?
(Multiple Choice)
4.8/5  (40)
(40)
How does the ProxySG handle a rule that contains a syntax error when the ProxySG processes installed policy as part of a client transaction? (Choose the best answer.)
(Multiple Choice)
4.8/5  (36)
(36)
What are two policy requirements for using the Isolate and Rejoin features in ATP? (Choose two.)
(Multiple Choice)
4.7/5  (40)
(40)
How does an attacker use a zero-day vulnerability during the Incursion phase?
(Multiple Choice)
4.8/5  (44)
(44)
You have designed a tiered storage environment using ISP volumes. You have also created the disk group that will be used to hold the tiered volumes. You now want to apply the appropriate tags to the disks. What should you do?
(Multiple Choice)
4.8/5  (38)
(38)
An ATP Administrator set up ATP: Network in TAP mode and has placed URLs on the blacklist. What will happen when a user attempts to access one of the blacklisted URLs?
(Multiple Choice)
4.7/5  (31)
(31)
While working under VxVM control, you discover that the vxplex command has failed because a previously attached plex did not complete. You get the following error messagE. "VxVM vxplex ERROR V-5-1-809 Plex plex1 in volume volume1 is locked by another utility." You must resolve this error with minimum administrative effort. How should you resolve this error?
(Multiple Choice)
4.8/5  (28)
(28)
What is the primary benefit of using Integrated Windows Authentication (IWA) authentication realms? (Choose the best answer.)
(Multiple Choice)
4.8/5  (31)
(31)
Why is it important for an Incident Responder to copy malicious files to the ATP file store or create an image of the infected system during the Recovery phase?
(Multiple Choice)
4.9/5  (43)
(43)
Showing 141 - 160 of 409
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)