Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
Fill in the blanks: A security Policy is created in _________ , stored in the _________ , and Distributed to the various __________ .
(Multiple Choice)
4.8/5  (31)
(31)
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base. 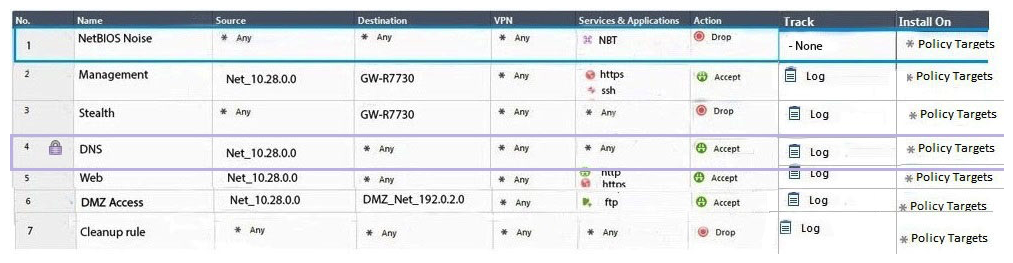 What is the possible explanation for this?
What is the possible explanation for this?
(Multiple Choice)
4.9/5  (33)
(33)
True or False: The destination server for Security Gateway logs depends on a Security Management Server configuration.
(Multiple Choice)
4.8/5  (37)
(37)
Fill in the blank: The R80 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows them as prioritized security events.
(Multiple Choice)
4.8/5  (35)
(35)
You work as a security administrator for a large company. The CSO of your company has attended a security conference where he has learned how hackers constantly modify their strategies and techniques to evade detection and reach corporate resources. He wants to make sure that his company has the right protections in place. Check Point has been selected for the security vendor. Which Check Point product protects BEST against malware and zero-day attacks while ensuring quick delivery of safe content to your users?
(Multiple Choice)
4.8/5  (40)
(40)
An identity server uses a ___________ for user authentication.
(Multiple Choice)
4.8/5  (39)
(39)
When a Security Gateways sends its logs to an IP address other than its own, which deployment option is installed?
(Multiple Choice)
4.8/5  (33)
(33)
Which type of Endpoint Identity Agent includes packet tagging and computer authentication?
(Multiple Choice)
4.8/5  (35)
(35)
Which Check Point supported authentication scheme typically requires a user to possess a token?
(Multiple Choice)
4.8/5  (33)
(33)
In a Distributed Environment, a Central License can be installed via CLI on a Security Gateway
(Multiple Choice)
4.9/5  (41)
(41)
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the "Select additional profile that will be able edit this layer" you do not see anything. What is the most likely cause of this problem? Select the BEST answer. 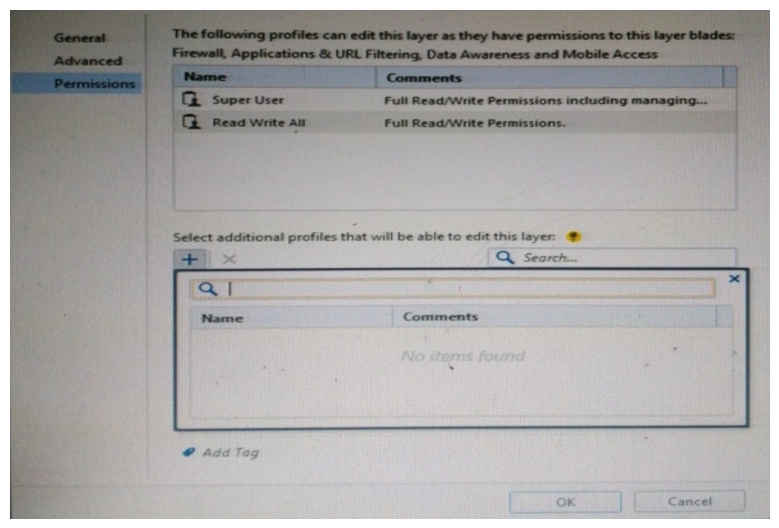
(Multiple Choice)
4.9/5  (40)
(40)
Which option will match a connection regardless of its association with a VPN community?
(Multiple Choice)
4.9/5  (36)
(36)
In order to modify Security Policies the administrator can use which of the following tools? Select the BEST answer.
(Multiple Choice)
4.9/5  (37)
(37)
Fill in the blank: Back up and restores can be accomplished through_________.
(Multiple Choice)
4.8/5  (30)
(30)
Which of the following commands can be used to remove site-to-site IPSEC Security Associations (SA)?
(Multiple Choice)
4.8/5  (33)
(33)
If there is an Accept Implied Policy set to "First", what is the reason Jorge cannot see any logs?
(Multiple Choice)
4.7/5  (38)
(38)
Showing 581 - 600 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)