Exam 12: Managing Systems Support and Security
Exam 1: Introduction to Systems Analysis and Design112 Questions
Exam 2: Analyzing the Business Case112 Questions
Exam 3: Managing Systems Projects112 Questions
Exam 4: Requirements Modeling112 Questions
Exam 5: Data and Process Modeling112 Questions
Exam 6: Object Modeling112 Questions
Exam 7: Development Strategies112 Questions
Exam 8: User Interface Design112 Questions
Exam 9: Data Design112 Questions
Exam 10: System Architecture111 Questions
Exam 11: Managing Systems Implementation112 Questions
Exam 12: Managing Systems Support and Security112 Questions
Exam 13: Communication Tools45 Questions
Exam 14: CASE Tools44 Questions
Exam 15: Financial Analysis Tools44 Questions
Exam 16: Internet Resource Tools45 Questions
Select questions type
____________________ refers to the practice of storing backup media away from the main business location, in order to mitigate the risk of a catastrophic disaster such as a flood, fire, or earthquake.
(Short Answer)
4.8/5  (39)
(39)
The ____ describes the system at the beginning of system operation and includes the results of performance and acceptance tests for the operational system.
(Multiple Choice)
4.7/5  (37)
(37)
____ is a process for controlling changes in system requirements during software development.
(Multiple Choice)
4.7/5  (35)
(35)
Commercial software suppliers provide maintenance releases, often called ____________________.
(Short Answer)
4.8/5  (23)
(23)
Another of Jamal's clients has software that is so outdated that it has become increasingly vulnerable to attack. How does Jamal categorize this threat?
(Multiple Choice)
4.8/5  (41)
(41)
In a typical system, the initial version of the system is 1.0, and the release that includes the first set of maintenance changes is version ____.
(Multiple Choice)
4.9/5  (34)
(34)
Indications that a system has reached the end of its economically useful life include ____.
(Multiple Choice)
4.8/5  (37)
(37)
Although the procedures for corrective maintenance and adaptive maintenance are alike, minor corrective maintenance requires more IT department resources than minor adaptive maintenance.
(True/False)
4.7/5  (35)
(35)
The most recent wireless security enhancement, ____________________, further strengthens the level of wireless protection.
(Short Answer)
4.9/5  (39)
(39)
Another of Jamal's clients describes a situation in which a caller to their help desk pretended to be a legitimate user and requested that his password to his company account be changed. How does Jamal categorize this incident?
(Multiple Choice)
4.9/5  (35)
(35)
If significant changes take place in an existing system or if a new version is released, the IT department might develop a ____.
(Multiple Choice)
4.8/5  (34)
(34)
To provide security for network traffic, data can be ____________________, which refers to a process of encoding the data so it cannot be accessed without authorization.
(Short Answer)
4.8/5  (34)
(34)
Risk ____ develops safeguards that reduce risks and their impact.
(Multiple Choice)
4.9/5  (37)
(37)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-In risk control, this shifts the risk to another asset or party.
(Multiple Choice)
4.7/5  (39)
(39)
As the first step in capacity planning, analysts develop a current model based on the system's present workload and performance specifications.
(True/False)
4.9/5  (46)
(46)
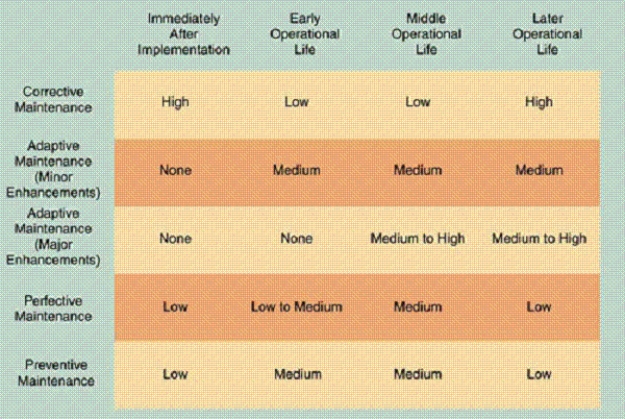 -As shown in the accompanying figure, ____ when it becomes clear that the company plans to replace the system.
-As shown in the accompanying figure, ____ when it becomes clear that the company plans to replace the system.
(Multiple Choice)
4.9/5  (29)
(29)
____ describes the amount of data that a system can transfer in a fixed time period.
(Multiple Choice)
4.9/5  (37)
(37)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-In risk control, this reduces the impact of a risk by careful planning and preparation.
(Multiple Choice)
4.8/5  (46)
(46)
Showing 61 - 80 of 112
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)