Exam 2: CompTIA A+ Certification Exam: Core 2
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Which of the following operating systems utilizes the web browser named Edge, replacing its older browser software?
(Multiple Choice)
4.8/5  (35)
(35)
A company's security policy does not allow USB drives to be available in workstations. However, an exception needs to be made for a user. The network administrator changes the policy for the user. Which of the following commands should the administrator run on the user's workstation?
(Multiple Choice)
4.9/5  (29)
(29)
A customer's computer is having difficulty opening programs and regularly receives error messages regarding low system resources. Which of the following performance setting changes would BEST help the customer temporarily until a proper upgrade can be made?
(Multiple Choice)
4.8/5  (38)
(38)
A folder on an NTFS volume has the following permissions enabled for the administrators group: full control, modify, and write. A technician adds a permissions entry to the folder's security settings, denying the administrators group write and modify access. Which of the following permissions will the administrators group effectively have? (Choose two.)
(Multiple Choice)
4.7/5  (42)
(42)
A desktop technician is attempting to upgrade several machines to Windows 10. After realizing there is only one disc for the installation, the technician decides to upgrade over the network. Which of the following boot methods initiates such an upgrade?
(Multiple Choice)
4.7/5  (36)
(36)
A technician is troubleshooting an issue affecting all company laptops. All the laptops have exactly the same hardware. The screens present glitches every time the users move their mouse pointers over the screen. The technician discovers there was a recent OS update deployed throughout the company, which includes new versions for video drivers. Restarting the laptop in safe mode will not present the issue. Which of the following should the technician do NEXT?
(Multiple Choice)
4.9/5  (29)
(29)
An executive has contacted you through the help-desk chat support about an issue with a mobile device. Assist the executive to help resolve the issue. INSTRUCTIONS Select the MOST appropriate statement for each response. If at any time you would like to bring back the initial state of the simulation, please click the Reset All button. 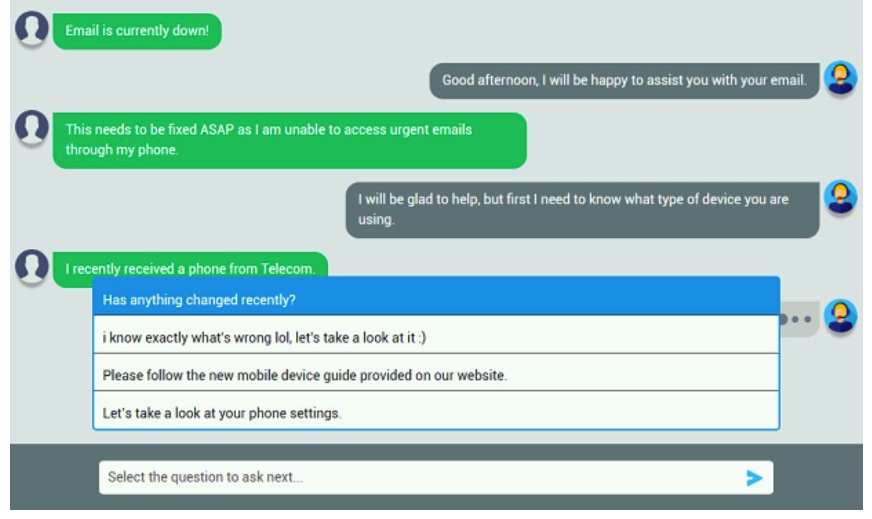 Let's take a look at your phone settings.
Let's take a look at your phone settings. 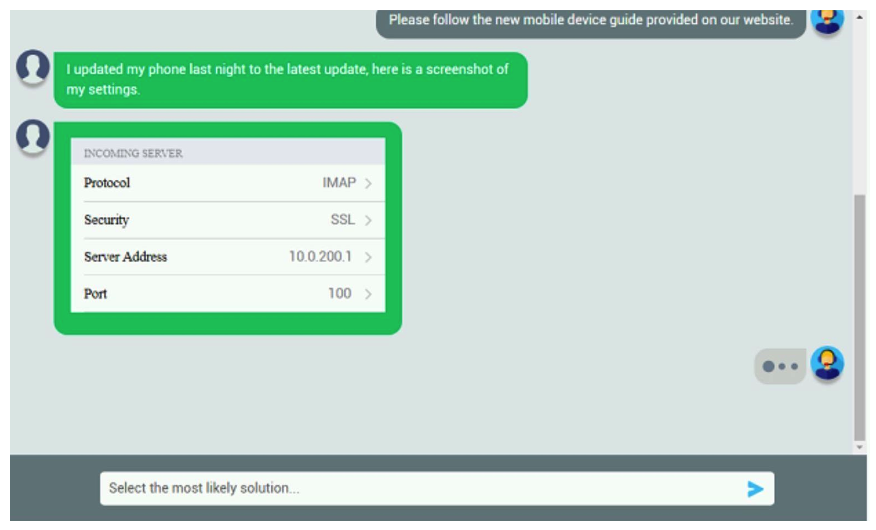
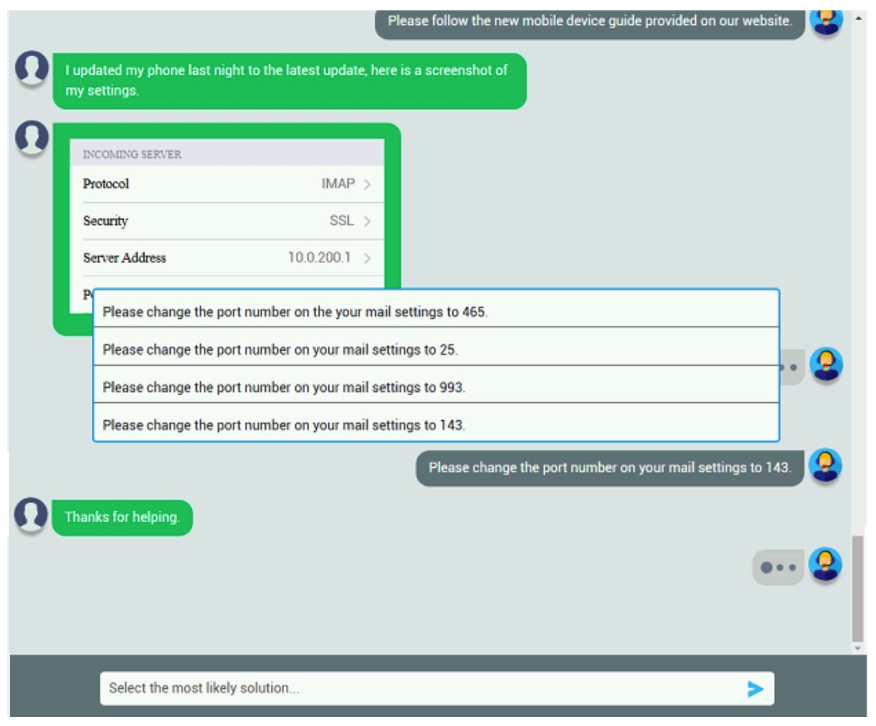 Please change the port number on your mail settings to 993. Which of the following should be done NEXT?
Please change the port number on your mail settings to 993. Which of the following should be done NEXT?
(Multiple Choice)
4.8/5  (36)
(36)
An application is installed and configured locally on a workstation, but it writes all the save files to a different workstation on the network. Which of the following accurately describes the configuration of the application?
(Multiple Choice)
4.8/5  (37)
(37)
