Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
When an encrypted packet is decrypted, where does this happen?
(Multiple Choice)
4.9/5  (37)
(37)
According to Check Point Best Practice, when adding a 3 rd party gateway to a Check Point security solution what object SHOULD be added? A(n):
(Multiple Choice)
4.8/5  (39)
(39)
Fill in the blank: To create policy for traffic to or from a particular location, use the _____________.
(Multiple Choice)
4.7/5  (31)
(31)
Which of the following Windows Security Events will NOT map a username to an IP address in Identity Awareness?
(Multiple Choice)
4.8/5  (38)
(38)
All R77 Security Servers can perform authentication with the exception of one. Which of the Security Servers can NOT perform authentication?
(Multiple Choice)
4.7/5  (39)
(39)
Which of the below is the MOST correct process to reset SIC from SmartDashboard?
(Multiple Choice)
4.9/5  (46)
(46)
Where can you trigger a failover of the cluster members? 1. Log in to Security Gateway CLI and run command clusterXL_admin down . 2. In SmartView Monitor right-click the Security Gateway member and select Cluster member stop 3. Log into Security Gateway CLI and run command cphaprob down
(Multiple Choice)
4.7/5  (37)
(37)
Which two of these Check Point Protocols are used by _____ ?
(Multiple Choice)
4.8/5  (42)
(42)
Where does the security administrator activate Identity Awareness within SmartDashboard?
(Multiple Choice)
4.8/5  (33)
(33)
It is Best Practice to have a _____ rule at the end of each policy layer.
(Multiple Choice)
5.0/5  (35)
(35)
Fill in the blank: The ________ feature allows administrators to share a policy with other policy packages.
(Multiple Choice)
4.7/5  (35)
(35)
Administrator Kofi has just made some changes on his Management Server and then clicks on the Publish button in SmartConsole but then gets the error message shown in the screenshot below. Where can the administrator check for more information on these errors? 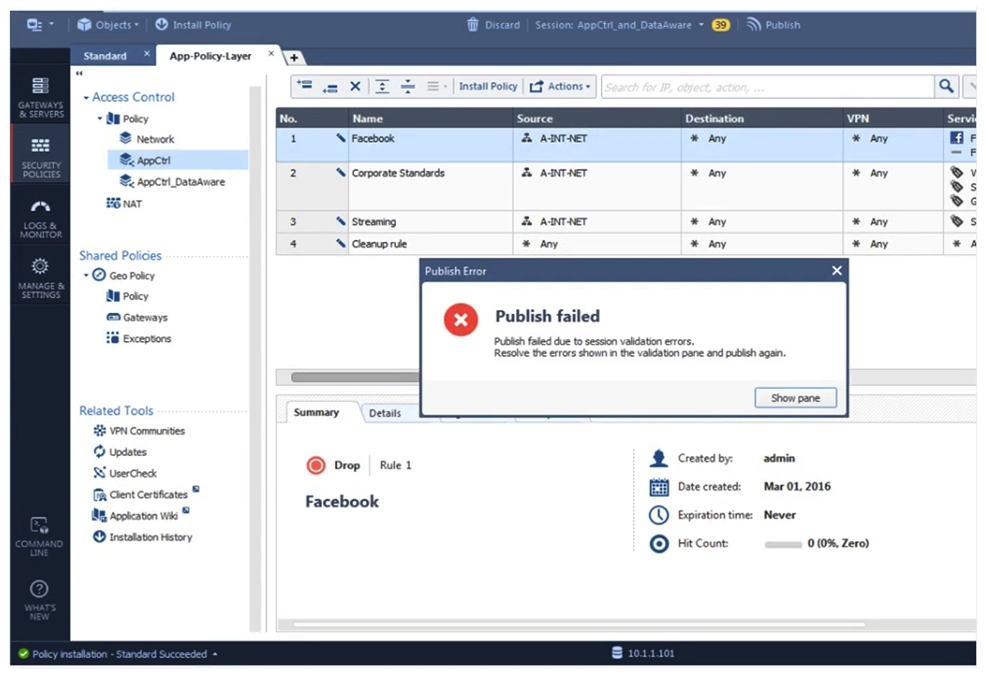
(Multiple Choice)
4.8/5  (41)
(41)
While in SmartView Tracker, Brady has noticed some very odd network traffic that he thinks could be an intrusion. He decides to block the traffic for 60 minutes, but cannot remember all the steps. What is the correct order of steps needed to set up the block? 1) Select Active Mode tab in SmartView Tracker. 2) Select Tools > Block Intruder . 3) Select Log Viewing 4) Set Blocking Timeout value to 60 minutes. 5) Highlight connection that should be blocked.
(Multiple Choice)
4.9/5  (41)
(41)
You are conducting a security audit. While reviewing configuration files and logs, you notice logs accepting POP3 traffic, but you do not see a rule allowing POP3 traffic in the Rule Base. Which of the following is the most likely cause?
(Multiple Choice)
4.9/5  (31)
(31)
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, gateway policy permits access only from Join's desktop which is assigned an IP address 10.0.0.19 via DHCP. John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but the limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop. He wants to move around the organization and continue to have access to the HR Web Server. To make this scenario work, the IT administrator: 1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources. 2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location. John plugged in his laptop to the network on a different network segment and he is not able to connect. How does he solve this problem?
(Multiple Choice)
4.9/5  (40)
(40)
You have discovered suspicious activity in your network. What is the BEST immediate action to take?
(Multiple Choice)
4.8/5  (36)
(36)
What does it mean if Bob gets this result on an object search? Refer to the image below. Choose the BEST answer. 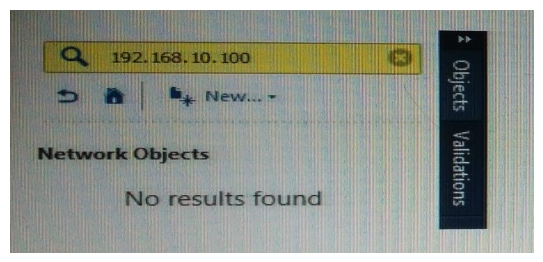
(Multiple Choice)
4.8/5  (34)
(34)
What is the most complete definition of the difference between the Install Policy button on the SmartConsole's tab, and the Install Policy button within a specific policy?
(Multiple Choice)
4.9/5  (39)
(39)
Which Threat Prevention Software Blade provides protection from malicious software that can infect your network computers?
(Multiple Choice)
4.9/5  (43)
(43)
Showing 401 - 420 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)