Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
Fill in the blank: Once a license is activated, a ________ should be installed.
(Multiple Choice)
4.7/5  (43)
(43)
Which method below is NOT one of the ways to communicate using the Management API's?
(Multiple Choice)
5.0/5  (37)
(37)
Which of the following is NOT a component of a Distinguished Name?
(Multiple Choice)
4.8/5  (33)
(33)
What is the most recommended installation method for Check Point appliances?
(Multiple Choice)
4.9/5  (33)
(33)
When defining QoS global properties, which option below is not valid?
(Multiple Choice)
4.8/5  (40)
(40)
When connected to the Check Point R80 Management Server using the SmartConsole the first administrator to connect has a lock on:
(Multiple Choice)
4.8/5  (36)
(36)
Which one of the following is the preferred licensing model? Choose the BEST answer.
(Multiple Choice)
4.9/5  (44)
(44)
True or False: In R80, more than one administrator can login to the Security Management Server with write permission at the same time.
(Multiple Choice)
4.9/5  (47)
(47)
Which Threat Prevention Profile is not included by default in R80 Management?
(Multiple Choice)
4.8/5  (38)
(38)
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the "Select additional profile that will be able edit this layer" you do not see anything. What is the most likely cause of this problem? 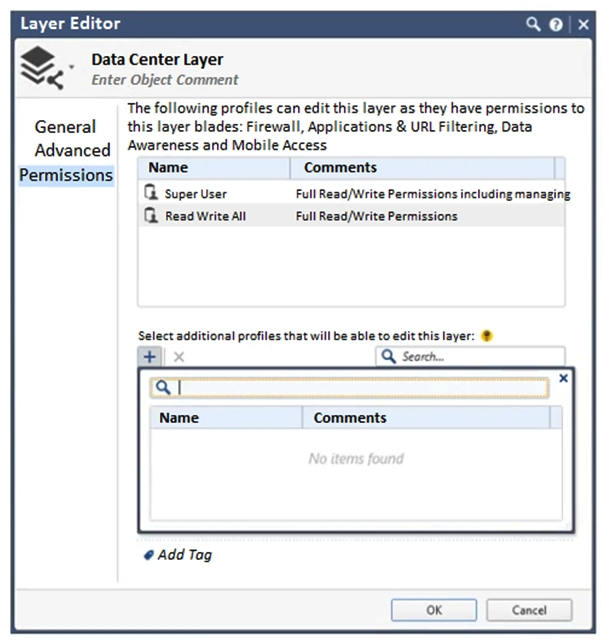
(Multiple Choice)
4.9/5  (40)
(40)
Alpha Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in Alpha Corp. 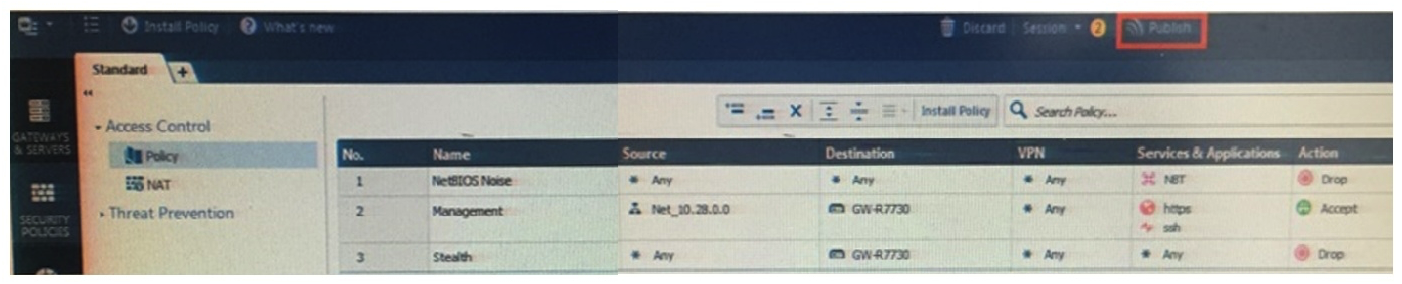 How will you describe the new " Publish " button in R80 Management Console?
How will you describe the new " Publish " button in R80 Management Console?
(Multiple Choice)
4.8/5  (34)
(34)
A Check Point software license consists of a _______ and _______ .
(Multiple Choice)
5.0/5  (43)
(43)
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19. John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his desktop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server. To make this scenario work, the IT administrator: 1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy. 2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location. 3) Changes from static IP address to DHCP for the client PC. What should John request when he cannot access the web server from his laptop?
(Multiple Choice)
4.8/5  (29)
(29)
The _________ collects logs and sends them to the _________ .
(Multiple Choice)
5.0/5  (36)
(36)
Packet acceleration (SecureXL) identifies connections by several attributes. Which of the attributes is NOT used for identifying connection?
(Multiple Choice)
4.9/5  (42)
(42)
Fill in the blanks: In the Network policy layer, the default action for the Implied last rule is ________ all traffic. However, in the Application Control policy layer, the default action is ________ all traffic.
(Multiple Choice)
4.8/5  (33)
(33)
You are working with multiple Security Gateways enforcing an extensive number of rules. To simplify security administration, which action would you choose?
(Multiple Choice)
4.8/5  (26)
(26)
Which of the following is NOT an option for internal network definition of Anti-spoofing?
(Multiple Choice)
4.9/5  (43)
(43)
Showing 101 - 120 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)