Exam 8: Discovering Computers: Operating Systems and Utility Programs
Exam 1: Microsoft Windows Internet Explorer 8 : Introduction to Internet Explorer112 Questions
Exam 2: Office 2010 and Windows 7 : essential concepts and skills112 Questions
Exam 3: Access : Databases and Database Objects : an Introduction112 Questions
Exam 4: Access: Querying a Database224 Questions
Exam 5: Discovering Computers: Introduction to Computers112 Questions
Exam 6: Discovering Computers: the Internet and World Wide Web112 Questions
Exam 7: Discovering Computers: Application Software112 Questions
Exam 8: Discovering Computers: Operating Systems and Utility Programs112 Questions
Exam 9: Discovering Computers: Computer Security and Safety, Ethics, and Privacy112 Questions
Exam 10: Excel : Creating a Worksheet and an Embedded Chart112 Questions
Exam 11: Excel : Formulas, Functions, and Formatting112 Questions
Exam 12: Excel : What-If Analysis, Charting and Working With Large Worksheets112 Questions
Exam 13: Powerpoint : Creating and Editing a Presentation With Clip Art112 Questions
Exam 14: Powerpoint : Enhancing a Presentation With Pictures, Shapes and Wordart112 Questions
Exam 15: Powerpoint : Reusing a Presentation With Adding Media112 Questions
Exam 16: Word: Creating, Formatting, and Editing a Word Document With Pictures112 Questions
Exam 17: Word: Creating a Research Paper With Citations and References112 Questions
Exam 18: Word: Creating a Business Letter With a Letterhead and Table112 Questions
Select questions type
____ is a scam in which a perpetrator attempts to obtain your personal and/or financial information.
(Multiple Choice)
4.9/5  (38)
(38)
A(n)Internet spy removes or blocks certain items from being displayed.
(True/False)
4.9/5  (39)
(39)
____ is a program that displays an online advertisement in a banner or pop-up window on Web pages, e-mail, or other Internet services.
(Multiple Choice)
4.7/5  (37)
(37)
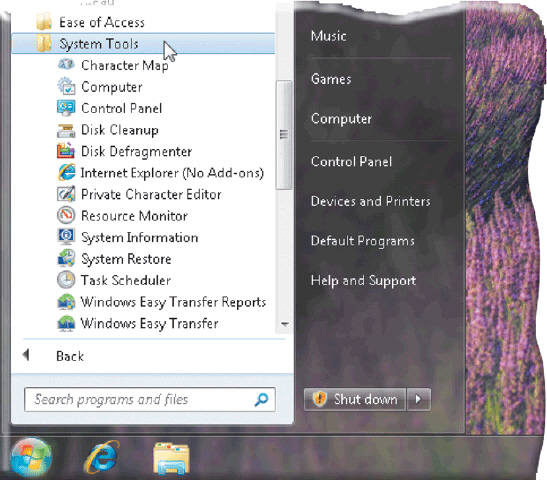 The accompanying figure lists a few of the utilities available in Windows 7; one of the utilities available in Windows 7, a disk ____ utility searches for and removes unnecessary files.
The accompanying figure lists a few of the utilities available in Windows 7; one of the utilities available in Windows 7, a disk ____ utility searches for and removes unnecessary files.
(Multiple Choice)
4.7/5  (40)
(40)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
A private combination of characters associated with the user name that allows access to certain computer resources
Responses:
service pack
BlackBerry
user name
Correct Answer:
Premises:
Responses:
(Matching)
4.7/5  (45)
(45)
Command-line interfaces are hard to use because they require exact ____.
(Multiple Choice)
4.8/5  (41)
(41)
With a(n)____________________, you interact with menus and visual images such as buttons and other graphical objects to issue commands.
(Short Answer)
4.7/5  (29)
(29)
Identify the letter of the choice that best matches the phrase or definition.
Premises:
Operating system that runs on handheld devices supplied by RIM
Responses:
user name
performance monitor
hibernate
Correct Answer:
Premises:
Responses:
(Matching)
4.8/5  (32)
(32)
New versions of an operating system usually are ____________________ compatible.
(Short Answer)
4.7/5  (28)
(28)
A ____ operating system is a complete operating system that works on a desktop computer, a notebook computer, or mobile computing device.
(Multiple Choice)
4.7/5  (30)
(30)
A ____ is a unique combination of characters, such as letters of the alphabet or numbers, that identifies one specific user.
(Multiple Choice)
4.8/5  (30)
(30)
Some operating systems include a built-in firewall to protect the computer from unauthorized intrusions.
(True/False)
4.8/5  (35)
(35)
If a printer does not have its own internal memory or if its memory is full, the operating system's buffer holds the information waiting to print while the printer prints from the buffer at its own rate of speed.
(True/False)
4.9/5  (38)
(38)
To ____ a file, you restore a zipped file to its original form.
(Multiple Choice)
5.0/5  (38)
(38)
Showing 81 - 100 of 112
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)