Exam 11: Computer Security, Ethics, and Privacy
Exam 1: Introduction to Computers191 Questions
Exam 2: The Internet and World Wide Web191 Questions
Exam 3: Application Software191 Questions
Exam 4: The Components of the System Unit191 Questions
Exam 5: Input181 Questions
Exam 6: Output191 Questions
Exam 7: Storage191 Questions
Exam 8: Operating Systems and Utility Programs191 Questions
Exam 9: Communications and Networks181 Questions
Exam 10: Database Management191 Questions
Exam 11: Computer Security, Ethics, and Privacy191 Questions
Exam 12: Information System Development191 Questions
Exam 13: Programming Languages and Program Development191 Questions
Exam 14: Enterprise Computing191 Questions
Exam 15: Computer Careers and Certification191 Questions
Select questions type
With a(n) ____, users choose which folders and files to include in a backup.
(Multiple Choice)
4.8/5  (42)
(42)
Examples of biometric devices and systems include all of the following except ____.
(Multiple Choice)
4.8/5  (28)
(28)
A(n) ____ network, the most recent network standard, conforms to the government security standards and uses more sophisticated encryption techniques than WPA or WEP.
(Multiple Choice)
4.9/5  (30)
(30)
To promote a better understanding of software piracy problems and, if necessary, to take legal action, a number of major worldwide software companies formed the ____.
(Multiple Choice)
4.8/5  (40)
(40)
With a three-generation backup policy, the child is the ____.
(Multiple Choice)
4.9/5  (36)
(36)
A(n) ____ attack is an assault whose purpose is to disrupt computer access to an Internet service such as the Web or e-mail.
(Multiple Choice)
4.7/5  (31)
(31)
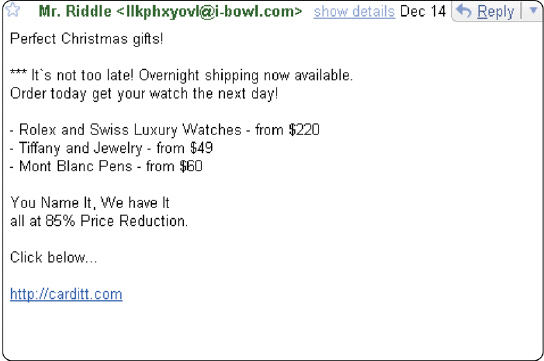 Figure 11-1 In order to safeguard personal information, you should not reply to messages like those shown in Figure 11-1 for any reason.
Figure 11-1 In order to safeguard personal information, you should not reply to messages like those shown in Figure 11-1 for any reason.
(True/False)
4.8/5  (30)
(30)
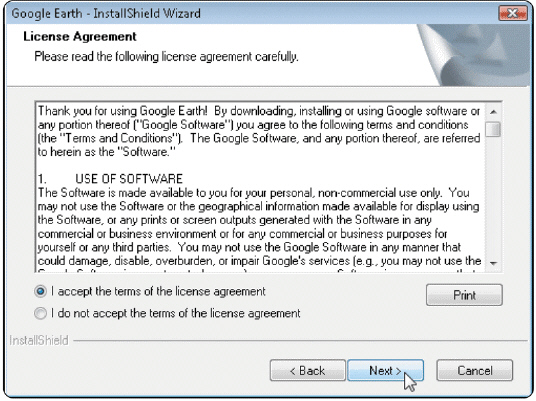 Figure 11-5 When users purchase software, a single-user license agreement like the one in Figure 11-5 permits users to do any of the following except ____.
Figure 11-5 When users purchase software, a single-user license agreement like the one in Figure 11-5 permits users to do any of the following except ____.
(Multiple Choice)
4.8/5  (33)
(33)
Programmers often build trapdoors into programs during system development.
(True/False)
4.9/5  (31)
(31)
A momentary overvoltage, called a ____, occurs when the increase in power lasts for less than one millisecond (one thousandth of a second).
(Multiple Choice)
4.9/5  (28)
(28)
The term ____, although originally a complimentary word for a computer enthusiast, now has a derogatory meaning and refers to someone who accesses a computer or network illegally.
(Multiple Choice)
4.9/5  (34)
(34)
____________________ is any unwanted signal, usually varying quickly, that is mixed with the normal voltage entering a computer.
(Short Answer)
5.0/5  (28)
(28)
Methods that guarantee a computer or network is safe from computer viruses, worms, and Trojan horses exist.
(True/False)
4.9/5  (42)
(42)
A(n) ____ is a duplicate of a file, program, or disk that can be used if the original is lost, damaged, or destroyed.
(Multiple Choice)
4.9/5  (29)
(29)
One approach to content filtering is through a rating system of ____, which is similar to those used for movies and videos.
(Multiple Choice)
4.7/5  (33)
(33)
A(n) ____ control is a security measure that defines who can access a computer, when they can access it, and what actions they can take while accessing the computer.
(Multiple Choice)
4.7/5  (37)
(37)
Most multiuser operating systems require that users correctly enter a user name and password before they can access the data, information, and programs stored on a computer network.
(True/False)
4.9/5  (38)
(38)
Showing 121 - 140 of 191
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)