Exam 18: CompTIA Linux+
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A Linux systems administrator needs to provision multiple web servers into separate regional datacenters. The systems architect has instructed the administrator to define the server infrastructure using a specific tool that consumes a text-based file. Which of the following is the BEST reason to do this?
(Multiple Choice)
4.8/5  (39)
(39)
When requesting SSH access to a remote system, a user accidentally emailed the id_rsa key to the administrator. Which of the following should the user do NEXT?
(Multiple Choice)
4.9/5  (29)
(29)
A systems administration team has decided to treat their systems as immutable instances. They keep the desired state of each of their systems in version control and apply automation whenever they provision a new instance. If there is an issue with one of their servers, instead of troubleshooting the issue, they terminate the instance and rebuild it using automation. Which of the following is this an example of?
(Multiple Choice)
4.8/5  (38)
(38)
A technician wants to secure a sensitive workstation by ensuring network traffic is kept within the local subnet. To accomplish this task, the technician executes the following command: echo 0 > /proc/sys/net/ipv4/ip_default_ttl Which of the following commands can the technician use to confirm the expected results? (Choose two.)
(Multiple Choice)
4.7/5  (36)
(36)
An administrator reviews the following configuration file provided by a DevOps engineer: 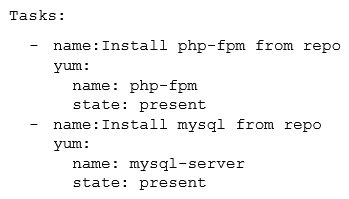 Which of the following would the application parsing this file MOST likely have to support?
Which of the following would the application parsing this file MOST likely have to support?
(Multiple Choice)
4.8/5  (28)
(28)
A user receives an access_denied error when trying to modify a file, even though the file permissions are set to 777. Which of the following commands should be used to view additional file permissions?
(Multiple Choice)
4.9/5  (47)
(47)
A company wants to provide internal identity verification services for networked devices. Which of the following servers should be installed?
(Multiple Choice)
5.0/5  (32)
(32)
A junior Linux administrator is updating local name resolution to support IPv6. The administrator issues the command cat /etc/hosts and receives the following output: 127.0.0.1 localhost Which of the following actions should the administrator perform to accomplish this task?
(Multiple Choice)
4.9/5  (37)
(37)
A Linux systems administrator needs to set permissions on an application with the following parameters: The owner of the application should be able to read, write, and execute the application. Members of the group should be able to read and execute the application. Everyone else should not have access to the application. Which of the following commands would BEST accomplish these tasks?
(Multiple Choice)
4.8/5  (47)
(47)
A systems administrator notices several intensive tasks executing from users Joe and Ann. These processes are impacting server operations but must be allowed to continue running. Which of the following commands should the systems administrator run to reduce the impact on the server?
(Multiple Choice)
4.8/5  (32)
(32)
An administrator notices that a long-running script, /home/ user /script.sh , is taking up a large number of system resources. The administrator does not know the script's function. Which of the following commands should the administrator use to minimize the script's impact on system resources?
(Multiple Choice)
4.8/5  (40)
(40)
A user wants to list the lines of a log, adding a correlative number at the beginning of each line separated by a set of dashes from the actual message. Which of the following scripts will complete this task?
(Multiple Choice)
4.7/5  (35)
(35)
A systems administrator needs to conduct maintenance on a server. Which of the following commands will place the administrator in the appropriate runlevel?
(Multiple Choice)
4.9/5  (33)
(33)
A four-drive Linux NAS has been improperly configured. Each drive has a capacity of 6TB, for a total storage capacity of 24TB. To reconfigure this unit to be not pluggable for drive replacement and provide total storage of 11TB to 12TB, which of the following would be the correct RAID configuration?
(Multiple Choice)
4.9/5  (39)
(39)
An administrator is analyzing a Linux server which was recently hacked. Which of the following will the administrator use to find all unsuccessful login attempts?
(Multiple Choice)
4.8/5  (43)
(43)
A company wants to ensure that all newly created files can be modified only by their owners and that all new directory content can be changed only by the creator of the directory. Which of the following commands will help achieve this task?
(Multiple Choice)
4.9/5  (35)
(35)
An administrator is troubleshooting an application that has failed to start after the server was rebooted. Noticing the data volume is not mounted, the administrator attempts to mount it and receives this error: 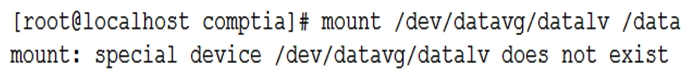 Upon checking the logical volume status, the administrator receives this information:
Upon checking the logical volume status, the administrator receives this information: 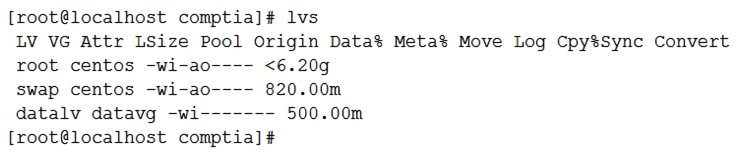 Which of the following can be said about the data logical volume, and how can this problem be resolved?
Which of the following can be said about the data logical volume, and how can this problem be resolved?
(Multiple Choice)
4.8/5  (37)
(37)
A Linux team is using Git to version a set of custom scripts. A team member has made an update to a script and published the changes to the repository. Which of the following is the BEST way to retrieve the latest changes to the administrator's local working copy?
(Multiple Choice)
5.0/5  (29)
(29)
A junior systems administrator needs to make a packet capture file that will only capture HTTP protocol data to a file called test.pcap . Which of the following commands would allow the administrator to accomplish this task?
(Multiple Choice)
4.7/5  (32)
(32)
A new user has been added to a Linux machine. Which of the following directories would contain the user's default files?
(Multiple Choice)
4.9/5  (39)
(39)
Showing 61 - 80 of 252
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)