Exam 12: Managing Systems Support and Security
Exam 1: Introduction to Systems Analysis and Design112 Questions
Exam 2: Analyzing the Business Case112 Questions
Exam 3: Managing Systems Projects112 Questions
Exam 4: Requirements Modeling112 Questions
Exam 5: Data and Process Modeling112 Questions
Exam 6: Object Modeling112 Questions
Exam 7: Development Strategies112 Questions
Exam 8: User Interface Design112 Questions
Exam 9: Data Design112 Questions
Exam 10: System Architecture111 Questions
Exam 11: Managing Systems Implementation112 Questions
Exam 12: Managing Systems Support and Security112 Questions
Exam 13: Communication Tools45 Questions
Exam 14: CASE Tools44 Questions
Exam 15: Financial Analysis Tools44 Questions
Exam 16: Internet Resource Tools45 Questions
Select questions type
____ costs include expenses for items such as supplies, equipment rental, and software leases.
(Multiple Choice)
4.7/5  (38)
(38)
One of Jamal's clients reports that the traffic on their network is being intercepted and scanned for valuable information. How does Jamal categorize this incident?
(Multiple Choice)
5.0/5  (35)
(35)
____ shifts the risk to another asset or party, such as an insurance company, in risk control.
(Multiple Choice)
4.8/5  (48)
(48)
Companies with limited resources always consider new systems development, adaptive maintenance, and corrective maintenance less important than perfective maintenance.
(True/False)
4.8/5  (36)
(36)
The use of a(n) ____________________ password requires that the password be entered before the computer can be started.
(Short Answer)
4.8/5  (35)
(35)
Requests for corrective and adaptive maintenance normally come from the IT department, while users usually initiate perfective maintenance.
(True/False)
4.7/5  (34)
(34)
When corrective action cannot occur immediately, users appreciate feedback from the system administrator and should be kept informed of any decisions or actions that affect their maintenance requests.
(True/False)
4.8/5  (40)
(40)
MATCHING
Identify the letter of the choice that best matches the phrase or definition.
-Uses analytical techniques to identify potential quality and performance improvements in an information system.
(Multiple Choice)
4.9/5  (43)
(43)
What is capacity planning? Include an explanation of what-if analysis in your answer.
(Essay)
4.8/5  (31)
(31)
____ prevents unauthorized users from creating, modifying, or deleting information.
(Multiple Choice)
4.9/5  (36)
(36)
____________________ means that in normal operating conditions, any transaction that occurs on the primary system must automatically propagate to the hot site.
(Short Answer)
4.8/5  (26)
(26)
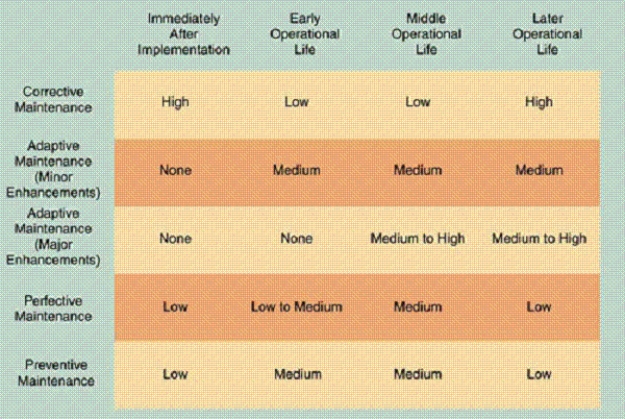 -As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor ____ maintenance.
-As shown in the accompanying figure, once a system becomes stable, maintenance costs usually remain low and involve minor ____ maintenance.
(Multiple Choice)
5.0/5  (38)
(38)
 -As shown in the accompanying figure, maintenance expenses usually are high when a system is implemented because problems must be detected, investigated, and resolved by ____ maintenance.
-As shown in the accompanying figure, maintenance expenses usually are high when a system is implemented because problems must be detected, investigated, and resolved by ____ maintenance.
(Multiple Choice)
4.9/5  (39)
(39)
Using software ____________________ techniques, an analyst can analyze a system's quality or performance.
(Short Answer)
4.9/5  (23)
(23)
____ ensures that authorized users have timely and reliable access to necessary information.
(Multiple Choice)
4.9/5  (36)
(36)
When a(n) ____________________ is used, all noncritical changes to a system are held until they can be implemented at the same time.
(Short Answer)
4.8/5  (35)
(35)
Depending on the system, bandwidth might be measured in any of the following except ____.
(Multiple Choice)
4.8/5  (32)
(32)
IT staff members usually initiate requests for perfective and preventive maintenance.
(True/False)
4.9/5  (44)
(44)
Showing 81 - 100 of 112
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)