Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A systems security engineer is assisting an organization's market survey team in reviewing requirements for an upcoming acquisition of mobile devices. The engineer expresses concerns to the survey team about a particular class of devices that uses a separate SoC for baseband radio I/O. For which of the following reasons is the engineer concerned?
Free
(Multiple Choice)
4.8/5  (29)
(29)
Correct Answer:
B
A university's help desk is receiving reports that Internet access on campus is not functioning. The network administrator looks at the management tools and sees the 1Gbps Internet is completely saturated with ingress traffic. The administrator sees the following output on the Internet router: 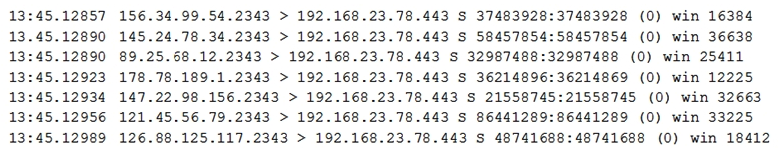 The administrator calls the university's ISP for assistance, but it takes more than four hours to speak to a network engineer who can resolve the problem. Based on the information above, which of the following should the ISP engineer do to resolve the issue?
The administrator calls the university's ISP for assistance, but it takes more than four hours to speak to a network engineer who can resolve the problem. Based on the information above, which of the following should the ISP engineer do to resolve the issue?
Free
(Multiple Choice)
4.8/5  (39)
(39)
Correct Answer:
D
A penetration tester noticed special characters in a database table. The penetration tester configured the browser to use an HTTP interceptor to verify that the front-end user registration web form accepts invalid input in the user's age field. The developer was notified and asked to fix the issue. Which of the following is the MOST secure solution for the developer to implement?
Free
(Multiple Choice)
4.8/5  (36)
(36)
Correct Answer:
B
A recent overview of the network's security and storage applications reveals a large amount of data that needs to be isolated for security reasons. Below are the critical applications and devices configured on the network: Firewall Core switches RM server Virtual environment NAC solution The security manager also wants data from all critical applications to be aggregated to correlate events from multiple sources. Which of the following must be configured in certain applications to help ensure data aggregation and data isolation are implemented on the critical applications and devices? (Select TWO).
(Multiple Choice)
4.9/5  (38)
(38)
After the departure of a developer under unpleasant circumstances, the company is concerned about the security of the software to which the developer has access. Which of the following is the BEST way to ensure security of the code following the incident?
(Multiple Choice)
4.8/5  (29)
(29)
A security architect is implementing security measures in response to an external audit that found vulnerabilities in the corporate collaboration tool suite. The report identified the lack of any mechanism to provide confidentiality for electronic correspondence between users and between users and group mailboxes. Which of the following controls would BEST mitigate the identified vulnerability?
(Multiple Choice)
4.9/5  (40)
(40)
An analyst is investigating behavior on a corporate-owned, corporate-managed mobile device with application whitelisting enabled, based on a name string. The employee to whom the device is assigned reports the approved email client is displaying warning messages that can launch browser windows and is adding unrecognized email addresses to the "compose" window. Which of the following would provide the analyst the BEST chance of understanding and characterizing the malicious behavior?
(Multiple Choice)
4.9/5  (41)
(41)
A company's security policy states any remote connections must be validated using two forms of network-based authentication. It also states local administrative accounts should not be used for any remote access. PKI currently is not configured within the network. RSA tokens have been provided to all employees, as well as a mobile application that can be used for 2FA authentication. A new NGFW has been installed within the network to provide security for external connections, and the company has decided to use it for VPN connections as well. Which of the following should be configured? (Choose two.)
(Multiple Choice)
4.8/5  (42)
(42)
A company recently implemented a new cloud storage solution and installed the required synchronization client on all company devices. A few months later, a breach of sensitive data was discovered. Root cause analysis shows the data breach happened from a lost personal mobile device. Which of the following controls can the organization implement to reduce the risk of similar breaches?
