Exam 2: Check Point Certified Security Administrator (CCSA R80)
Exam 1: Check Point Certified Security Principles Associate (CCSPA)60 Questions
Exam 2: Check Point Certified Security Administrator (CCSA R80)676 Questions
Exam 3: Check Point Certified Security Expert - R80340 Questions
Select questions type
What port is used for delivering logs from the gateway to the management server?
(Multiple Choice)
4.9/5  (40)
(40)
The tool _______ generates a R80 Security Gateway configuration report.
(Multiple Choice)
4.8/5  (31)
(31)
Review the following screenshot and select the BEST answer. 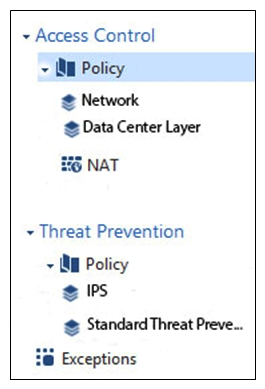
(Multiple Choice)
4.7/5  (38)
(38)
AdminA and AdminB are both logged in on SmartConsole. What does it mean if AdminB sees a lock icon on a rule? Choose the BEST answer.
(Multiple Choice)
4.8/5  (34)
(34)
You have two rules, ten users, and two user groups in a Security Policy. You create database version 1 for this configuration. You then delete two existing users and add a new user group. You modify one rule and add two new rules to the Rule Base. You save the Security Policy and create database version 2. After a while, you decide to roll back to version 1 to use the Rule Base, but you want to keep your user database. How can you do this?
(Multiple Choice)
4.9/5  (33)
(33)
Fill in the blank: When LDAP is integrated with Check Point Security Management, it is then referred to as _______
(Multiple Choice)
4.7/5  (41)
(41)
AdminA and AdminB are both logged in on SmartConsole. What does it mean if AdminB sees a lock icon on a rule?
(Multiple Choice)
4.7/5  (40)
(40)
Fill in the blanks: A High Availability deployment is referred to as a ______ cluster and a Load Sharing deployment is referred to as a ________ cluster.
(Multiple Choice)
4.8/5  (36)
(36)
VPN gateways authenticate using ___________ and ___________ .
(Multiple Choice)
4.8/5  (34)
(34)
Fill in the blank: When a policy package is installed, ________ are also distributed to the target installation Security Gateways.
(Multiple Choice)
4.9/5  (43)
(43)
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
(Multiple Choice)
4.9/5  (31)
(31)
In SmartConsole, objects are used to represent physical and virtual network components and also some logical components. These objects are divided into several categories. Which of the following is NOT an objects category?
(Multiple Choice)
4.8/5  (39)
(39)
Harriet wants to protect sensitive information from intentional loss when users browse to a specific URL: https://personal.mymail.com, which blade will she enable to achieve her goal?
(Multiple Choice)
4.9/5  (34)
(34)
What are the three conflict resolution rules in the Threat Prevention Policy Layers?
(Multiple Choice)
4.9/5  (36)
(36)
When you upload a package or license to the appropriate repository in SmartUpdate, where is the package or license stored
(Multiple Choice)
4.7/5  (35)
(35)
Fill in the blank: The R80 feature ________ permits blocking specific IP addresses for a specified time period.
(Multiple Choice)
4.8/5  (37)
(37)
You believe Phase 2 negotiations are failing while you are attempting to configure a site-to-site VPN with one of your firm's business partners. Which SmartConsole application should you use to confirm your suspicious?
(Multiple Choice)
4.9/5  (41)
(41)
Provide very wide coverage for all products and protocols, with noticeable performance impact. 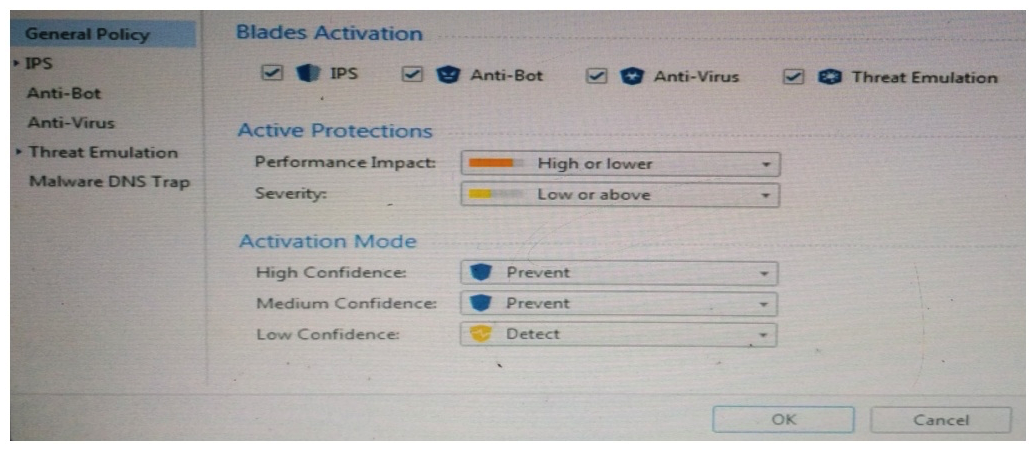 How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
How could you tune the profile in order to lower the CPU load still maintaining security at good level? Select the BEST answer.
(Multiple Choice)
4.9/5  (41)
(41)
Showing 481 - 500 of 676
Filters
- Essay(0)
- Multiple Choice(0)
- Short Answer(0)
- True False(0)
- Matching(0)