Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
Fill in the blank: A new license should be generated and installed in all of the following situations EXCEPT when ________ .
(Multiple Choice)
4.8/5  (35)
(35)
You find a suspicious connection from a problematic host. You decide that you want to block everything from that whole network, not just the problematic host. You want to block this for an hour while you investigate further, but you do not want to add any rules to the Rule Base. How do you achieve this?
(Multiple Choice)
4.8/5  (36)
(36)
Which of the following is NOT an option to calculate the traffic direction?
(Multiple Choice)
4.7/5  (33)
(33)
The command __________ provides the most complete restoration of a R80 configuration.
(Multiple Choice)
4.8/5  (30)
(30)
In the Check Point three-tiered architecture, which of the following is NOT a function of the Security Management Server?
(Multiple Choice)
5.0/5  (31)
(31)
Which option would allow you to make a backup copy of the OS and Check Point configuration, without stopping Check Point processes?
(Multiple Choice)
4.8/5  (38)
(38)
Which of the following statements accurately describes the command snapshot ?
(Multiple Choice)
4.8/5  (43)
(43)
Fill in the blank: The _________ collects logs and sends them to the _________ .
(Multiple Choice)
4.9/5  (33)
(33)
Choose the Best place to find a Security Management Server backup file named backup_fw , on a Check Point Appliance.
(Multiple Choice)
4.9/5  (34)
(34)
The most important part of a site-to-site VPN deployment is the ________ .
(Multiple Choice)
4.8/5  (36)
(36)
What is the BEST command to view configuration details of all interfaces in Gaia CLISH?
(Multiple Choice)
4.9/5  (39)
(39)
Which of the following is NOT a valid deployment option for R80?
(Multiple Choice)
4.8/5  (35)
(35)
A High Availability deployment is referred to as a ______ cluster and a Load Sharing deployment is referred to as a ________ cluster.
(Multiple Choice)
4.8/5  (33)
(33)
What CLI utility allows an administrator to capture traffic along the firewall inspection chain?
(Multiple Choice)
4.8/5  (36)
(36)
A client has created a new Gateway object that will be managed at a remote location. When the client attempts to install the Security Policy to the new Gateway object, the object does not appear in the Install On check box. What should you look for?
(Multiple Choice)
4.9/5  (27)
(27)
Fill in the blank: A _________ VPN deployment is used to provide remote users with secure access to internal corporate resources by authenticating the user through an internet browser.
(Multiple Choice)
4.7/5  (38)
(38)
Fill in the blank: A(n) _____ rule is created by an administrator and is located before the first and before last rules in the Rule Base.
(Multiple Choice)
4.8/5  (32)
(32)
Look at the following screenshot and select the BEST answer. 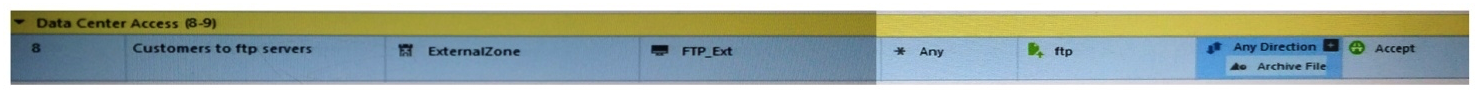
(Multiple Choice)
5.0/5  (30)
(30)
Showing 181 - 200 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)