Exam 11: Computer Security, Ethics, and Privacy
Exam 1: Introduction to Computers191 Questions
Exam 2: The Internet and World Wide Web191 Questions
Exam 3: Application Software191 Questions
Exam 4: The Components of the System Unit191 Questions
Exam 5: Input181 Questions
Exam 6: Output191 Questions
Exam 7: Storage191 Questions
Exam 8: Operating Systems and Utility Programs191 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management191 Questions
Exam 11: Computer Security, Ethics, and Privacy191 Questions
Exam 12: Information System Development191 Questions
Exam 13: Programming Languages and Program Development191 Questions
Exam 14: Enterprise Computing191 Questions
Exam 15: Computer Careers and Certification191 Questions
Select questions type
One of the more popular e-mail encryption programs is called ____, which is freeware for personal, noncommercial users.
(Multiple Choice)
4.9/5  (42)
(42)
Many systems implement access controls using a two-phase process called identification and assessment .
(True/False)
5.0/5  (26)
(26)
Carpal tunnel syndrome (CTS) is inflammation of a tendon due to some repeated motion or stress on that tendon.
(True/False)
4.8/5  (42)
(42)
Critical Thinking Questions Case 2 In your introductory course on computers, your professor has decided to dedicate a lecture to computer ethics. There is a lot of ambiguity in this topic, and she has presented a range of circumstances for you and your classmates to review. Which is NOT an issue surrounding the concept of fair use, from copyright law?
(Multiple Choice)
4.7/5  (27)
(27)
Perpetrators of back doors trick their victims into interacting with phony Web sites.
(True/False)
4.9/5  (28)
(28)
In its simplest form, a(n) ____ is a programmed formula that the recipient of encrypted data uses to decrypt the ciphertext.
(Multiple Choice)
4.9/5  (30)
(30)
Computer ____ is the discovery, collection, and analysis of evidence found on computers and networks.
(Multiple Choice)
4.7/5  (40)
(40)
A(n) ____________________ is a utility program that detects and protects a personal computer and its data from unauthorized access.
(Short Answer)
4.8/5  (37)
(37)
A standby UPS, sometimes called an offline UPS, runs constantly off the battery, which provides continuous protection.
(True/False)
4.9/5  (34)
(34)
 Figure 11-3 A program like the one in Figure 11-3 scans for programs that attempt to modify the boot program, the operating system, and other programs that normally are read from but not modified.
Figure 11-3 A program like the one in Figure 11-3 scans for programs that attempt to modify the boot program, the operating system, and other programs that normally are read from but not modified.
(True/False)
4.7/5  (33)
(33)
A(n) ____________________ has the same intent as a cracker, but does not have the technical skills and knowledge.
(Short Answer)
4.7/5  (30)
(30)
Many organizations and businesses have strict written policies governing the installation and use of software and enforce their rules by checking networked or online computers periodically to ensure that all software is licensed properly.
(True/False)
4.9/5  (35)
(35)
____________________ occurs when someone steals software media, intentionally erases software programs, or illegally copies a software program.
(Short Answer)
4.8/5  (37)
(37)
____ is/are not considered spyware because a user knows it/they exist(s).
(Multiple Choice)
4.8/5  (43)
(43)
Critical Thinking Questions Case 2 In your introductory course on computers, your professor has decided to dedicate a lecture to computer ethics. There is a lot of ambiguity in this topic, and she has presented a range of circumstances for you and your classmates to review. Which of the following is NOT a question of computer ethics?
(Multiple Choice)
4.9/5  (36)
(36)
 Figure 11-2 Many Web sites, like that in Figure 11-2, require a user to enter a(n) ____________________, which is a private combination of characters associated with a user name that allows access to certain computer resources.
Figure 11-2 Many Web sites, like that in Figure 11-2, require a user to enter a(n) ____________________, which is a private combination of characters associated with a user name that allows access to certain computer resources.
(Short Answer)
4.8/5  (37)
(37)
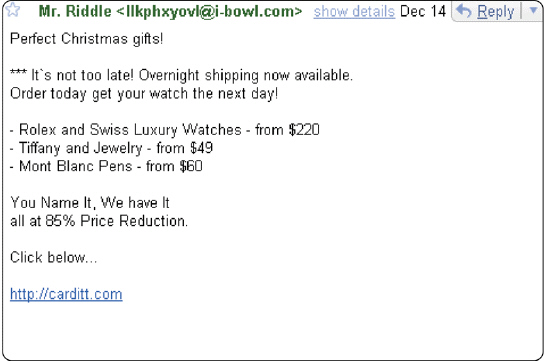 Figure 11-1 An alternative to e-mail filtering is to purchase a(n) ____________________ that attempts to remove a message like the one in Figure 11-1 before it reaches a user s inbox.
Figure 11-1 An alternative to e-mail filtering is to purchase a(n) ____________________ that attempts to remove a message like the one in Figure 11-1 before it reaches a user s inbox.
(Short Answer)
4.7/5  (32)
(32)
Showing 41 - 60 of 191
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)