An employee contacts the help desk because the battery in a company-provided smartphone lasts only a short period of time when the worker is in the office. Which of the following would MOST likely reduce this symptom? (Select TWO).
(Multiple Choice)
4.8/5  (33)
(33)
With which of the following types is a man-in-the-middle attack associated?
(Multiple Choice)
4.9/5  (38)
(38)
A security team is auditing a company's network logs and notices that a USB drive was previously inserted into several of the servers. Many login attempts were then successfully performed using common login information. Which of the following actions should be taken to close the vulnerability? (Select two.)
(Multiple Choice)
4.7/5  (27)
(27)
Users notify the help desk of an email that was just received. The email came from the help desk's email address and asked the users to click on an embedded link. This email is BEST described as:
(Multiple Choice)
4.9/5  (29)
(29)
A Mac user needs to configure a network device using a serial connection to enable a remote network connection. Which of the following utilities would MOST likely be used to make the necessary changes?
(Multiple Choice)
4.9/5  (34)
(34)
Joe, a technician, is configuring advanced security settings on a SOHO router. Joe cannot locate the settings he intends to change, but the online vendor documentation has instructions for configuring those settings. Which of the following should the technician perform?
(Multiple Choice)
4.8/5  (28)
(28)
A technician is removing malware from a workstation. The malware was installed via a phishing attack, which was initiated from a link that was included in an email. Which of the following should the technician do to address this issue? (Choose two.)
(Multiple Choice)
4.8/5  (34)
(34)
A technician is encrypting the company's laptops using BitLocker, but some of the laptops do not have a built-in TPM. Which of the following would enable the technician to use BitLocker on these machines?
(Multiple Choice)
4.8/5  (34)
(34)
A user's corporate email is missing the shared inbox folders that were present before the user went on vacation. The technician verifies the user is connected to the domain and can still send and receive email. Which of the following is MOST likely causing the missing folders issue?
(Multiple Choice)
4.9/5  (28)
(28)
Which of the following is the MOST common method of allowing outside access through a wireless SOHO router for specific program access?
(Multiple Choice)
4.8/5  (39)
(39)
A technician needs to connect to a network switch in a remote location. The technician wants to make sure the data passed over the wire is encrypted so it cannot be read by someone using a sniffer. Which of the following connection protocols should the technician use?
(Multiple Choice)
4.8/5  (38)
(38)
Several users at an office have noticed their computers have been behaving erratically over the past hour. A technician suspects there may be a network worm or a hardware failure because all the affected computers were purchased together. Which of the following should the technician perform FIRST?
(Multiple Choice)
4.8/5  (28)
(28)
Showing 21 - 40 of 409
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)