Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
In SmartEvent, what are the different types of automatic reactions that the administrator can configure?
(Multiple Choice)
4.7/5  (32)
(32)
Using ClusterXL, what statement is true about the Sticky Decision Function?
(Multiple Choice)
4.8/5  (36)
(36)
You installed Security Management Server on a computer using GAiA in the MegaCorp home office. You use IP address 10.1.1.1. You also installed the Security Gateway on a second GAiA computer, which you plan to ship to another Administrator at a MegaCorp hub office. What is the correct order for pushing SIC certificates to the Gateway before shipping it? 1. Run cpconfig on the Gateway, select Secure Internal Communication , enter the activation key, and reconfirm. 2. Initialize Internal Certificate Authority (ICA) on the Security Management Server. 3. Configure the Gateway object with the host name and IP addresses for the remote site. 4. Click the Communication button in the Gateway object's General screen, enter the activation key, and click Initialize and OK . 5. Install the Security Policy.
(Multiple Choice)
4.8/5  (36)
(36)
What are the three deployment options available for a security gateway?
(Multiple Choice)
4.9/5  (42)
(42)
An administrator is creating an IPsec site-to-site VPN between his corporate office and branch office. Both offices are protected by Check Point Security Gateway managed by the same Security Management Server. While configuring the VPN community to specify the pre-shared secret, the administrator found that the check box to enable pre-shared secret is shared and cannot be enabled. Why does it not allow him to specify the pre-shared secret?
(Multiple Choice)
4.8/5  (34)
(34)
Which Check Point software blade provides protection from zero-day and undiscovered threats?
(Multiple Choice)
4.8/5  (37)
(37)
The __________ is used to obtain identification and security information about network users.
(Multiple Choice)
4.8/5  (48)
(48)
____________ is the Gaia command that turns the server off .
(Multiple Choice)
4.7/5  (31)
(31)
When using LDAP as an authentication method for Identity Awareness, the query:
(Multiple Choice)
4.8/5  (43)
(43)
Your company enforces a strict change control policy. Which of the following would be MOST effective for quickly dropping an attacker's specific active connection?
(Multiple Choice)
4.7/5  (25)
(25)
Fill in the blank: The command __________ provides the most complete restoration of a R80 configuration.
(Multiple Choice)
4.7/5  (39)
(39)
Review the rules. Assume domain UDP is enabled in the implied rules. 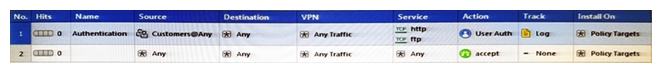 What happens when a user from the internal network tries to browse to the internet using HTTP? The user:
What happens when a user from the internal network tries to browse to the internet using HTTP? The user:
(Multiple Choice)
4.7/5  (31)
(31)
When using GAiA, it might be necessary to temporarily change the MAC address of the interface eth 0 to 00:0C:29:12:34:56 . After restarting the network the old MAC address should be active. How do you configure this change?
(Multiple Choice)
4.7/5  (39)
(39)
Which of the completed statements is NOT true? The WebUI can be used to manage user accounts and:
(Multiple Choice)
4.9/5  (29)
(29)
VPN gateways must authenticate to each other prior to exchanging information. What are the two types of credentials used for authentication?
(Multiple Choice)
4.9/5  (26)
(26)
The default method for destination NAT is _____________, where NAT occurs on the inbound interface closest to the client.
(Multiple Choice)
4.8/5  (36)
(36)
The Administrator wishes to update IPS protections from SmartConsole by clicking on the option " Update Now " under the Updates tab in Threat Tools. Which device requires internet access for the update to work?
(Multiple Choice)
4.9/5  (37)
(37)
Which pre-defined Permission Profile should be assigned to an administrator that requires full access to audit all configurations without modifying them?
(Multiple Choice)
5.0/5  (45)
(45)
Showing 141 - 160 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)