Exam 22: Computer Benefits and Risks
Exam 1: Computer Hardware75 Questions
Exam 2: Peripheral Devices75 Questions
Exam 3: System and Application Software75 Questions
Exam 4: Installing Software75 Questions
Exam 5: Getting Started With Windows75 Questions
Exam 6: Working With Windows Settings and Accounts75 Questions
Exam 7: Working With Files75 Questions
Exam 8: Getting Started With Application Software75 Questions
Exam 9: Creating a Document75 Questions
Exam 10: Formatting a Document75 Questions
Exam 11: Finalizing a Document75 Questions
Exam 12: Creating a Worksheet75 Questions
Exam 13: Formatting a Worksheet75 Questions
Exam 14: Finalizing a Worksheet75 Questions
Exam 15: Creating a Presentation75 Questions
Exam 16: Finalizing a Presentation75 Questions
Exam 17: Creating a Database75 Questions
Exam 18: Finalizing a Database75 Questions
Exam 19: Networks75 Questions
Exam 20: Working With E-Mail75 Questions
Exam 21: Browsing the Web75 Questions
Exam 22: Computer Benefits and Risks75 Questions
Select questions type
All of the following are steps computer owners should take to have a positive effect on the environment, EXCEPT _____.
(Multiple Choice)
4.8/5  (40)
(40)
Digital certificates can be attached to software, but NOT to a document or e-mail.
(True/False)
4.9/5  (36)
(36)
A virus pattern is a section of a virus program that can be used to identify a known virus.
(True/False)
4.8/5  (43)
(43)
Case-Based Critical Thinking Questions Case 22-1 Ethan is in charge of Internet security for a small company. Employees are often asking him questions related to their identity and privacy online, as well as about some phishing schemes. Below are three of these questions. I have received an e-mail that warns about a devastating new virus, tells how to remove it, and encourages me to notify all my friends. What is this e-mail called?
(Multiple Choice)
4.8/5  (37)
(37)
Malicious code can slip into your computer only through unknown Web sites.
(True/False)
4.9/5  (48)
(48)
____________________ software is a set of utility programs that looks for and eradicates viruses, Trojan horses, worms, and other malware.
(Short Answer)
4.9/5  (28)
(28)
Which of the following files is most likely to contain a hidden virus?
(Multiple Choice)
4.8/5  (46)
(46)
Which of the following is a computer program that seems to perform one function while actually doing something else?
(Multiple Choice)
4.8/5  (35)
(35)
A _____ is malicious software designed to spread from computer to computer over local area networks and the Internet.
(Multiple Choice)
4.8/5  (37)
(37)
Privacy violations take place only when you distribute your personal information over the Internet.
(True/False)
4.9/5  (32)
(32)
The original wireless encryption was called _____ because it was designed to provide a level of confidentiality similar to that of a wired network.
(Multiple Choice)
4.9/5  (36)
(36)
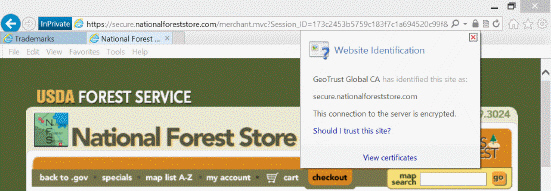 Referring to the accompanying figure, which of the following icons should you click to view a digital certificate?
Referring to the accompanying figure, which of the following icons should you click to view a digital certificate?
(Multiple Choice)
4.8/5  (31)
(31)
You can use a music clip or a photo on your Web site without the author's permission.
(True/False)
4.7/5  (40)
(40)
The term Intellectual property refers to intangibles, such as ideas, music, art, photos, logos, movies, and programs, that are the result of creativity and intellectual effort.
(True/False)
4.8/5  (38)
(38)
Which of the following is a major online privacy threat today?
(Multiple Choice)
4.7/5  (31)
(31)
To configure Internet Explorer to block third-party cookies, you should first select Internet Options from the Settings menu, then select the _____ tab.
(Multiple Choice)
4.8/5  (32)
(32)
The data carried by Wi-Fi signals can be encrypted with all of the following, EXCEPT _____.
(Multiple Choice)
4.9/5  (37)
(37)
A(n) worm is a computer program that seems to perform one function while actually doing something else.
(True/False)
4.7/5  (41)
(41)
Showing 21 - 40 of 75
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)