Exam 12: CompTIA PenTest+ Certification Exam
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
A penetration tester executes the following commands: 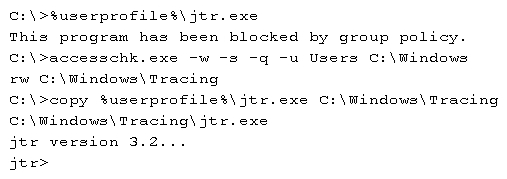 Which of the following is a local host vulnerability that the attacker is exploiting?
Which of the following is a local host vulnerability that the attacker is exploiting?
(Multiple Choice)
4.8/5  (34)
(34)
A penetration tester is performing initial intelligence gathering on some remote hosts prior to conducting a vulnerability scan. The tester runs the following command: nmap -p 192.168.1.1, 192.168.1.2, 192.168.1.3 -sV -o --max-rate 2 192.168.1.130 Which of the following BEST describes why multiple IP addresses are specified?
(Multiple Choice)
4.8/5  (42)
(42)
A penetration tester is performing initial intelligence gathering on some remote hosts prior to conducting a vulnerability scan. The tester runs the following command: nmap -D 192.168.1.1, 192.168.1.2, 192.168.1.3 -sV -o --max-rate 2 192.168.1.130 Which of the following BEST describes why multiple IP addresses are specified?
(Multiple Choice)
4.9/5  (38)
(38)
A client has requested an external network penetration test for compliance purposes. During discussion between the client and the penetration tester, the client expresses unwillingness to add the penetration tester's source IP addresses to the client's IPS whitelist for the duration of the test. Which of the following is the BEST argument as to why the penetration tester's source IP addresses should be whitelisted?
(Multiple Choice)
4.8/5  (36)
(36)
A penetration tester is performing a code review. Which of the following testing techniques is being performed?
(Multiple Choice)
5.0/5  (39)
(39)
A penetration tester runs the following on a machine: 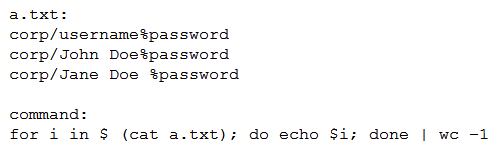 Which of the following will be returned?
Which of the following will be returned?
(Multiple Choice)
4.8/5  (35)
(35)
Which of the following would be the BEST for performing passive reconnaissance on a target's external domain?
(Multiple Choice)
4.9/5  (35)
(35)
A company hires a penetration tester to determine if there are any vulnerabilities in its new VPN concentrator installation with an external IP of 100.170.60.5. Which of the following commands will test if the VPN is available?
(Multiple Choice)
4.8/5  (40)
(40)
A consultant is performing a social engineering attack against a client. The consultant was able to collect a number of usernames and passwords using a phishing campaign. The consultant is given credentials to log on to various employees email accounts. Given the findings, which of the following should the consultant recommend be implemented?
(Multiple Choice)
4.8/5  (39)
(39)
While trying to maintain persistence on a Windows system with limited privileges, which of the following registry keys should the tester use?
(Multiple Choice)
4.9/5  (35)
(35)
A penetration tester is scanning a network for SSH and has a list of provided targets. Which of the following Nmap commands should the tester use?
(Multiple Choice)
4.8/5  (31)
(31)
A penetration tester has obtained access to an IP network subnet that contains ICS equipment intercommunication. Which of the following attacks is MOST likely to succeed in creating a physical effect?
(Multiple Choice)
4.9/5  (38)
(38)
A penetration tester observes that several high-numbered ports are listening on a public web server. However, the system owner says the application only uses port 443. Which of the following would be BEST to recommend?
(Multiple Choice)
4.9/5  (34)
(34)
During a penetration test, a tester identifies traditional antivirus running on the exploited server. Which of the following techniques would BEST ensure persistence in a post-exploitation phase?
(Multiple Choice)
4.9/5  (36)
(36)
A penetration tester is connected to a client's local network and wants to passively identify cleartext protocols and potentially sensitive data being communicated across the network. Which of the following is the BEST approach to take?
(Multiple Choice)
4.9/5  (41)
(41)
A client asks a penetration tester to add more addresses to a test currently in progress. Which of the following would define the target list?
(Multiple Choice)
4.9/5  (35)
(35)
A penetration tester used an ASP.NET web shell to gain access to a web application, which allowed the tester to pivot in the corporate network. Which of the following is the MOST important follow-up activity to complete after the tester delivers the report?
(Multiple Choice)
4.8/5  (43)
(43)
Consumer-based IoT devices are often less secure than systems built for traditional desktop computers. Which of the following BEST describes the reasoning for this?
(Multiple Choice)
4.7/5  (37)
(37)
Which of the following properties of the penetration testing engagement agreement will have the LARGEST impact on observing and testing production systems at their highest loads?
(Multiple Choice)
4.9/5  (37)
(37)
A company contracted a firm specializing in penetration testing to assess the security of a core business application. The company provided the firm with a copy of the Java bytecode. Which of the following steps must the firm take before it can run a static code analyzer?
(Multiple Choice)
4.8/5  (38)
(38)
Showing 61 - 80 of 165
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)