Exam 13: CompTIA Server+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee's birthday, the tester gave the employee an external hard drive as a gift. Which of the following social-engineering attacks was the tester utilizing?
(Multiple Choice)
4.7/5  (33)
(33)
Which of the following should a penetration tester attack to gain control of the state in the HTTP protocol after the user is logged in?
(Multiple Choice)
4.7/5  (44)
(44)
A penetration tester performs the following command: curl -I -http2 https://www.comptia.org Which of the following snippets of output will the tester MOST likely receive?
(Multiple Choice)
4.9/5  (34)
(34)
A consultant is reviewing the following output after reports of intermittent connectivity issues: ? (192.168.1.1) at 0a:d1:fa:b1:01:67 on en0 ifscope [ethernet] ? (192.168.1.12) at 34:a4:be:09:44:f4 on en0 ifscope [ethernet] ? (192.168.1.17) at 92:60:29:12:ac:d2 on en0 ifscope [ethernet] ? (192.168.1.34) at 88:de:a9:12:ce:fb on en0 ifscope [ethernet] ? (192.168.1.136) at 0a:d1:fa:b1:01:67 on en0 ifscope [ethernet] ? (192.168.1.255) at ff:ff:ff:ff:ff:ff on en0 ifscope [ethernet] ? (224.0.0.251) at 01:02:5e:7f:ff:fa on en0 ifscope permanent [ethernet] ? (239.255.255.250) at ff:ff:ff:ff:ff:ff on en0 ifscope permanent [ethernet] Which of the following is MOST likely to be reported by the consultant?
(Multiple Choice)
4.9/5  (39)
(39)
A penetration tester is testing input validation on a search form that was discovered on a website. Which of the following characters is the BEST option to test the website for vulnerabilities?
(Multiple Choice)
4.8/5  (43)
(43)
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
(Multiple Choice)
4.9/5  (31)
(31)
Running a vulnerability scanner on a hybrid network segment that includes general IT servers and industrial control systems:
(Multiple Choice)
4.8/5  (39)
(39)
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows: • The following request was intercepted going to the network device: GET /login HTTP/1.1 Host: 10.50.100.16 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5 Connection: keep-alive Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk • Network management interfaces are available on the production network. • An Nmap scan returned the following:  Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
(Multiple Choice)
4.8/5  (37)
(37)
A client wants a security assessment company to perform a penetration test against its hot site. The purpose of the test is to determine the effectiveness of the defenses that protect against disruptions to business continuity. Which of the following is the MOST important action to take before starting this type of assessment?
(Multiple Choice)
4.9/5  (37)
(37)
The results of an Nmap scan are as follows: 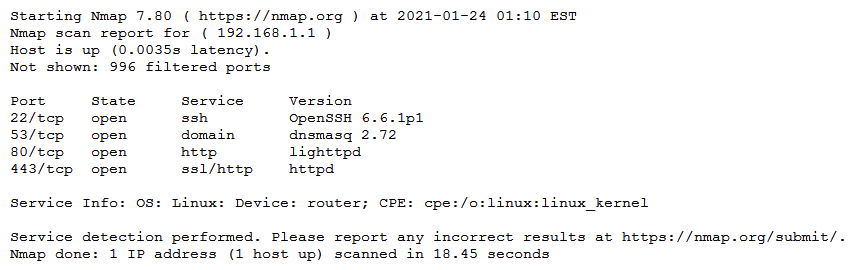 Which of the following would be the BEST conclusion about this device?
Which of the following would be the BEST conclusion about this device?
(Multiple Choice)
4.9/5  (42)
(42)
A penetration tester who is doing a security assessment discovers that a critical vulnerability is being actively exploited by cybercriminals. Which of the following should the tester do NEXT?
(Multiple Choice)
4.9/5  (42)
(42)
A company that developers embedded software for the automobile industry has hired a penetration-testing team to evaluate the security of its products prior to delivery. The penetration-testing team has stated its intent to subcontract to a reverse-engineering team capable of analyzing binaries to develop proof-of-concept exploits. The software company has requested additional background investigations on the reverse-engineering team prior to approval of the subcontract. Which of the following concerns would BEST support the software company's request?
(Multiple Choice)
4.8/5  (32)
(32)
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
(Multiple Choice)
4.9/5  (39)
(39)
When preparing for an engagement with an enterprise organization, which of the following is one of the MOST important items to develop fully prior to beginning the penetration testing activities?
(Multiple Choice)
4.8/5  (30)
(30)
A software development team is concerned that a new product's 64-bit Windows binaries can be deconstructed to the underlying code. Which of the following tools can a penetration tester utilize to help the team gauge what an attacker might see in the binaries?
(Multiple Choice)
4.9/5  (32)
(32)
A penetration tester ran an Nmap scan on an Internet-facing network device with the -F option and found a few open ports. To further enumerate, the tester ran another scan using the following command: nmap -O -A -sS -p- 100.100.100.50 Nmap returned that all 65,535 ports were filtered. Which of the following MOST likely occurred on the second scan?
(Multiple Choice)
4.7/5  (37)
(37)
In an unprotected network file repository, a penetration tester discovers a text file containing usernames and passwords in cleartext and a spreadsheet containing data for 50 employees, including full names, roles, and serial numbers. The tester realizes some of the passwords in the text file follow the format: <name-serial_number> . Which of the following would be the best action for the tester to take NEXT with this information?
(Multiple Choice)
4.9/5  (35)
(35)
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
(Multiple Choice)
4.8/5  (39)
(39)
A penetration tester is testing a web application that is hosted by a public cloud provider. The tester is able to query the provider's metadata and get the credentials used by the instance to authenticate itself. Which of the following vulnerabilities has the tester exploited?
(Multiple Choice)
4.9/5  (35)
(35)
A penetration tester writes the following script: 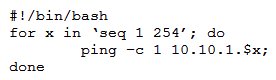 Which of the following objectives is the tester attempting to achieve?
Which of the following objectives is the tester attempting to achieve?
(Multiple Choice)
4.9/5  (34)
(34)
Showing 21 - 40 of 66
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)