Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
Which Threat Tool within SmartConsole provides a list of trusted files to the administrator so they can specify to the Threat Prevention blade that these files do not need to be scanned or analyzed?
(Multiple Choice)
4.9/5  (41)
(41)
In order to install a license, it must first be added to the ____________.
(Multiple Choice)
4.8/5  (36)
(36)
What protocol is specifically used for clustered environments?
(Multiple Choice)
4.8/5  (33)
(33)
When tunnel test packets no longer invoke a response, Tunnel and User Monitoring displays _____________ for the given VPN tunnel.
(Multiple Choice)
4.8/5  (39)
(39)
Which of the following situations would not require a new license to be generated and installed?
(Multiple Choice)
4.9/5  (45)
(45)
What are the three essential components of the Check Point Security Management Architecture?
(Multiple Choice)
4.8/5  (36)
(36)
Fill in the blanks: A ____ license requires an administrator to designate a gateway for attachment whereas a _____ license is automatically attached to a Security Gateway.
(Multiple Choice)
4.8/5  (37)
(37)
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base. To make this scenario work, the IT administrator must: 1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources. 2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected. 3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action. 4) Install policy. Ms McHanry tries to access the resource but is unable. What should she do?
(Multiple Choice)
4.7/5  (46)
(46)
Fill in the blank: Each cluster, at a minimum, should have at least ___________ interfaces.
(Multiple Choice)
4.8/5  (34)
(34)
You are the administrator for Alpha Corp. You have logged into your R80 Management server. You are making some changes in the Rule Base and notice that rule No.6 has a pencil icon next to it. 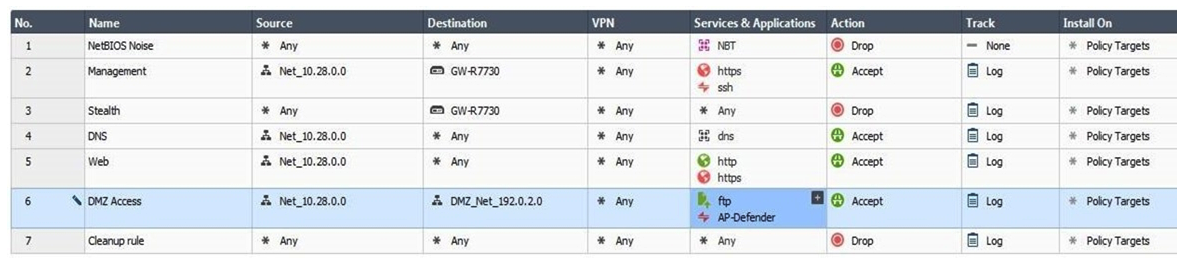 What does this mean?
What does this mean?
(Multiple Choice)
4.8/5  (43)
(43)
Look at the screenshot below. What CLISH command provides this output? 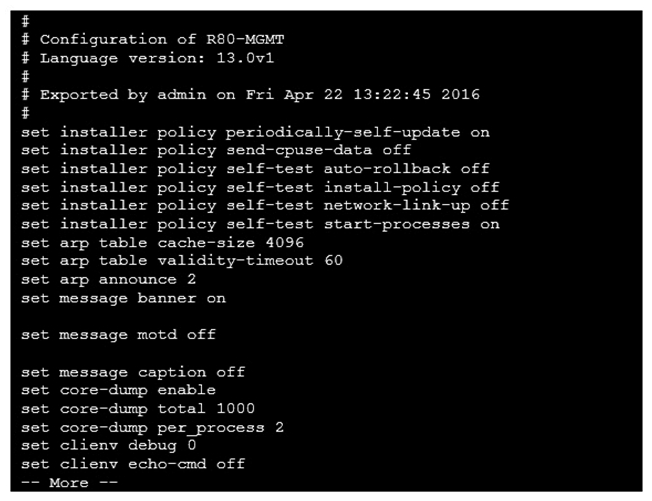
(Multiple Choice)
4.8/5  (32)
(32)
The Firewall kernel is replicated multiple times, therefore:
(Multiple Choice)
4.8/5  (47)
(47)
View the rule below. What does the lock-symbol in the left column mean? 
(Multiple Choice)
4.9/5  (32)
(32)
When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
(Multiple Choice)
4.8/5  (35)
(35)
Can multiple administrators connect to a Security Management Server at the same time?
(Multiple Choice)
4.8/5  (37)
(37)
You are about to test some rule and object changes suggested in an R77 news group. Which backup solution should you use to ensure the easiest restoration of your Security Policy to its previous configuration after testing the changes?
(Multiple Choice)
4.8/5  (32)
(32)
Showing 641 - 660 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)