(Multiple Choice)
4.8/5  (27)
(27)
Following a complete outage of the electronic medical record system for more than 18 hours, the hospital's Chief Executive Officer (CEO) has requested that the Chief Information Security Officer (CISO) perform an investigation into the possibility of a disgruntled employee causing the outage maliciously. To begin the investigation, the CISO pulls all event logs and device configurations from the time of the outage. The CISO immediately notices the configuration of a top-of-rack switch from one day prior to the outage does not match the configuration that was in place at the time of the outage. However, none of the event logs show who changed the switch configuration, and seven people have the ability to change it. Because of this, the investigation is inconclusive. Which of the following processes should be implemented to ensure this information is available for future investigations?
(Multiple Choice)
4.9/5  (35)
(35)
Staff members are reporting an unusual number of device thefts associated with time out of the office. Thefts increased soon after the company deployed a new social networking application. Which of the following should the Chief Information Security Officer (CISO) recommend implementing?
(Multiple Choice)
4.7/5  (37)
(37)
During a security event investigation, a junior analyst fails to create an image of a server's hard drive before removing the drive and sending it to the forensics analyst. Later, the evidence from the analysis is not usable in the prosecution of the attackers due to the uncertainty of tampering. Which of the following should the junior analyst have followed?
(Multiple Choice)
4.8/5  (34)
(34)
A security analyst works for a defense contractor that produces classified research on drones. The contractor faces nearly constant attacks from sophisticated nation-state actors and other APIs. Which of the following would help protect the confidentiality of the research data?
(Multiple Choice)
4.8/5  (28)
(28)
Due to a recent breach, the Chief Executive Officer (CEO) has requested the following activities be conducted during incident response planning: Involve business owners and stakeholders Create an applicable scenario Conduct a biannual verbal review of the incident response plan Report on the lessons learned and gaps identified Which of the following exercises has the CEO requested?
(Multiple Choice)
4.9/5  (30)
(30)
A company is acquiring incident response and forensic assistance from a managed security service provider in the event of a data breach. The company has selected a partner and must now provide required documents to be reviewed and evaluated. Which of the following documents would BEST protect the company and ensure timely assistance? (Choose two.)
(Multiple Choice)
4.8/5  (29)
(29)
A security analyst has been asked to create a list of external IT security concerns, which are applicable to the organization. The intent is to show the different types of external actors, their attack vectors, and the types of vulnerabilities that would cause business impact. The Chief Information Security Officer (CISO) will then present this list to the board to request funding for controls in areas that have insufficient coverage. Which of the following exercise types should the analyst perform?
(Multiple Choice)
4.7/5  (32)
(32)
A core router was manipulated by a credentialed bypass to send all network traffic through a secondary router under the control of an unauthorized user connected to the network by WiFi. Which of the following would BEST reduce the risk of this attack type occurring?
(Multiple Choice)
4.7/5  (34)
(34)
A newly hired systems administrator is trying to connect a new and fully updated, but very customized, Android device to access corporate resources. However, the MDM enrollment process continually fails. The administrator asks a security team member to look into the issue. Which of the following is the MOST likely reason the MDM is not allowing enrollment?
(Multiple Choice)
4.7/5  (42)
(42)
A security assessor is working with an organization to review the policies and procedures associated with managing the organization's virtual infrastructure. During a review of the virtual environment, the assessor determines the organization is using servers to provide more than one primary function, which violates a regulatory requirement. The assessor reviews hardening guides and determines policy allows for this configuration. It would be MOST appropriate for the assessor to advise the organization to:
(Multiple Choice)
4.9/5  (42)
(42)
A software development manager is running a project using agile development methods. The company cybersecurity engineer has noticed a high number of vulnerabilities have been making it into production code on the project. Which of the following methods could be used in addition to an integrated development environment to reduce the severity of the issue?
(Multiple Choice)
4.9/5  (46)
(46)
Showing 1 - 20 of 442
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)