Exam 11: Computer Security, Ethics, and Privacy
Exam 1: Introduction to Computers191 Questions
Exam 2: The Internet and World Wide Web191 Questions
Exam 3: Application Software191 Questions
Exam 4: The Components of the System Unit191 Questions
Exam 5: Input181 Questions
Exam 6: Output191 Questions
Exam 7: Storage191 Questions
Exam 8: Operating Systems and Utility Programs191 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management191 Questions
Exam 11: Computer Security, Ethics, and Privacy191 Questions
Exam 12: Information System Development191 Questions
Exam 13: Programming Languages and Program Development191 Questions
Exam 14: Enterprise Computing191 Questions
Exam 15: Computer Careers and Certification191 Questions
Select questions type
To remove spyware, users need to obtain a special program that can detect and delete it.
(True/False)
4.9/5  (34)
(34)
With a three-generation backup policy, the grandparent is the ____.
(Multiple Choice)
4.8/5  (34)
(34)
A more devastating type of DoS attack is the ____________________, in which multiple unsuspecting computers are used to attack multiple computer networks.
(Short Answer)
4.8/5  (39)
(39)
The ____ is the destructive event or prank a malicious-logic program is intended to deliver.
(Multiple Choice)
4.8/5  (38)
(38)
A certificate ____ is an authorized person or company that issues and verifies digital certificates.
(Multiple Choice)
4.9/5  (30)
(30)
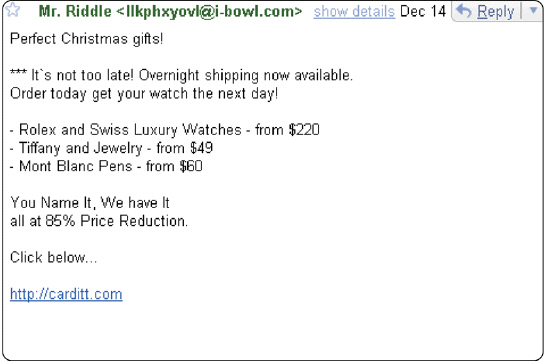 Figure 11-1 A message like the one in Figure 11-1, when sent through an instant messaging service, is called spit .
Figure 11-1 A message like the one in Figure 11-1, when sent through an instant messaging service, is called spit .
(True/False)
4.7/5  (41)
(41)
A ____ is a mathematical formula that generates a code from the contents of an e-mail message.
(Multiple Choice)
4.8/5  (32)
(32)
Phishing is an unsolicited e-mail message or newsgroup posting sent to many recipients or newsgroups at once.
(True/False)
4.9/5  (43)
(43)
Symptoms of a user with computer addiction include all of the following except ____.
(Multiple Choice)
4.7/5  (28)
(28)
Personal firewalls constantly monitor all transmissions to and from a computer and inform users of any attempted intrusion.
(True/False)
4.8/5  (41)
(41)
It is illegal for employers to use software programs that monitor employees.
(True/False)
4.8/5  (26)
(26)
To help reduce the chance of ____, physical controls such as locked doors and cables usually are adequate to protect equipment.
(Multiple Choice)
5.0/5  (38)
(38)
Critical Thinking Questions Case 1 One form of software theft is the theft of the software from software manufacturers, which is known as piracy. Because this has historically been rather easy to do, the practice has become very common. As a computer instructor you feel it is your responsibility to explain this practice to students through the use of some examples. Which of the following practice IS permissible under a EULA?
(Multiple Choice)
4.8/5  (35)
(35)
Undervoltages can cause equipment damage, but generally do not cause data loss.
(True/False)
4.8/5  (33)
(33)
A(n) ____ is a device that contains surge protection circuits and one or more batteries that can provide power during a temporary or permanent loss of power.
(Multiple Choice)
4.7/5  (30)
(30)
Computer viruses, worms, and Trojan horses deliver their payload on a computer when a user ____.
(Multiple Choice)
5.0/5  (44)
(44)
A cyberextortionist uses the Internet or network to destroy or damage computers for political reasons.
(True/False)
4.9/5  (41)
(41)
To utilize intrusion detection software requires little expertise because the programs are simple and easy to use and interpret.
(True/False)
4.9/5  (44)
(44)
A spyware program communicates information it collects to some inside source while a user is ____________________.
(Short Answer)
4.8/5  (31)
(31)
Showing 21 - 40 of 191
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)