Exam 16: CompTIA Security+ 2021
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A systems administrator needs to implement an access control scheme that will allow an object's access policy to be determined by its owner. Which of the following access control schemes BEST fits the requirements?
(Multiple Choice)
4.7/5  (44)
(44)
Which of the following allows for functional test data to be used in new systems for testing and training purposes to protect the real data?
(Multiple Choice)
4.8/5  (42)
(42)
When selecting a technical solution for identity management, an architect chooses to go from an in-house solution to a third-party SaaS provider. Which of the following risk management strategies is this an example of?
(Multiple Choice)
4.8/5  (39)
(39)
A security analyst is configuring a large number of new company-issued laptops. The analyst received the following requirements: The devices will be used internationally by staff who travel extensively. Occasional personal use is acceptable due to the travel requirements. Users must be able to install and configure sanctioned programs and productivity suites. The devices must be encrypted. The devices must be capable of operating in low-bandwidth environments. Which of the following would provide the GREATEST benefit to the security posture of the devices?
(Multiple Choice)
4.9/5  (51)
(51)
The Chief Financial Officer (CFO) of an insurance company received an email from Ann, the company's Chief Executive Officer (CEO), requesting a transfer of $10,000 to an account. The email states Ann is on vacation and has lost her purse, containing cash and credit cards. Which of the following social-engineering techniques is the attacker using?
(Multiple Choice)
4.7/5  (36)
(36)
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on user devices. Which of the following solutions would BEST support the policy?
(Multiple Choice)
4.8/5  (30)
(30)
Phishing and spear-phishing attacks have been occurring more frequently against a company's staff. Which of the following would MOST likely help mitigate this issue?
(Multiple Choice)
4.7/5  (33)
(33)
A security audit has revealed that a process control terminal is vulnerable to malicious users installing and executing software on the system. The terminal is beyond end-of-life support and cannot be upgraded, so it is placed on a protected network segment. Which of the following would be MOST effective to implement to further mitigate the reported vulnerability?
(Multiple Choice)
4.8/5  (42)
(42)
Which of the following are requirements that must be configured for PCI DSS compliance? (Choose two.)
(Multiple Choice)
4.7/5  (33)
(33)
A security engineer is reviewing log files after a third party discovered usernames and passwords for the organization's accounts. The engineer sees there was a change in the IP address for a vendor website one week earlier. This change lasted eight hours. Which of the following attacks was MOST likely used?
(Multiple Choice)
4.9/5  (33)
(33)
A company has drafted an insider-threat policy that prohibits the use of external storage devices. Which of the following would BEST protect the company from data exfiltration via removable media?
(Multiple Choice)
4.8/5  (29)
(29)
A user enters a password to log in to a workstation and is then prompted to enter an authentication code. Which of the following MFA factors or attributes are being utilized in the authentication process? (Choose two.)
(Multiple Choice)
4.8/5  (35)
(35)
A company recently moved sensitive videos between on-premises, company-owned websites. The company then learned the videos had been uploaded and shared to the Internet. Which of the following would MOST likely allow the company to find the cause?
(Multiple Choice)
4.8/5  (41)
(41)
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
(Multiple Choice)
4.7/5  (35)
(35)
A public relations team will be taking a group of guests on a tour through the facility of a large e-commerce company. The day before the tour, the company sends out an email to employees to ensure all whiteboards are cleaned and all desks are cleared. The company is MOST likely trying to protect against:
(Multiple Choice)
4.8/5  (36)
(36)
A university with remote campuses, which all use different service providers, loses Internet connectivity across all locations. After a few minutes, Internet and VoIP services are restored, only to go offline again at random intervals, typically within four minutes of services being restored. Outages continue throughout the day, impacting all inbound and outbound connections and services. Services that are limited to the local LAN or WiFi network are not impacted, but all WAN and VoIP services are affected. Later that day, the edge-router manufacturer releases a CVE outlining the ability of an attacker to exploit the SIP protocol handling on devices, leading to resource exhaustion and system reloads. Which of the following BEST describe this type of attack? (Choose two.)
(Multiple Choice)
4.9/5  (34)
(34)
After entering a username and password, an administrator must draw a gesture on a touch screen. Which of the following demonstrates what the administrator is providing?
(Multiple Choice)
4.8/5  (28)
(28)
An analyst visits an Internet forum looking for information about a tool. The analyst finds a thread that appears to contain relevant information. One of the posts says the following: 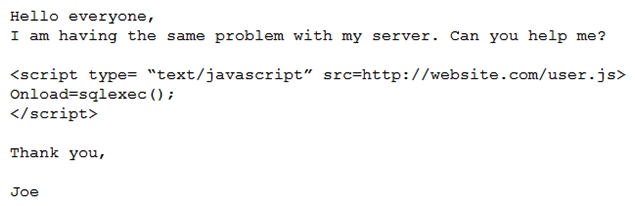 Which of the following BEST describes the attack that was attempted against the forum readers?
Which of the following BEST describes the attack that was attempted against the forum readers?
(Multiple Choice)
4.9/5  (51)
(51)
Several employees return to work the day after attending an industry trade show. That same day, the security manager notices several malware alerts coming from each of the employee's workstations. The security manager investigates but finds no signs of an attack on the perimeter firewall or the NIDS. Which of the following is MOST likely causing the malware alerts?
(Multiple Choice)
4.8/5  (41)
(41)
A company uses wireless for all laptops and keeps a very detailed record of its assets, along with a comprehensive list of devices that are authorized to be on the wireless network. The Chief Information Officer (CIO) is concerned about a script kiddie potentially using an unauthorized device to brute force the wireless PSK and obtain access to the internal network. Which of the following should the company implement to BEST prevent this from occurring?
(Multiple Choice)
4.9/5  (37)
(37)
Showing 21 - 40 of 129
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)