Exam 13: CompTIA Server+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Which of the following BEST describe the OWASP Top 10? (Choose two.)
(Multiple Choice)
4.7/5  (33)
(33)
A company is concerned that its cloud service provider is not adequately protecting the VMs housing its software development. The VMs are housed in a datacenter with other companies sharing physical resources. Which of the following attack types is MOST concerning to the company?
(Multiple Choice)
4.9/5  (31)
(31)
Which of the following expressions in Python increase a variable val by one (Choose two.)
(Multiple Choice)
4.8/5  (38)
(38)
A penetration tester was conducting a penetration test and discovered the network traffic was no longer reaching the client's IP address. The tester later discovered the SOC had used sinkholing on the penetration tester's IP address. Which of the following BEST describes what happened?
(Multiple Choice)
4.8/5  (35)
(35)
A penetration tester wants to scan a target network without being detected by the client's IDS. Which of the following scans is MOST likely to avoid detection?
(Multiple Choice)
4.9/5  (34)
(34)
A penetration tester logs in as a user in the cloud environment of a company. Which of the following Pacu modules will enable the tester to determine the level of access of the existing user?
(Multiple Choice)
4.8/5  (33)
(33)
During a penetration-testing engagement, a consultant performs reconnaissance of a client to identify potential targets for a phishing campaign. Which of the following would allow the consultant to retrieve email addresses for technical and billing contacts quickly, without triggering any of the client's cybersecurity tools? (Choose two.)
(Multiple Choice)
4.9/5  (40)
(40)
A penetration tester was able to gain access successfully to a Windows workstation on a mobile client's laptop. Which of the following can be used to ensure the tester is able to maintain access to the system?
(Multiple Choice)
4.8/5  (43)
(43)
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are: 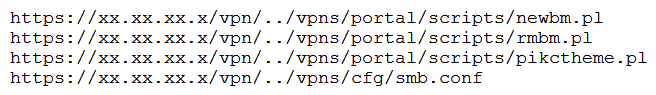 Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
(Multiple Choice)
4.9/5  (34)
(34)
A penetration tester is exploring a client's website. The tester performs a curl command and obtains the following:
* Connected to 10.2.11.144 (::1) port 80 (#0)
> GET /readmine.html HTTP/1.1
> Host: 10.2.11.144
> User-Agent: curl/7.67.0
> Accept: */*
> * Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Date: Tue, 02 Feb 2021 21:46:47 GMT
< Server: Apache/2.4.41 (Debian)
< Content-Length: 317
< Content-Type: text/html; charset=iso-8859-1
< <code><span> <</span>!DOCTYPE html <span>></span>
<span><</span>html lang="en"<span>></span> <span><head <span>></span>
<span><</span>meta name="viewport" content="width=device-width" / <span>> </span>
<span><</span>meta http-equiv="Content-Type" content="text/html; charset=utf-8" / <span>></span>
<span><</span>title <span>>WordPress › ReadMe<span><</span>/title<span>></span>
<span><</span>link rel="stylesheet" href="wp-admin/css/install.css?ver=20100228" type="text/css" /></span> <span><</span>/head> </span></code>
Which of the following tools would be BEST for the penetration tester to use to explore this site further?
(Multiple Choice)
4.8/5  (37)
(37)
A penetration tester has identified several newly released CVEs on a VoIP call manager. The scanning tool the tester used determined the possible presence of the CVEs based off the version number of the service. Which of the following methods would BEST support validation of the possible findings?
(Multiple Choice)
4.8/5  (37)
(37)
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
(Multiple Choice)
4.8/5  (39)
(39)
A penetration tester conducted a vulnerability scan against a client's critical servers and found the following: 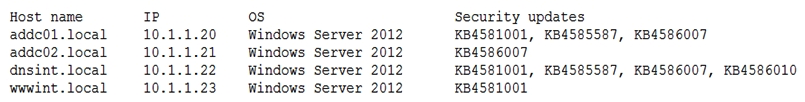 Which of the following would be a recommendation for remediation?
Which of the following would be a recommendation for remediation?
(Multiple Choice)
4.7/5  (29)
(29)
A large client wants a penetration tester to scan for devices within its network that are Internet facing. The client is specifically looking for Cisco devices with no authentication requirements. Which of the following settings in Shodan would meet the client's requirements?
(Multiple Choice)
4.9/5  (39)
(39)
A penetration tester wants to identify CVEs that can be leveraged to gain execution on a Linux server that has an SSHD running. Which of the following would BEST support this task?
(Multiple Choice)
4.7/5  (34)
(34)
The results of an Nmap scan are as follows: Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-24 01:10 EST Nmap scan report for ( 10.2.1.22 ) Host is up (0.0102s latency). Not shown: 998 filtered ports Port State Service 80/tcp open http |_http-title: 80F 22% RH 1009.1MB (text/html) |_http-slowloris-check: | VULNERABLE: | Slowloris DoS Attack | <..> Device type: bridge|general purpose Running (JUST GUESSING) : QEMU (95%) OS CPE: cpe:/a:qemu:qemu No exact OS matches found for host (test conditions non-ideal). OS detection performed. Please report any incorrect results at https://nmap.org/submit/. Nmap done: 1 IP address (1 host up) scanned in 107.45 seconds Which of the following device types will MOST likely have a similar response? (Choose two.)
(Multiple Choice)
4.9/5  (34)
(34)
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
(Multiple Choice)
4.8/5  (38)
(38)
A tester who is performing a penetration test on a website receives the following output: Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62 Which of the following commands can be used to further attack the website?
(Multiple Choice)
4.9/5  (39)
(39)
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
(Multiple Choice)
4.8/5  (30)
(30)
Showing 41 - 60 of 66
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)