Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
When using Monitored circuit VRRP, what is a priority delta?
(Multiple Choice)
4.9/5  (32)
(32)
Fill in the blank: Once a certificate is revoked from the Security GateWay by the Security Management Server, the certificate information is _______.
(Multiple Choice)
4.8/5  (48)
(48)
Where would an administrator enable Implied Rules logging?
(Multiple Choice)
4.9/5  (36)
(36)
You are going to perform a major upgrade. Which back up solution should you use to ensure your database can be restored on that device?
(Multiple Choice)
4.7/5  (44)
(44)
Which of the following is used to initially create trust between a Gateway and Security Management Server?
(Multiple Choice)
4.8/5  (40)
(40)
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators?
(Multiple Choice)
4.8/5  (42)
(42)
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80 management platform. You are presenting an in-house R80 Management to the other administrators in ABC Corp. 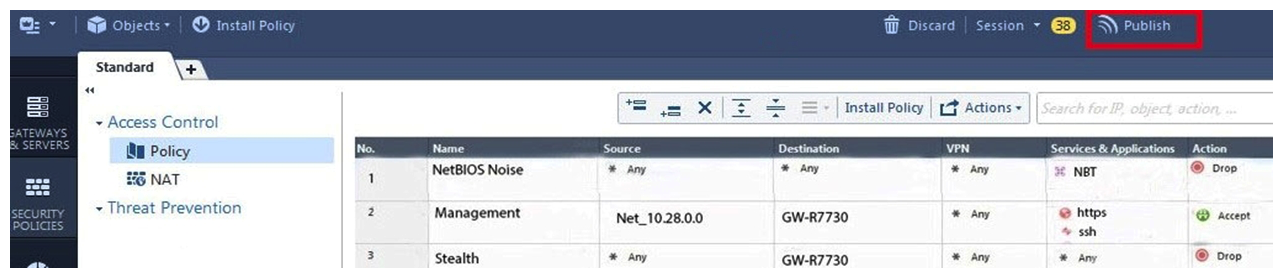 How will you describe the new " Publish " button in R80 Management Console?
How will you describe the new " Publish " button in R80 Management Console?
(Multiple Choice)
4.8/5  (39)
(39)
Which information is included in the "Full Log" tracking option, but is not included in the "Log" tracking option?
(Multiple Choice)
4.7/5  (32)
(32)
An administrator wishes to enable Identity Awareness on the Check Point firewalls. However, they allow users to use company issued or personal laptops. Since the administrator cannot manage the personal laptops, which of the following methods would BEST suit this company?
(Multiple Choice)
4.8/5  (41)
(41)
What is the Transport layer of the TCP/IP model responsible for?
(Multiple Choice)
4.9/5  (34)
(34)
There are two R80.X0 Security Gateways in the Firewall Cluster. They are named FW_A and FW_B. The cluster is configured to work as HA (High availability) with default cluster configuration. FW_A is configured to have higher priority than FW_B. FW_A was active and processing the traffic in the morning. FW_B was standby. Around 1100 am, its interfaces went down and this caused a failover. FW_B became active. After an hour, FW_A's interface issues were resolved and it became operational. When it re-joins the cluster, will it become active automatically?
(Multiple Choice)
4.8/5  (32)
(32)
Choose the BEST describes the Policy Layer Traffic Inspection?
(Multiple Choice)
4.9/5  (37)
(37)
Fill in the blank: With the User Directory Software Blade, you can create R80 user definitions on a(an) ___________ Server.
(Multiple Choice)
4.8/5  (44)
(44)
Which VPN routing option uses VPN routing for every connection a satellite gateway handles?
(Multiple Choice)
4.9/5  (38)
(38)
SandBlast has several functional components that work together to ensure that attacks are prevented in real-time. Which the following is NOT part of the SandBlast component?
(Multiple Choice)
4.8/5  (40)
(40)
Which of the following is NOT a type of Endpoint Identity Agent?
(Multiple Choice)
4.7/5  (48)
(48)
Showing 621 - 640 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)