Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)
Exam 1: Administration of Symantec Endpoint Protection 14 (Broadcom)165 Questions
Exam 2: Administration of Symantec Email Security.cloud (v1)113 Questions
Exam 3: Administration of Symantec Data Loss Prevention 12 (Broadcom)98 Questions
Exam 4: Administration of Symantec ProxySG 6.7138 Questions
Exam 5: Symantec Messaging Gateway 10.5 Technical Assessment (Broadcom)409 Questions
Select questions type
In which type of physical deployment does a ProxySG have potential visibility to all traffic through the use of a device such as WCCP-capable router or a Layer 4 switch? (Choose the best answer.)
(Multiple Choice)
4.8/5  (35)
(35)
An administrator is tasked with implementing an IT Management Suite 8.1 solution that will centrally manage 30,000 endpoints. Which is the best architecture to support this environment?
(Multiple Choice)
4.8/5  (46)
(46)
An administrator is applying a newly created agent configuration to an Endpoint server. Upon inspection, the new configuration is unassigned in the Endpoint Server Details. What is a possible cause for the new configuration failing to be assigned?
(Multiple Choice)
4.8/5  (34)
(34)
Which two non-Symantec methods for restricting traffic are available to the Incident Response team? (Choose two.)
(Multiple Choice)
4.9/5  (40)
(40)
What is the primary vector for the delivery of Advanced Persistent Threats, per the Internet Security Threat Reports from 2016 through 2018?
(Multiple Choice)
4.8/5  (31)
(31)
Which information is required in order to release an email from the Malware Quarantine?
(Multiple Choice)
4.9/5  (34)
(34)
An Incident Responder runs an endpoint search on a client group with 100 endpoints. After one day, the responder sees the results for 90 endpoints. What is a possible reason for the search only returning results for 90 of 100 endpoints?
(Multiple Choice)
4.8/5  (36)
(36)
What should an Incident Responder do to mitigate a false positive?
(Multiple Choice)
4.8/5  (35)
(35)
ou have gathered file I/O performance data from an Oracle Enterprise database. The database is using one filesystem on a striped volume. You want to use the performance data to adjust the system configuration to ensure efficient use of system resources. Which specific activity should you should perform to adjust the system configuration?
(Multiple Choice)
4.8/5  (43)
(43)
Which two (2) fields are essential to tracking assets when creating a warranty contract in IT Management Suite 8.1? (Choose two.)
(Multiple Choice)
4.7/5  (25)
(25)
While working with Veritas Storage Foundation for Oracle, you execute the command set #vxtunefs -s -o qui_cache_enable=1 /db01. What will be the output of this command?
(Multiple Choice)
4.8/5  (37)
(37)
Refer to the exhibit. 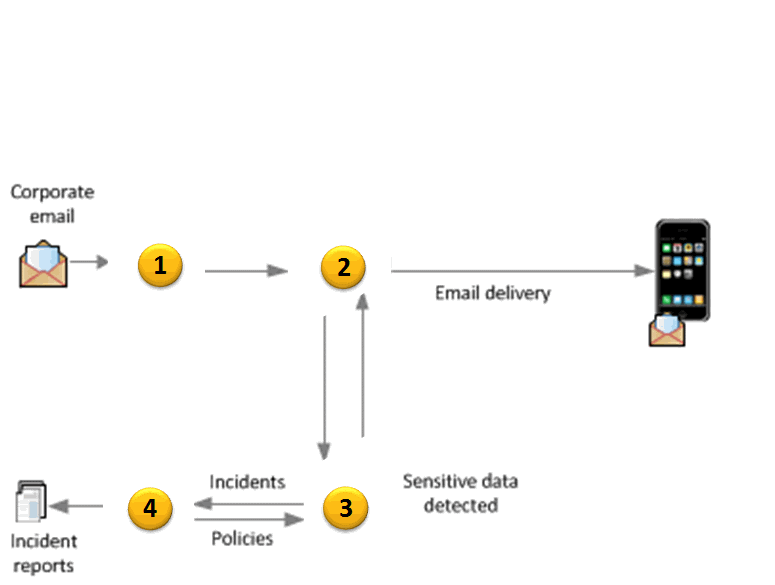 An administrator needs to implement a Mobile Email Monitor solution to inspect corporate emails on mobile devices. Where should the administrator place the web proxy?
An administrator needs to implement a Mobile Email Monitor solution to inspect corporate emails on mobile devices. Where should the administrator place the web proxy?
(Multiple Choice)
4.8/5  (37)
(37)
What does Address Registration protect against within the Email Security.cloud solution?
(Multiple Choice)
4.8/5  (44)
(44)
Which best practice does Symantec recommend with the Endpoint Detection and Response feature?
(Multiple Choice)
4.7/5  (35)
(35)
The vxprint command output for volume vol07 indicates that it has three plexes. How will you determine which plexes are used for data?
(Multiple Choice)
4.8/5  (40)
(40)
Which scanning technology will create an Advanced Threat Incident within ClientNet?
(Multiple Choice)
4.8/5  (42)
(42)
You are assessing a volume configuration in an attempt to improve its performance. You notice that the redo logs are on VxVM RAID-5 volume with user tablespaces and data files. You want to ensure that redo logs are stored as the best practices and guidelines. What should you do?
(Multiple Choice)
4.9/5  (26)
(26)
What is the maximum number of computers that could be adequately managed for an "on-box" installation of the Microsoft SQL Server with Notification Server?
(Multiple Choice)
4.9/5  (41)
(41)
Which two (2) environments will IP surrogate credentials NOT work in? (Choose two.)
(Multiple Choice)
4.8/5  (33)
(33)
Which two user roles allow an Incident Responder to blacklist or whitelist files using the ATP manager? (Choose two.)
(Multiple Choice)
4.8/5  (47)
(47)
Showing 161 - 180 of 409
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)