Exam 6: CompTIA CySA+ Certification Exam (CS0-002)
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
The CASB report indicates several unsanctioned SaaS applications are being used in an organization. Which of the following is the MOST likely cause?
(Multiple Choice)
4.8/5  (42)
(42)
A cloud engineer is upgrading a high-performance computing cluster for the private cloud. The existing cluster is being replaced with GPU servers. A single GPU server is capable of the same teraflops output as 10 CPU servers. The current cluster configuration is as follows: 100 quad-core CPU servers capable of producing 100 teraflops. The baseline and current usage is 100%. The new cluster was set up and benchmarked in four different configurations. Which of the following configurations will meet the baseline teraflops performance of the cluster while maintaining the current usage?
(Multiple Choice)
4.8/5  (38)
(38)
A cloud engineer received a support call indicating web apps running on an IaaS server are unavailable. The engineer took the following trouble-shooting steps: - Hypothesized the server outage is considered to be the cause of the problem. - Performed rollback of applied patches. - Ensured all web apps are running correctly. - Documented the incident. Which of the following troubleshooting methodology steps did the cloud engineer overlook?
(Multiple Choice)
4.8/5  (35)
(35)
Worldwide users from an organization are experiencing intermittent access to a global cloud application. The cloud provider availability dashboard shows all resource availability has been 100% in the last two weeks. No network outages have been reported. Which of the following should the organization's administrator do BEFORE calling the cloud provider?
(Multiple Choice)
4.8/5  (45)
(45)
A company wants to implement a public IaaS solution but also wants to address site resiliency challenges. When selecting an IaaS provider, which of the following should a cloud technician look for within the provider's capabilities to meet the requirements?
(Multiple Choice)
4.7/5  (34)
(34)
A cloud administrator is adding several accounts for new development team interns. These interns will need access to some, but not all, of the resources and will only be working over the summer. Which of the following user provisioning techniques should be used?
(Multiple Choice)
4.7/5  (34)
(34)
A company is subcontracting part of a large project to another company. Management wants to ensure that there is a secure way for employees from both companies to share data without exposing internal information to employees at the other company. Which of the following cloud models BEST serves this purpose?
(Multiple Choice)
4.9/5  (38)
(38)
A cloud service provider wants to offer hardened virtual server images for provisioning purposes. This will enable users to use only the operating system services that are allowed by the provider. Which of the following tasks are MOST appropriate for the hardening process? (Select TWO).
(Multiple Choice)
4.8/5  (42)
(42)
Since the hypervisors were upgraded to the latest version, each new deployment results in an error being displayed at the orchestrator. To troubleshoot the issue, which of the following should be done FIRST?
(Multiple Choice)
4.9/5  (38)
(38)
A CASB provides the application proxy and web application firewall to a large retailer. All access to the retailer cloud application must originate from the CASB-designated IP addresses. The CASB has known geolocations with known IP addresses. Suddenly, all customers are not able to access the retailer cloud applications. Which of the following is MOST likely the reason for the issue?
(Multiple Choice)
4.8/5  (46)
(46)
? cloud administrator uses a script to automatically restart all the servers running in the public cloud provider environment, which hosts e-commerce applications. The administrator decides to implement the same script for a similar environment that hosts the finance applications. After verifying the script is deployed to the public cloud environment for finance, the administrator schedules a job to run at 9:00 a.m. After 9:00 a.m., the administrator receives a report from the e-commerce team that the application is experiencing outages. Which of the following should the administrator do to resolve the issue?
(Multiple Choice)
4.9/5  (33)
(33)
A cloud-based web proxy is blocking key sites that a business requires for operation. After validation, the sites are legitimate, and access is required for end users to complete their work. Which of the following is the BEST solution to allow access to the sites?
(Multiple Choice)
4.9/5  (40)
(40)
A company wants to leverage a SaaS provider for its back-office services, and security is paramount. Which of the following solutions should a cloud engineer deploy to BEST meet the security requirements?
(Multiple Choice)
4.9/5  (27)
(27)
A company is in the process of evaluating cloud service providers, as it is planning to move all of its on-premises IT services to the cloud. Most of the applications are mission critical with four 9s and five 9s uptime. The area where the company is located is also prone to natural disasters. One of the main requirements is that IT services need to survive local outages as well as regional outages. One of the company's main customers is a government entity. Which of the following is the BEST way for a cloud engineer to address these requirements?
(Multiple Choice)
4.9/5  (46)
(46)
A company's security policy requires full disk encryption on all clients with preboot enabled. The encryption server is hosted, and the requirement is to push an update to all endpoints. Which of the following is the BEST method to test and apply the update with minimal disruption to end users?
(Multiple Choice)
4.8/5  (32)
(32)
An e-commerce business recently experienced a two-hour outage from its hosted web service provider. According to the SLA, the business needs to determine how much data can be restored. On which of the following service-level components should the business focus?
(Multiple Choice)
4.9/5  (36)
(36)
A company is deploying a new instant messaging app to allow for communications with external vendors. Each entity will host its own version of the application, but users must be able to talk between the companies. Which of the following security techniques would MOST likely be used to allow this to happen?
(Multiple Choice)
4.7/5  (39)
(39)
Performance on a new private cloud deployment is not meeting expectations. An engineer has determined the virtualization host is experiencing high ready/wait times. VMs with the following configurations and metrics currently reside on the host: 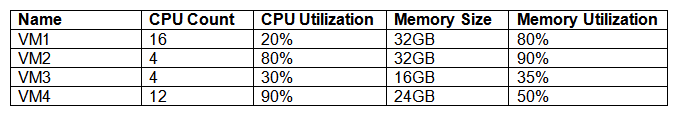 Which of the following troubleshooting choices would MOST likely be used to bring the high ready/wait times to meet the expected baseline?
Which of the following troubleshooting choices would MOST likely be used to bring the high ready/wait times to meet the expected baseline?
(Multiple Choice)
4.9/5  (42)
(42)
After scheduled network maintenance, users report that an externally hosted web application is particularly slow to load. Small items on the page load such as text documents and markup, but larger multimedia files do not load. Which of the following is the MOST likely cause of the reported issues?
(Multiple Choice)
4.8/5  (27)
(27)
A cloud provider is increasingly discovering hard-to-find issues within the growing infrastructure. The provider has all the basic necessary tools implemented to collect and store data regarding the environment. To allow the cloud provider to focus on relevant events, which of the following is the MOST appropriate technique to build intelligence?
(Multiple Choice)
4.8/5  (36)
(36)
Showing 181 - 200 of 294
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)