Exam 5: CompTIA Cloud Essentials+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A security analyst has discovered that developers have installed browsers on all development servers in the company's cloud infrastructure and are using them to browse the Internet. Which of the following changes should the security analyst make to BEST protect the environment?
Free
(Multiple Choice)
4.8/5  (31)
(31)
Correct Answer:
A
An analyst is investigating an anomalous event reported by the SOC. After reviewing the system logs, the analyst identifies an unexpected addition of a user with root-level privileges on the endpoint. Which of the following data sources will BEST help the analyst to determine whether this event constitutes an incident?
Free
(Multiple Choice)
4.9/5  (31)
(31)
Correct Answer:
E
Which of the following session management techniques will help to prevent a session identifier from being stolen via an XSS attack?
Free
(Multiple Choice)
4.9/5  (38)
(38)
Correct Answer:
B
A security analyst is reviewing the following web server log: GET %2f..%2f..%2f.. %2f.. %2f.. %2f.. %2f../etc/passwd Which of the following BEST describes the issue?
(Multiple Choice)
4.9/5  (29)
(29)
Which of the following secure coding techniques can be used to prevent cross-site request forgery attacks?
(Multiple Choice)
4.8/5  (35)
(35)
A security analyst implemented a solution that would analyze the attacks that the organization's firewalls failed to prevent. The analyst used the existing systems to enact the solution and executed the following command: $ sudo nc -1 -v -e maildaemon.py 25 > caplog.txt Which of the following solutions did the analyst implement?
(Multiple Choice)
4.9/5  (33)
(33)
An information security analyst is reviewing backup data sets as part of a project focused on eliminating archival data sets. Which of the following should be considered FIRST prior to disposing of the electronic data?
(Multiple Choice)
4.8/5  (35)
(35)
A user receives a potentially malicious email that contains spelling errors and a PDF document. A security analyst reviews the email and decides to download the attachment to a Linux sandbox for review. Which of the following commands would MOST likely indicate if the email is malicious?
(Multiple Choice)
4.9/5  (35)
(35)
A development team uses open-source software and follows an Agile methodology with two-week sprints. Last month, the security team filed a bug for an insecure version of a common library. The DevOps team updated the library on the server, and then the security team rescanned the server to verify it was no longer vulnerable. This month, the security team found the same vulnerability on the server. Which of the following should be done to correct the cause of the vulnerability?
(Multiple Choice)
4.9/5  (26)
(26)
A security analyst is building a malware analysis lab. The analyst wants to ensure malicious applications are not capable of escaping the virtual machines and pivoting to other networks. To BEST mitigate this risk, the analyst should use __________.
(Multiple Choice)
4.9/5  (32)
(32)
A company's incident response team is handling a threat that was identified on the network. Security analysts have determined a web server is making multiple connections from TCP port 445 outbound to servers inside its subnet as well as at remote sites. Which of the following is the MOST appropriate next step in the incident response plan?
(Multiple Choice)
4.7/5  (33)
(33)
Which of the following is the MOST important objective of a post-incident review?
(Multiple Choice)
4.8/5  (31)
(31)
A company wants to establish a threat-hunting team. Which of the following BEST describes the rationale for integrating intelligence into hunt operations?
(Multiple Choice)
4.8/5  (31)
(31)
An organization used a third party to conduct a security audit and discovered several deficiencies in the cybersecurity program. The findings noted many external vulnerabilities that were not caught by the vulnerability scanning software, numerous weaknesses that allowed lateral movement, and gaps in monitoring that did not detect the activity of the auditors. Based on these findings, which of the following would be the BEST long-term enhancement to the security program?
(Multiple Choice)
4.8/5  (30)
(30)
A security analyst is reviewing the following requirements for new time clocks that will be installed in a shipping warehouse: The clocks must be configured so they do not respond to ARP broadcasts. The server must be configured with static ARP entries for each clock. Which of the following types of attacks will this configuration mitigate?
(Multiple Choice)
4.9/5  (34)
(34)
During routine monitoring, a security analyst discovers several suspicious websites that are communicating with a local host. The analyst queries for IP 192.168.50.2 for a 24-hour period: 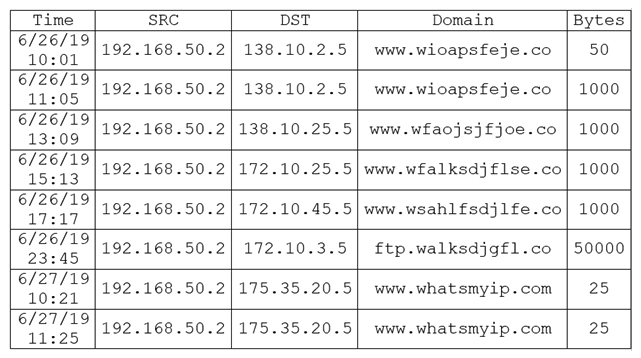 To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and __________.
To further investigate, the analyst should request PCAP for SRC 192.168.50.2 and __________.
(Multiple Choice)
4.9/5  (33)
(33)
An organization is assessing risks so it can prioritize its mitigation actions. Following are the risks and their probability and impact: 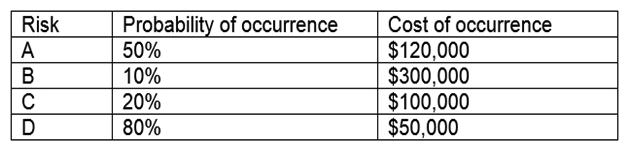 Which of the following is the order of priority for risk mitigation from highest to lowest?
Which of the following is the order of priority for risk mitigation from highest to lowest?
(Multiple Choice)
4.8/5  (31)
(31)
A product manager is working with an analyst to design a new application that will perform as a data analytics platform and will be accessible via a web browser. The product manager suggests using a PaaS provider to host the application. Which of the following is a security concern when using a PaaS solution?
(Multiple Choice)
4.8/5  (30)
(30)
A custom script currently monitors real-time logs of a SAMIL authentication server to mitigate brute-force attacks. Which of the following is a concern when moving authentication to a cloud service?
(Multiple Choice)
4.8/5  (34)
(34)
A storage area network (SAN) was inadvertently powered off while power maintenance was being performed in a datacenter. None of the systems should have lost all power during the maintenance. Upon review, it is discovered that a SAN administrator moved a power plug when testing the SAN's fault notification features. Which of the following should be done to prevent this issue from reoccurring?
(Multiple Choice)
4.7/5  (34)
(34)
Showing 1 - 20 of 165
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)